Reading Time: 2 min read
This is strictly educational. In no way, shape, or form does this writeup promote or condone unauthorized access, exploitation, or disruption of live systems. All analysis was performed passively and within legal boundaries. Always get explicit permission before engaging in any form of testing.
So a family member received a phishing SMS that looked as follows:
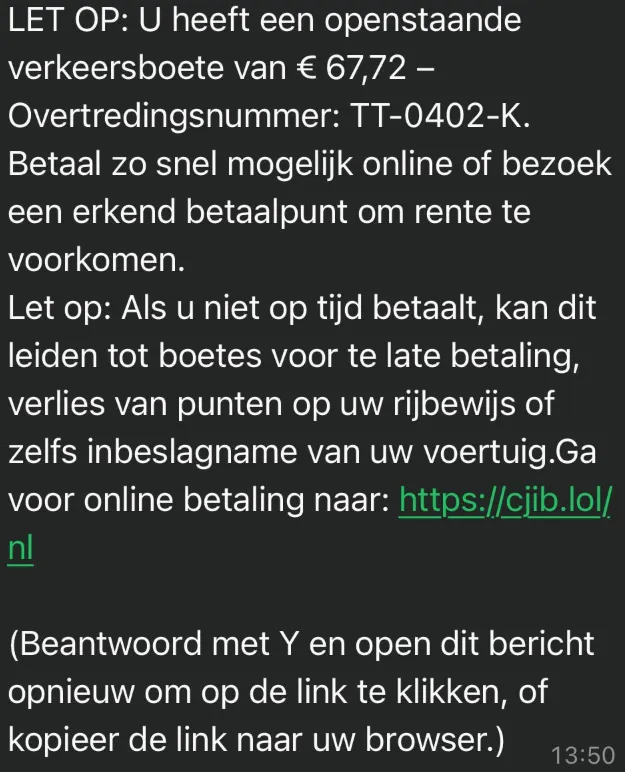
And since I had nothing to do anyways I decided to investigate it and potentially learn something new.
whatweb
Section titled “whatweb”From a sandboxed freshly installed VM I started off by running whatweb to find out what IP address this site belonged to:
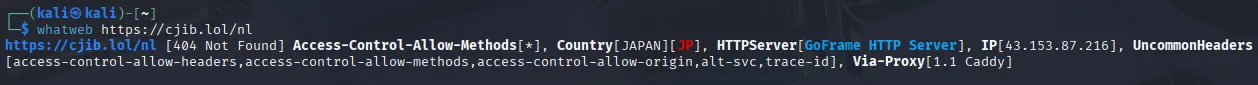
This showed me the IP address amongst other things, I went on to check out more about this IP address.
whois.domaintools.com
Section titled “whois.domaintools.com”On this website I used the IP address 43.153.87.216 as input and found out the following:
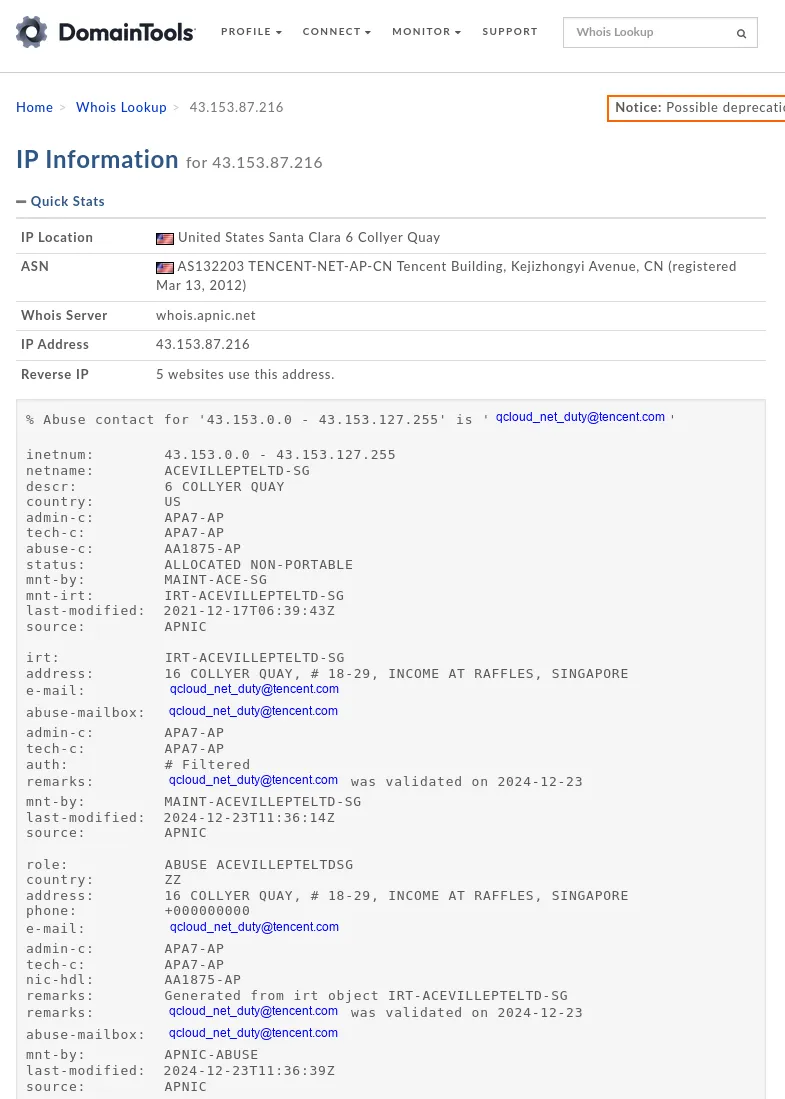
All sorts of alarm bells started ringing as none of this made sense.
Not before long however I enumerate further using gobuster.
gobuster - directory enum
Section titled “gobuster - directory enum”I went on to enumerate the website further, I was interested what other scams they had running, especially since shortly after scanning they took down the /nl endpoint:
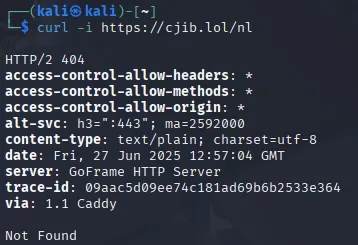
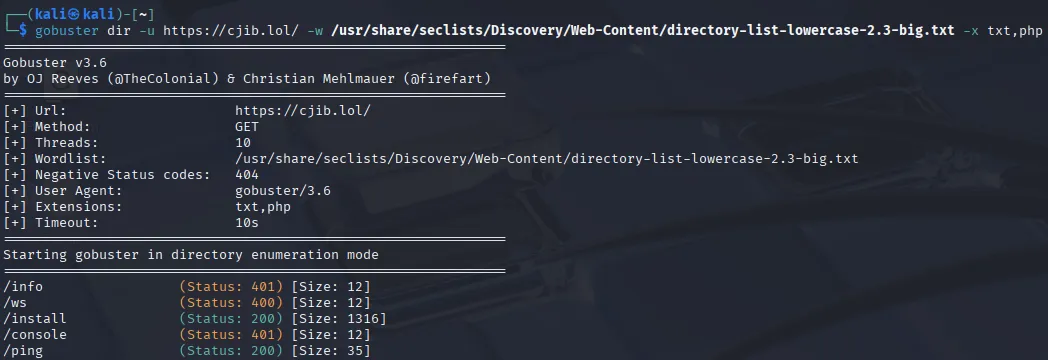
It found some other interesting endpoints on which I used curl to check them out.
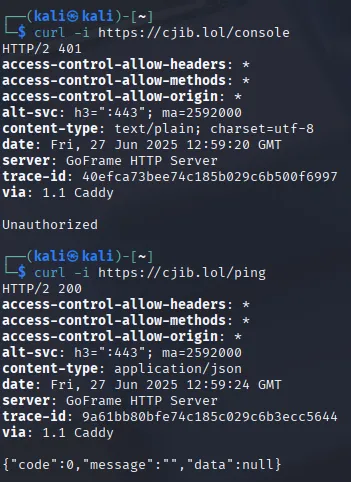
This was already quite interesting, but even more so was the following:
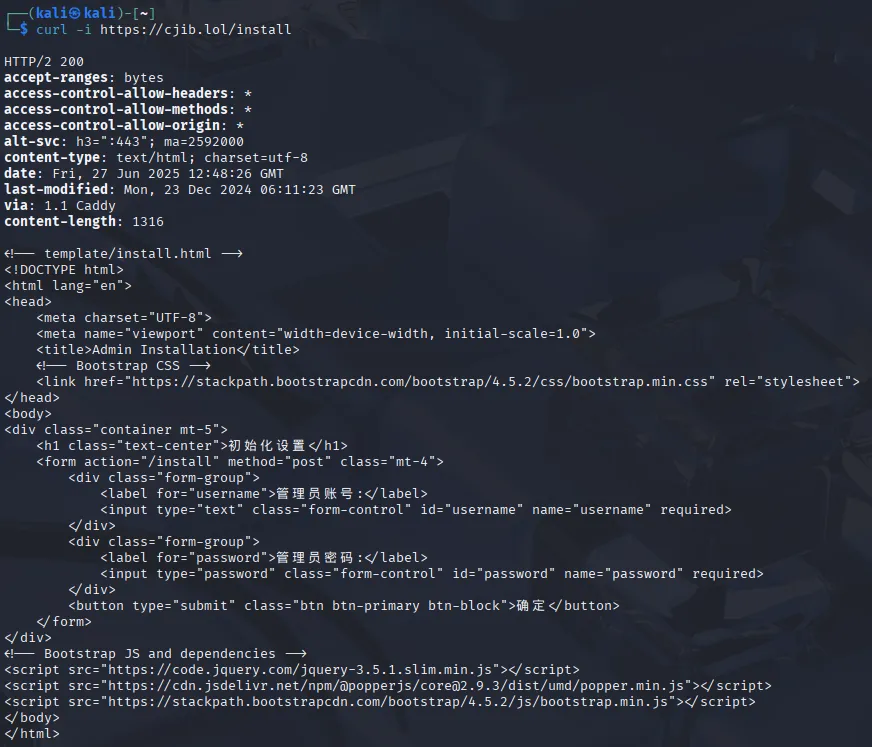
Viewing the page locally
Section titled “Viewing the page locally”Since I was quite curious I went ahead and used the following command to put this into a file and view it from localhost:
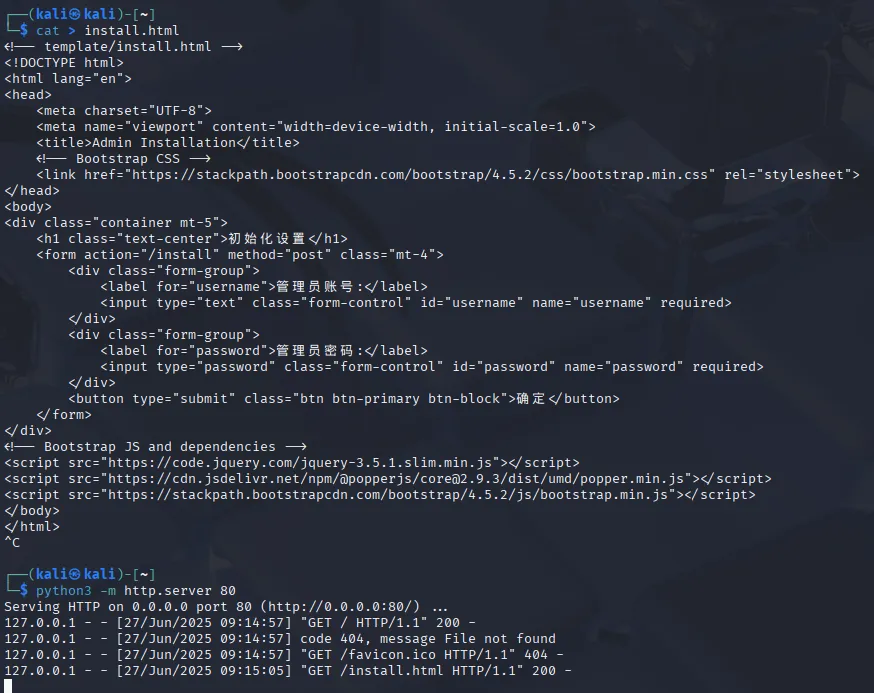
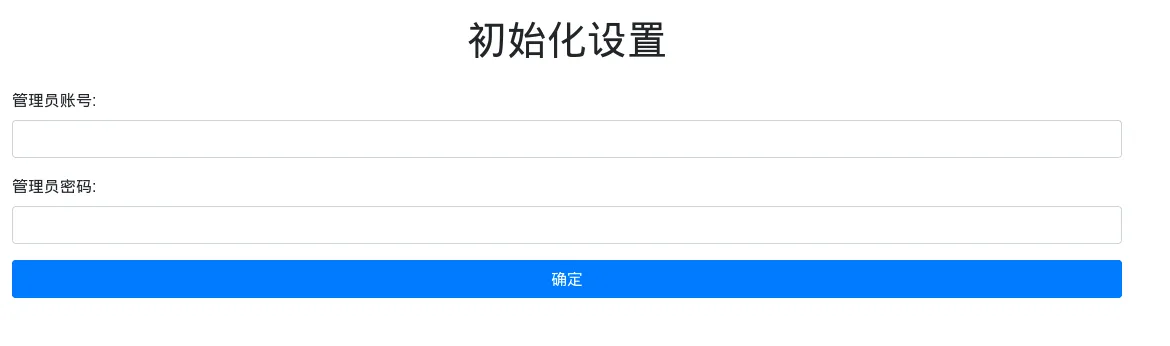
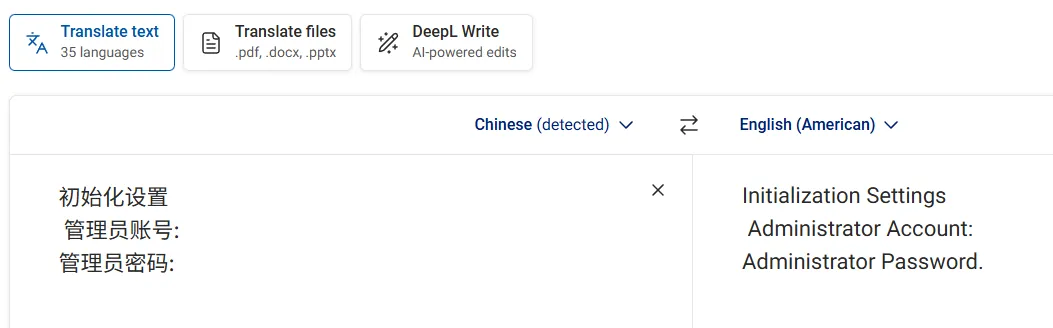
Via deepl I translated the words:
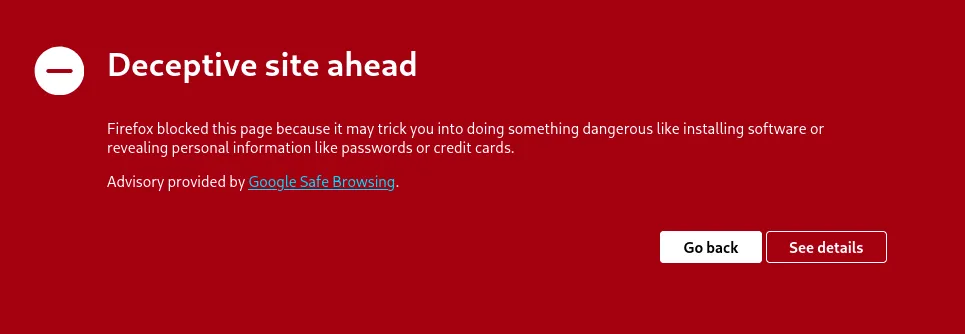
After just a short while I tried visiting the original website and sure enough the site was already flagged:
This concludes my short reverse engineering of this Phishing website, I managed to actually learn something from this by analysing how real attackers work.
